How can you know if someone is spying on your phone? Telltale signs include phone overheating or randomly restarting, drained battery, data usage spikes, and more. Let’s take a closer look at 16 signs that indicate spyware on your phone and how to prevent it.
16 signs that someone is spying on your phone
Here are the most common warning signs that your phone is being mirrored, tracked, tapped, or monitored by spyware software:
1. Increased data usage
You probably have a ballpark figure of your monthly mobile data usage. If someone is spying on your phone, they may be using your cellular network to download any data collected on you (it’s either that or Wi-Fi). Look out for strange spikes, as they’ll likely be a sign of spy apps.
Not tracking your data usage? You should start paying attention right away. While sophisticated versions can be quite discrete, some spyware takes up loads of data.
How to check data usage on an iPhone
Here’s how you can check data usage statistics on an iPhone or iPad:
- Open your phone Settings.
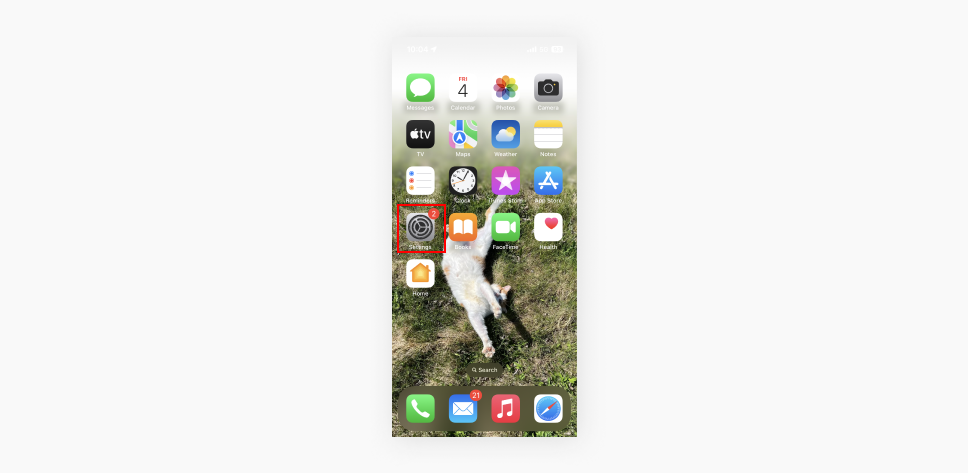
- Choose Cellular or Mobile Data.
- Scroll down to find detailed data usage information about your iOS apps.
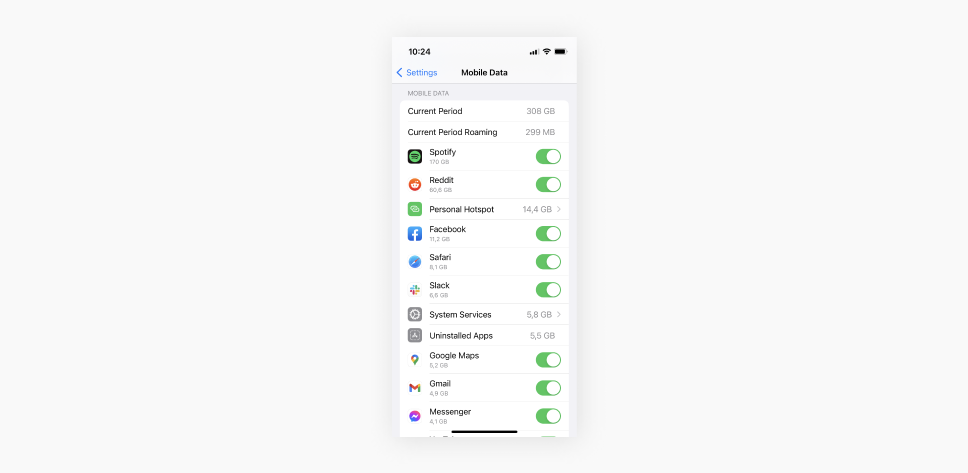
You’ll get the total amount of data used and how much each app consumes, so you can spot suspicious activity by looking for spikes in mobile data usage. Periodically press Reset Statistics at the bottom of the data settings screen to make tracking easier.
How to check data usage on Android
The process for checking data usage may be slightly different depending on the Android device you’re using, but it’ll be the same or similar to this:
- Open the Settings app.
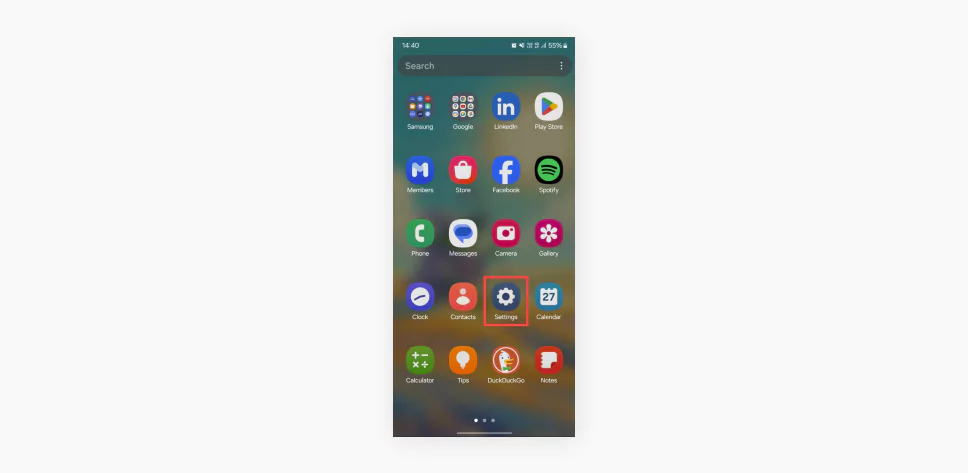
- Find and open your Network and internet settings.
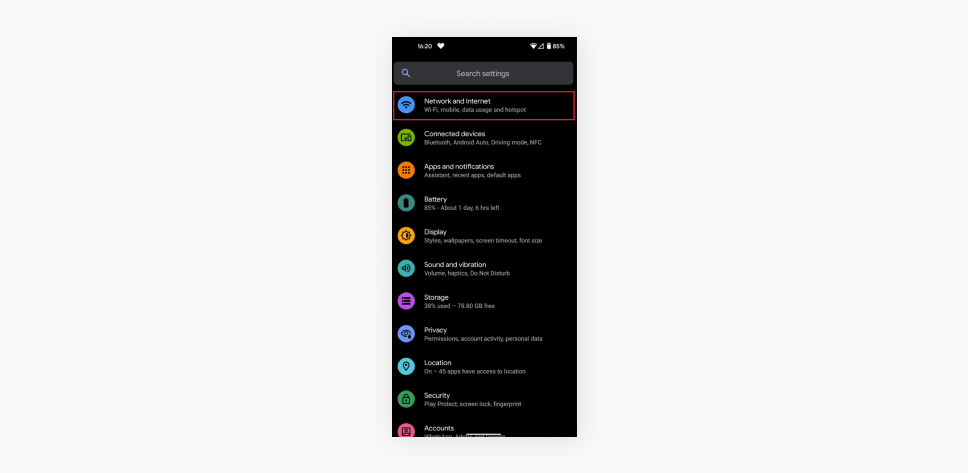
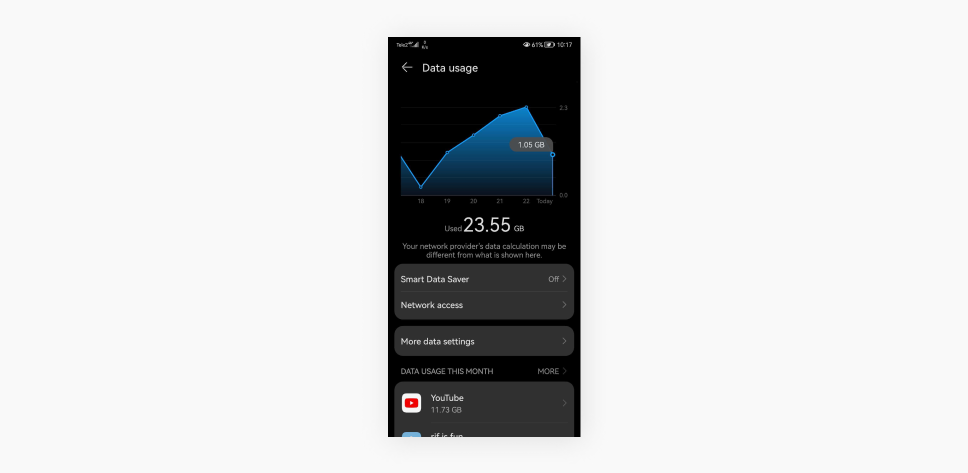
- Click on the App data usage section.
Android settings show the total amount of data used and the data used by each app during a given period, allowing you to check for any unusual activity.
2. Unusual activity on linked accounts (Google, Facebook, iCloud)
Unusual logins and other activity on platforms like Google and Facebook may point to a breach in your defense.
For Apple devices, security flaws within the iCloud system may allow bad actors to access your information through spyware. They can even access your other accounts if they’re linked to your iCloud and your login information is stored there.
Suspicious activity on any of your accounts is a cause for concern and shouldn’t be taken lightly. After all, chances are that hackers have taken over your device.
If you suspect that something like your Facebook has been hacked, the first step is to change your password and review your account’s login activity.
3. Weird pop-ups
If you’re receiving push notifications for fake virus alerts, it may be a sign your mobile phone is infected with adware, an intrusive kind of malware.
We’re not talking about cookie messages or windows asking you to disable your ad blocker. While annoying, those alone are common enough and aren’t red flags. Instead, watch out for totally unfamiliar pop-ups that look like they come from an untrusted source.
In the best case, these are just obnoxious, but they can be part of a phishing attempt in the worst-case scenario. Regardless, they should be monitored as they likely pose a threat to your security.
4. Slower phone performance
While it’s expected for things to get a little sluggish on older phones, slowdowns should always be a cause for concern. Spy apps use more than their fair share of processing power to track your phone, and your speed often takes a hit, even on a newer device.
However, poor speeds brought on by spying are a tough nut to crack. Malicious apps typically won’t instantly bring your device to a standstill — it can take weeks or even months for any noticeable changes to emerge.
Another issue lies in finding the cause of any inferior performance. Did you actually install spyware, or is your phone just getting slower with age? You’ll probably need to do some more digging to get to the bottom of any problems you face.
Try safe mode to figure out why your device is running slow.
5. Random reboots
Your phone shouldn’t reboot without your say-so or a major error of some kind. Frequent unexpected reboots may be a sign that your phone has been hacked.
You might think these reboots could be a sign that your device is on its last legs, but this is rarely the case. It’s more likely that a hacker has managed to gain remote access to your device with admin rights, and reboots might just be necessary to achieve whatever they’re doing to your phone.
6. Longer or impeded shutdowns
This one can be hard to notice if you’re like me and never shut off your phone. But try it out, and if your phone is taking a long time to turn off — or simply refuses to shut down — it may be due to interference from spy apps.
Much like a computer, your phone shuts down all active processes before turning itself off. Spyware is often designed to get in the way of shutdown processes so hackers don’t lose direct access to your device.
If you notice shutdowns taking a while, give your phone a search — the culprit may be a suspicious app.
7. Blocked emails
Are your emails to friends or coworkers getting blocked by their firewalls? This could indicate that malicious software is operating on your phone and infecting your messages.
It’s also possible that hackers have gained physical access to your email account and used it to send out spam emails. As a result, your legitimate emails are also flagged as spam due to the suspicious activity coming from your account.
Either way, if there’s an issue with how your emails are delivered, it could be a sign that someone has broken into your device.
8. Random wake-ups
When you lock your mobile device and set it down, your screen should stay black until you receive a notification. But if it suddenly lights up, despite a total lack of incoming calls or messages, someone may have successfully hacked your smartphone.
A screen lighting up is usually a sign of some processes running in the background. Legitimate apps may bring it to life, but you’ll usually know about this. If your phone starts lighting up without a clear reason on a regular basis, you should start looking into possible spyware apps on your device.
9. Interference with other devices
Have you ever heard interference from nearby electronics while on a phone call? That static buzzing, clicking noise that seems to randomly come and go?
Well, you shouldn’t be hearing any of it if you’re not actually on a phone call. If that’s happening, it may be a sign of a spyware app being in use. When these listen to what’s being said around your device and send information to whoever is stalking you, they’ve been known to cause such interference.
10. Strange noises during phone calls
Modern mobile phones use advanced noise cancellation and digital connections, so you shouldn’t hear unexplained sounds like echoes, static, or distant voices.
And while classic James Bond-style wiretapping is rare, poor encryption or spyware can still cause interference. If someone is intercepting your calls — especially on apps like Zoom, WhatsApp, or FaceTime — you might notice persistent audio glitches or strange noises that don’t go away, even after restarting the call or switching networks.
If you notice these sounds again and again, your phone’s security could be compromised.
11. Weird texts
Maybe actually calling someone on your phone isn’t for you. Well, texts can show signs of someone spying on your phone, too.
If you receive strange text messages (yes, even stranger than the typical marketing spam), you may be getting control messages meant for a spy app on your phone. Clues like strange symbols, excessive typos, and weird character combos are dead giveaways.
On top of receiving strange text messages, you may notice SMS messages from your device that you don’t remember sending. Losing track of a text or two happens to the best of us, but if you consistently spot these mysterious messages, they were probably sent by bad actors who have taken over your phone.
12. Faster battery drainage
Are you scrambling to charge your phone more often than usual? Sure, new apps tend to require more battery power, but what if you haven’t installed anything recently? Spyware apps might be the culprit.
These spy apps need energy to function, just like any other piece of software. And if they’re constantly on, recording your calls or texts, they might be eating up a lot of power.
On the off chance that it’s just the battery getting old, try using it with another device to compare performance. If your smartphone doesn’t have a replaceable battery, take it to any tech support center to check your battery’s health.
13. Warm battery when idle
Warm batteries after hours of doomscrolling or mobile games are one thing, but your phone shouldn’t heat up when it’s not in use.
Of course, a single occurrence may be explained by some app that’s gone haywire. On the other hand, if you’re experiencing a scorching smartphone on the regular, something more sinister is likely at play. There’s a real possibility that you’ve got a spy app on your hands.
The reason behind it isn’t rocket science. Even when you’re not using your phone, spyware may run in the background, putting constant strain on your battery. Many suspicious apps are pretty resource-intensive, so it’s easy for them to make your phone too hot to handle.
14. Autonomous app storage permissions (for Android phones)
If you find that your Android phone allows app downloading and installation outside the Google Play Store without asking for your permission first, you might be dealing with mobile spyware.
To check if this applies to you, go through Storage permissions in your Settings. Look for any unfamiliar apps that have the ability to store data, and there’s a good chance someone is spying on your Android phone.
15. Bad screenshot quality
A keylogger is a special kind of spyware that records what you type. If one of these apps is on your phone, it can impact all sorts of things, including your ability to take screenshots.
Spyware apps can interfere with how your device functions overall, potentially leading to issues like lag and worse performance. If these problems are severe enough and your phone is struggling to run basic processes smoothly, your screenshot quality is bound to be affected.
16. Malfunctioning autocorrect
Oh, duck! Autocorrect is hit-or-miss on the best of days. That said, if it starts acting strange or works with a persistent delay, this may be the result of a keylogger at work.
Spyware apps looking to track what you’re typing often go straight to the source — your keyboard or autocorrect itself. If anything about typing suddenly feels off, you may have fallen victim to a hacker.
How to prevent spyware from infecting your phone
Spyware apps certainly sound scary, but there’s plenty you can do to stop them from ever getting on your phone. Here are a few tips on preventing your phone from being riddled with spyware:
- Use antivirus software: a reliable antivirus does more than detect spyware — it actively prevents malware from reaching your phone. Tools like Surfshark Antivirus can scan downloads, app installations, and website activity through Real-time Protection, blocking malicious software before it can harm your device.
Advanced Surfshark Antivirus features like Cloud Protect scan for unknown files in the cloud, while Anti-tamper protection stops bad actors from sabotaging your files or antivirus software. - Use a VPN (Virtual Private Network): VPNs help protect your phone from spyware by hiding your IP (Internet Protocol) address and encrypting your internet traffic. They make it harder for hackers or cybercriminals to track your online activity or steal personal data. Spyware often relies on IP tracking and unsecured connections, but a VPN keeps your browsing private.
Some VPNs offer extra features — like Surfshark VPN’s CleanWeb — that add another layer of defense. CleanWeb blocks trackers, all known ads, and access to malicious sites, preventing you from unknowingly downloading dangerous content and reducing your overall risk of infection. - Keep your phone updated: while they may come across as a minor annoyance, updates to your operating system happen for a reason. The makers of our go-to apps and platforms know their biggest security gaps, and updates tend to offer fixes for most of them. Routinely check for the newest available versions to keep your device in peak shape.
- Don’t use third parties: enabling unsupported apps on Android devices or jailbreaking iPhones (i.e., removing their software restrictions) usually makes your phone more vulnerable to exploitation. Don’t download apps from unknown sources, and stick to trusted providers in your official app store (either the Google Play Store for Android or the Apple App Store for iPhone).
- Be careful online: some common sense online can go a long way. Shady websites, sketchy URL links, and suspicious email attachments can all be dangerous. Simply put, don’t click on what you don’t know.
- Keep Bluetooth off when not in use: bluejacking is when someone sends unwanted messages or files to your phone via Bluetooth. This usually isn’t dangerous and can be done as a prank, but it can still be used to eavesdrop and plant infected files on your phone.
- Never leave your phone unattended: locking your screen and keeping your phone by your side is the safest way to keep it from being hacked. Old-school hackers may prey on careless victims who momentarily leave their phones out in public, giving them the chance to install a spying app manually when you’re not paying attention. Stay safe by having your phone with you at all times.
In sum, these steps will significantly improve your phone’s security and protect it from hacking. Remember that spyware is just one form of hacking, so check out our tips on how to know if your phone is hacked for more information.
What can you do if your phone is being spied on?
Here’s what you can do if you feel like your cell phone is compromised by spyware.
Get antivirus software
Yes, an antivirus can prevent infections, but it can even help out when you’re already being spied on.
For instance, Surfshark Antivirus lets you run On-demand scans to detect, isolate, and remove spyware. These are manual scans you can run whenever you suspect a potential threat has found its way onto your phone.
Enable 2FA on your accounts
While enabling two-factor authentication (2FA) won’t get rid of spyware, it will help protect your accounts when your phone is hacked.
The best-case scenario would be to set up 2FA in a way that requires authentication from another device. After all, if you only get a message or email on your phone to confirm a login, the person who has hacked your phone will probably be able to see this as well.
Change your passwords
Changing your passwords is another protective measure you should take if you feel like your phone has been hacked. Also, it’s a good idea to do this on another device.
Why? Hackers may be able to see everything you’re doing on your phone. In other words, if you’re using the same phone to change passwords, you might not be hiding anything from bad actors.
Remove spy software on Android manually
It’s possible that a spyware app on your phone is installed with a name like spy, monitor, or other similar unsubtle words. Here’s how you can detect them:
- Go to Settings.
- Choose Applications.
- Find either Manage Applications or Running Services.
- Check for suspicious apps by scanning their names.
Don’t know whether any unfamiliar apps you found are suspicious? Simply Google their names. If any red flags pop up, uninstall the apps in question immediately.
An alternative method is to root through file sections and directories to find ones with suspicious titles. Here’s how it’s done:
- Open your file manager. Depending on your device, this can be called Files by Google, My Files, or something similar.
- Access Internal storage (phone or SD).
- Choose Android.
- Choose Data.
- Browse around for folders or unknown apps with suspicious names.
Remove spy software on iOS devices manually
In most cases, spying on an iPhone requires jailbreaking. Even then, the spy apps need a third-party installer to work.
While not foolproof, you can check for apps like Cydia or Icy. If you have them, your phone is jailbroken.
You can also see if all the apps installed on your device are in the official App Store. If any aren’t, it’s another sign your phone is jailbroken. For either jailbreaking scenario, the best solution is to update to the latest iOS version.
A third option involves parental control apps (aka no-jailbreak apps) like mSpy that can spy on what you upload on iCloud. The easiest fix here is to change your iCloud password.
How to reset to factory settings on Android and iPhone
If nothing else helps, you might need to resort to performing a factory reset to clear your phone of spyware. This is the nuclear option for removing spy apps. It’ll wipe your phone, which means your settings, apps, contacts, media, and other stuff will be gone. Remember to back up everything important before a factory reset.
Factory reset on an Android device
As is always the case with Android devices, reverting to your factory settings may be slightly different depending on your device and the version of your OS. The general process of a factory reset should be similar to the following for Android users:
- Make sure the phone is well-charged or plugged in.
- Enter the Settings menu (usually by swiping down on the main screen and selecting the appropriate button).
- Tap System.
- Tap Advanced.
- Go to Reset Options.
- Select Erase all data (factory reset).
- Tap Erase all data.
- Enter PIN if prompted.
- Tap Erase all data to confirm.
Factory reset on an iPhone
Before performing a factory reset on an iOS device, it’s a good idea to back up your files on iCloud. Once you’ve done this, follow these steps:
- Go to Settings.
- Select General.
- Tap Transfer or Reset iPhone.
- Tap the Erase All Content and Settings option.
- Enter your device password and/or Apple ID password if prompted.
- Tap Erase iPhone to proceed.
Factory resets are the most extreme option for removing spy software, but these make sure your phone is fresh and free of spyware.
Can someone spy on you when your phone is off?
Yes, there are ways to spy on you via your phone, even when it’s turned off.
A common trick hackers use is to make your phone appear turned off when, in truth, it’s just pretending to be. It’s possible to simulate a switched-off state by locking the screen, blocking calls, and turning off notifications.
This can’t be done remotely — someone or something has to compromise your phone in the first place. Such tricks can be accomplished only when malicious software is installed on your phone.
Another related subject is Airplane Mode. For iPhone users, turning on Airplane Mode doesn’t mean the phone is immune to tracking. As long as Bluetooth stays on, an iPhone will still ping other iPhones as part of the system that makes Find My Device and Apple AirTags work. So, while this doesn’t allow hackers to access your files, they can still track your location.
How can someone remotely access my phone?
The most conventional way to hack a phone is by physically installing a monitoring app from one of the official app stores, but your cell phone can get compromised remotely by one of these means:
- Suspicious emails: just as you shouldn’t open suspicious email links and attachments on a computer, you should also refrain from doing so on your phone;
- Compromised apps: think everything you find in your app store is safe? Think again. For instance, researchers found over 200 malicious apps — garnering more than 3 million downloads — in Google Play from 2023 to 2024. It’s all too easy to download a third-party app that wasn’t properly vetted by your app store;
- Jailbreaking: if you want to install third-party apps on Apple products, you need to jailbreak them. Once you do this, however, you’re opening up your device to a world of risks;
- No-jailbreak apps: this is a niche category of Apple monitoring apps that spy on you by accessing your iCloud updates.
Codes to check if your phone is tapped
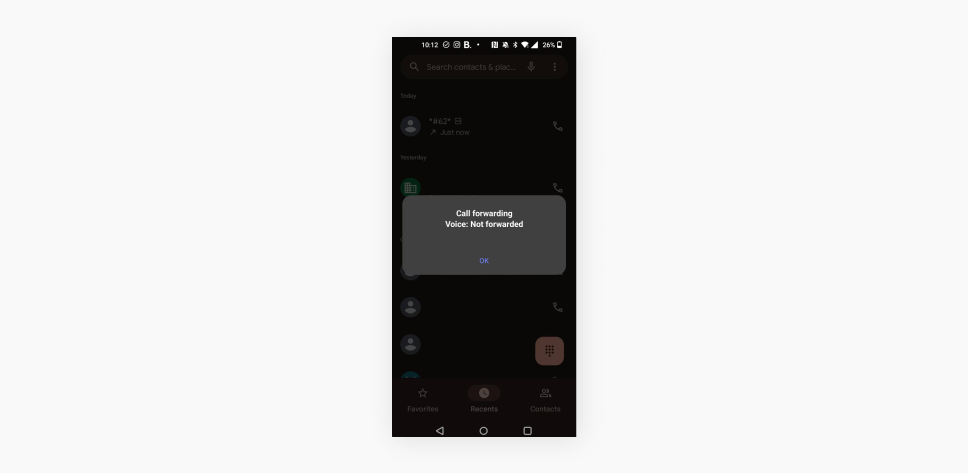
USSD (Unstructured Supplementary Service Data) codes are shortcodes that allow you to access certain network functions directly, and they can be mighty handy for seeing if someone is listening in on your calls.
To test them out, enter the full codes presented below — complete with the * and # symbols — and tap the call button. Just note that they may not work in all countries or with all phones and operators.
- Check for redirects: enter *#62* to see if your calls are redirected to another phone number. If you see a different number, be sure to check it online, as it may be your service provider’s voicemail function. If it isn’t, you can dial ##002# to reset;
- Check for call forwarding: enter *#21# to find out if calls or texts are getting automatically diverted to another number. Call forwarding is different from redirection, as this can be set up under specific conditions, like when your phone is busy. If you find call forwarding incorrectly configured, reset it by dialing ##002#. You can also completely turn it off in your settings.
Key takeaway: outsmart snoops with an antivirus
Can someone install spyware on your phone without touching it? Yes.
Can you tell that your phone is being spied on? Also yes.
And once you know your security is compromised, you can take corrective measures. One step you can take right now is getting an antivirus tool to secure your smartphone and keep spyware at bay.
FAQ
How can you tell if someone is spying on your phone?
A few common conditions, like strange texts, weird noises during calls, or your phone heating up or restarting for no reason, can help you determine whether your phone has been compromised.
Is someone watching me through my phone?
In most cases, no one can watch you through your phone without your knowledge. However, if your phone is infected with spyware, it’s possible for someone to access your camera or microphone and track your location. To protect your privacy, keep your phone updated, use strong passwords, and consider using a security tool like a VPN and antivirus.
Can someone spy on your phone without you knowing?
Yes, if someone had physical access to your phone and installed monitoring software, they can now spy on your phone.
How do I stop my phone from being monitored?
There are different solutions for getting rid of monitoring software on your phone. Run frequent malware scans, always keep your phone OS updated, don’t download sketchy apps, and if nothing else helps — perform a factory reset of your phone.
Can someone use your IP address to spy on your phone?
While your IP address cannot be used directly to spy on your phone, there are a few ways in which your IP address could be used in an attack, which could compromise your security and privacy.
Can someone spy on my phone through linked contacts?
No, hackers generally can’t directly spy on your phone through linked contacts. However, if your phone is compromised with spyware or if you share sensitive information through apps that have access to your contacts, it’s possible for someone to gather details from those contacts. Always be cautious about which apps and services you grant permissions to.
Can someone see exactly what you’re doing on your phone?
Yes, someone might be able to monitor your activities, such as your browsing history, calls, texts, or real-time screen activity, if your phone is infected with spyware. To protect yourself, ensure your phone is secure by using strong passwords, regularly updating software, and using trusted security tools like a VPN app for your iPhone or Android phone and an antivirus.