
A VPN (Virtual Private Network) creates a secure connection between your device and the internet, allowing you to protect your privacy and improve online security. You may already be using one, but do you know what type of VPN it is? And I don’t mean the brand, like Surfshark. I mean remote access, site-to-site, personal… Let’s discuss them in greater detail and see how they differ.
Table of content
VPN types: how do they work?
VPN types are not the same as VPN providers. If we compare VPNs to cars, the VPN type would be like a type of car: hatchback, sedan, SUV, and so on. They differ in implementation and function.
VPN providers, then, would be like car manufacturers: your car may come from Toyota, Ford, or Mercedes-Benz, while your VPN may be provided by Surfshark, Nord Security, or some other company.
Our tech specialists up to the CTO level say there is no set-in-stone way of sorting VPN types and no SI-system-approved table. But everyone still does it anyway, so here’s our take:
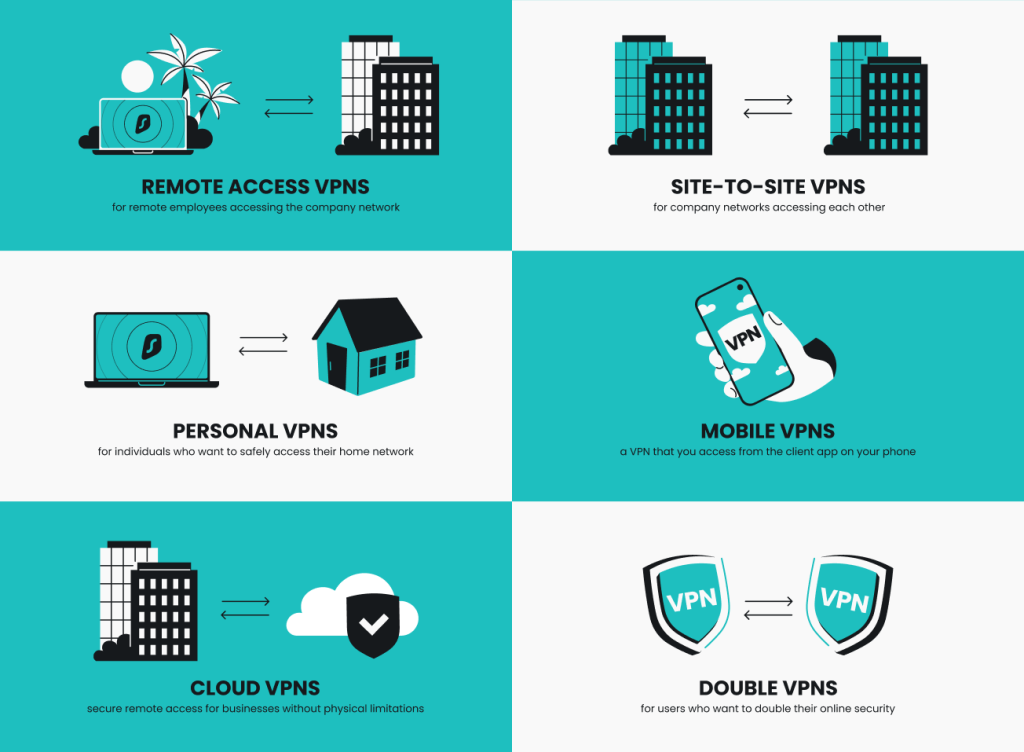
Remote access VPNs
A remote access VPN allows a user (you) to establish a secure connection to a network remotely. The most likely application of this is in a business setting to access your work network from home.
How do remote access VPNs work?
With a remote-access VPN, you will have a VPN client (app) installed on your device. This client establishes a secure VPN tunnel to the VPN server. Any data passing between the client and remote private network is encrypted, so it’s hidden from observation even when you use regular public internet to maintain the connection.
What does this mean?
For businesses, this means allowing your data, files, and other resources to be accessed remotely and kept safe.
For individuals, this also means keeping your data safe. Many commercial types of VPNs operate the same way. You, the user, connect to a VPN server, which allows you to access their network — the internet.
As a result, you get benefits like:
- Websites and services see the server’s IP address and consider the server’s location yours;
- Firewalls and other blocking mechanisms see that you’re connecting to the VPN server, not YouTube or Roblox, so they let the connection go through.
Site-to-site VPNs
Site-to-site VPNs, sometimes referred to as router-to-router VPNs, connect two or more remote private networks.
A site-to-site VPN is usually used by organizations to connect different branches or locations to one big private network. For example, a company office in Kiribati connects to the office in Warsaw. This is called an intranet-based site-to-site VPN.
In an extranet-based site-to-site VPN, one company could allow another to access only specific data needed for their partnership.
Site-to-site VPNs are complex to set up, so they’re used mainly by large businesses.
How do site-to-site VPNs work?
A site-to-site VPN often uses routers to connect the private networks of two organizations.
One router acts like the client, and the other like the server the client connects to. This is more complicated than the remote access model, where the client is simply a phone or computer app.
Personal VPNs
A personal VPN is a VPN you, the user, set up to securely access your home network. Say you want to use your printer at home for some remote printing. This could be accomplished via a secure personal VPN connection — you set up the server at home, connect to it from somewhere else, and you can securely access the devices at your home.
On the other hand, you can call consumer VPN services like Surfshark personal VPNs because they’re meant to be used by individual customers — personally. A residential VPN that uses the IP addresses of other users across the globe could also be considered a personal VPN.
When looking for the best personal VPN, it’s important to consider factors like ease of use, encryption standards, and server network size.
How do personal VPNs work?
You, the user, download the VPN app and connect to your chosen server. And that’s it — your work is done. The server and the client on your device handle all the data encryption and decryption.
So, the function of a personal access VPN is similar to that of a remote access one. The difference is that a remote access VPN opens up into a relatively small corporate network, while a personal VPN goes out into the internet.
Mobile VPNs
If you’re accessing the World Wide Web (www.) on your phone, you may also want to use a VPN. Mobile VPN is a virtual private network that works on your phone. It is very helpful when traveling, connecting to unreliable free Wi-Fi hotspots, and getting past restrictive local firewalls that bar access to certain websites.
How do mobile VPNs work?
Mobile VPNs exist mainly in Android and iOS varieties. Both systems have their own built-in VPN support. But for the best mobile VPN experience, you want to get a commercial VPN with client apps compatible with your phone. That will be practically all of them, including Surfshark.
Cloud VPNs
A cloud VPN allows you to securely access cloud-based environments. For example, if a business’s resources, data, and applications are stored in the cloud, you can securely access them with a cloud VPN connection via an app or a website.
The advantages of cloud VPNs are that they’re not limited to specific locations, and the secure and encrypted connection can be rapidly deployed and accessed globally.
How do cloud VPNs work?
Cloud VPNs are usually hosted and managed by cloud providers. They work just like traditional VPNs, creating secure encrypted tunnels between networks, using the same security and encryption protocols — only in the cloud rather than physical infrastructure.
Double VPNs
Double VPN is a VPN security feature rather than a VPN type. However, it is worth the mention. Instead of routing your internet traffic through one VPN server, Double VPN routes it through two. By encrypting your data twice, it doubles your privacy and online security.
How do Double VPNs work?
This VPN setup configuration encrypts and routes your data via one remote VPN server. Then, it sends the data through a second VPN server and re-encrypts it, making your connection safer and more private. Some VPN providers even let you manually select the entry and exit servers — like Surfshark’s Dynamic MultiHop.
Which VPN type is best for your business vs. your personal needs?
Now that we’ve looked into the different types of VPNs, let’s see which one is better for business and which one for personal needs:
Business | Personal | |
|---|---|---|
Remote access VPN | ||
Site-to-site VPN | ||
Personal VPN | ||
Mobile VPN | ||
Cloud VPN | ||
Double VPN |
Classifying VPNs by price
Consumer-grade VPNs, like Surfshark or any other VPN provider you might use, are mostly classed by price. This type of VPN can combine some of the features described in the previous sections, depending on what service they try to provide.
The only big difference, however, exists between paid VPNs — basically any VPN that charges a subscription fee — and free VPNs. On the other hand, the choice may not be so obvious to the consumer.
The average cost of a paid VPN varies from company to company — it can cost around US$3.65 a month for discounted 1-3 year deals, while the cheapest monthly VPN can be priced as low as US$2.03. And while not paying for a VPN service may seem appealing, the truth is that free VPNs are worse than paid ones in every way.
When it comes to functionality, such as the number of servers, server locations, speed, whether or not speed limits exist, the app’s usability, platforms supported, and so on, paid VPNs always win.
Limitations of the top free VPNs (according to data by Techradar): | Paid VPN for contrast (Surfshark): | |
|---|---|---|
Servers | 1-50+ | 4,500+ |
Server countries | 1-20+ | 100 |
Data limits | 500MB/month* – 10GB/month | No |
~** | No | |
24/7 support | No*** | Yes |
*One provider offers 500MB/day limits
**One provider offers unlimited data but engages in speed throttling
***4 out of 6 VPNs in question
Understand VPN protocol types
No matter what type of VPN you use, they all rely on a VPN protocol. If we continue with the car metaphor, a VPN protocol would be like the car’s engine — it’s what makes it work. And just like with engines, several VPN protocols were developed, improved, superseded by others, and declared obsolete.
- IPSec (Internet Protocol Security). IPSec, very technically speaking, is not a VPN protocol by itself. It can create a secure tunnel that a VPN needs to work, but it can’t establish secure communication. That’s why IPSec/IKEv2 is more popular: IPSec does the tunneling, and IKEv2 sets the groundwork for establishing it.
- L2TP (Layer 2 Tunneling Protocol). L2TP isn’t the newest protocol, but it isn’t the oldest, either. It is a tunneling protocol that generates a secure tunnel between two L2TP connection points. It is often combined with IPSec security protocol to encrypt the sent data and establish a secure VPN connection.
- PPTP (Point-to-Point Tunneling Protocol). PPTP was developed with the cooperation of several companies, including Microsoft. As such, PPTP was bundled with Windows as part of the native VPN capability. However, multiple vulnerabilities have been discovered over the years, making PPTP fairly easy to crack.
- SSL (Secure Sockets Layer) and TLS (Transport Layer Security). SSL and TLS aren’t exactly VPN protocols. They are certain types of encryption used to secure your everyday internet use — that’s what puts the S in the HTTPS bit you see when entering a web address. So, you don’t really get to choose whether to use them.
- SSH (Secure Shell). SSH is very close to what you could consider a VPN protocol. It operates on similar principles, with one key difference: it only protects one connection to a specific target, while a VPN can encrypt all your traffic.
- OpenVPN. OpenVPN is an open-source VPN protocol, one of the mainstays of the VPN protocol business. It has been relentlessly tested over years of use in all sorts of settings. It may not be the freshest design ever, but it is reliable, which counts for a lot.
- WireGuard. WireGuard is one of the newest VPN protocols out there. It’s faster and smoother than others, even OpenVPN. Over the past few years, it has steadily claimed more and more space in the consumer VPN market.
In conclusion: get the type of VPN you need
When shopping for a VPN, you should consider not only the brand but also the type of VPN you need. Choose remote access VPN, site-to-site VPN, or cloud VPN for your business. For personal use — get Surfshark VPN. It provides a VPN connection on all your devices, including mobile, and offers advanced security features like Double VPN.
FAQ
How many types of VPNs are there?
While there is no hard classification of VPNs, the main types are: remote access VPNs, site-to-site VPNs, personal VPNs, mobile VPNs, cloud VPNs, and double VPNs (a noteworthy personal VPN feature).
What is the best type of VPN?
The best type of VPN depends on how you sort VPNs into types. If you sort by price, paid VPNs are better than free VPNs. If you sort by use cases, it depends on your needs. For example, you’ll need a remote access VPN if you need your employees to connect to the business network. However, a mobile VPN is the way to go if you want to remain secure during your daily online activities while traveling.
What are the types of VPN tunnels?
There are no types of VPN tunnels as the tunnel is either established or not. There are different VPN tunneling protocols, which include OpenVPN, IKEv2, L2P2, PPTP, WireGuard, and SSTP.
Does Surfshark VPN suit personal and business use?
Surfshark VPN is suitable for both personal and business use. Our regular subscriptions are best for personal day-to-day use. However, you can get Surfshark for business by filling out a request form here and getting an offer tailored to your company’s needs.
What type of VPN is most commonly used today?
The most commonly used type of VPN is personal VPN. With people becoming more aware of their security and privacy online, personal VPNs are becoming more and more popular for daily use.




