You’ve likely heard that a VPN is one of the best ways to stay safe online.
But do you know what’s really happening behind the scenes? At the heart of it all is something called a VPN tunnel.
What is a VPN tunnel, and how does it work? Don’t stay in the dark — let’s unravel these internet pathways that are key to gaining greater security online.
Table of contents
What is a VPN tunnel?
A VPN tunnel is a secure, encrypted connection between your device and the internet routed through a VPN server. It’s called a “tunnel” because it creates a safe pathway for data to travel between two devices.
You know how they call the internet the information superhighway? Well, while the rest of the internet is regular traffic on this highway, a VPN tunnel provides a private VIP lane for all your data.
And since every bit of online data traveling along this tunnel is encrypted, it’s extremely difficult for anyone to see what you’re doing or intercept your browsing information.
How does VPN tunneling work?
VPN tunneling is the process of routing your internet traffic through an encrypted connection to a remote server. Even though this process can take a fraction of a second, it’s worth understanding what happens every step of the way.
As the VPN tunnel diagram above shows, setting up a secure tunnel involves these steps:
- Connecting to a VPN: you won’t get far without a VPN service like Surfshark on your device. Choose your preferred virtual location and click Connect.
- Authenticating your connection: next, your VPN provider starts a kind of negotiation with your desired server. Your device communicates with the VPN server to ensure the proper security measures are in place.
- Establishing your tunnel: if everything checks out, an encrypted tunnel between your device and the VPN server will be created. You’ll access the internet through the server with a secure, private connection.
Now that you have a VPN tunnel in place, how does it actually enhance your online privacy? VPN tunneling:
- Encrypts your data: a secure VPN scrambles your internet traffic, making it unreadable to anyone who’s able to access it;
- Hides your IP (Internet Protocol) address: VPN tunnels mask a user’s IP address, making it harder to track their online activity;
- Secures public Wi-Fi: an encrypted tunnel protects your data from prying eyes when using unsecured public networks;
- Safeguards personal information: a VPN connection keeps sensitive information like login credentials and browsing data safe;
- Prevents ISP (Internet Service Provider) tracking: VPN tunneling stops your ISP from monitoring and logging your browsing activity.
What are VPN tunneling protocols?
Not all VPN tunnels are created equal, and some are, in fact, safer than others. It all comes down to the VPN protocol you’re using.
You see, VPN tunneling protocols are rules that determine how your data gets transmitted through a VPN tunnel. They tell your VPN how to encrypt, send, and receive data between your device and the VPN server.
The good news is that your VPN app should let you choose which encryption protocols you want to use. Here are the main types of VPN protocols and their respective pros and cons:
WireGuard
WireGuard is the newest VPN protocol on the block, and it’s also one of the best. With streamlined code, WireGuard provides improved performance and power use while still maintaining a secure connection. This minimalistic design also reduces the possibility of dropping your encrypted connection, making you less vulnerable to threats.
WireGuard does have a few weaknesses worth noting. As a newer tunneling protocol, it isn’t as battle-tested as the older alternatives. It also has limited additional features, making it less versatile than other choices.
Pros | Cons |
|---|---|
Robust security | Relatively new |
Minimal coding | Limited features |
Exceptional speed | Less compatible with legacy devices |
Verdict: highly recommended
IKEv2
IKEv2 (Internet Key Exchange version 2) is a tunneling protocol known for its speed, stability, and solid data encryption. Developed by none other than Cisco and Microsoft, IKEv2 supports powerful algorithms and offers high-speed performance. Its ability to switch networks on demand makes it an excellent choice for mobile users.
Regarding downsides, IKEv2 isn’t as universally available as other protocols. Specific networks and firewalls may still block it, and it’s so feature-rich that manual configuration can be a headache.
Pros | Cons |
|---|---|
Fast speeds | Limited support |
Strong encryption algorithms | Can be blocked by firewalls |
Seamless mobility | Complex configuration |
Verdict: highly recommended, especially for mobile devices
OpenVPN
OpenVPN is one of the best VPN tunnel protocols available. It’s flexible, secure, and allows for strong encryption. It works on most platforms and — as its name suggests — is an open-source protocol, resulting in greater transparency. It’s even compatible with advanced VPN features like a kill switch and split tunneling.
On the other hand, its robust nature means performance may lag depending on server load, and certain networks may block OpenVPN traffic. Manual set-up can also be tricky, so it’s best to use OpenVPN with a user-friendly VPN service that does all the heavy lifting for you — like Surfshark.
Pros | Cons |
|---|---|
High-end encryption | Difficult manual set-up |
Robust security capabilities | May be blocked by some networks |
Verdict: highly recommended, especially for routers
Disclaimer: The remaining protocols are not supported by Surfshark.
SSTP
The SSTP (Secure Socket Tunneling Protocol) VPN protocol uses SSL (Secure Sockets Layer) encryption to protect data during transmission. With the ability to bypass firewalls, SSTP should offer robust VPN protection in theory, but it isn’t recommended for most users.
Why? SSTP is primarily designed for Windows, so setting it up on other operating systems like macOS is more complicated. It doesn’t have open-source code and has never been publicly audited, which raises concerns about potential vulnerabilities. Lastly, if the available bandwidth is limited, SSTP may cause slower speeds and performance issues.
Pros | Cons |
|---|---|
Can bypass firewalls | Requires excess bandwidth |
Connections are often reliably stable | Never been audited |
Strong encryption | Code isn’t open-source |
Easy to set up on Windows | Hard to set up on any non-Windows OS |
Verdict: Not recommended
PPTP
Developed by Microsoft, PPTP (Point-to-Point Tunneling Protocol) is one of the earliest VPN tunnel protocols. It’s known for being easy to configure and having native support for all major operating systems. PPTP’s relatively basic encryption also allows for fast performance.
However, PPTP’s security is now outdated and simply isn’t as strong as other modern protocols. It can be easily blocked by firewalls and restricted networks, limiting its effectiveness. As a result, most VPN providers don’t support PPTP.
Pros | Cons |
|---|---|
Easy to set up | Relatively weak encryption |
Fast performance | Vulnerable to attacks |
Compatible with most operating systems | Can’t bypass many firewalls |
Verdict: not recommended
L2TP/IPsec
As PPTP’s successor, L2TP (Layer 2 Tunneling Protocol) looked to improve on its predecessor’s shortcomings. Combined with IPsec (Internet Protocol Security), L2TP offers a strong balance of security and speed. Most operating systems are supported, and the resulting encryption is strong and stable.
The biggest problem with this protocol is that the mix of L2TP and IPsec can lead to slower speeds and subpar performance. In addition, firewalls might still block it, and configuring its advanced security settings can get quite complex.
Pros | Cons |
|---|---|
Stong security | Slower speeds |
Widely supported | Hard to set up |
Stable and reliable | Can’t bypass many firewalls |
Verdict: not recommended
Shadowsocks
Shadowsocks isn’t a full-fledged tunneling protocol in the traditional sense — think of it as a VPN lite. Shadowsocks routes network traffic through a remote server to mask your online activity. It focuses on speed and simplicity and is popular for accessing blocked content.
However, Shadowsocks isn’t as secure as a VPN and lacks many standard encryption and security features. While it’s suitable for evading censorship with minimal impact on browsing speed, it’s not ideal for those looking for greater online privacy.
Pros | Cons |
|---|---|
Relatively fast | Doesn’t secure all internet traffic |
Helps bypass censorship | Not practical for general data privacy |
Open source and constantly under development | Limited security features |
Verdict: only recommended for bypassing censorship
How to test a VPN tunnel
There are two common methods you can use to see if your VPN tunneling is working:
-
Run an IP address leak test
Disconnect from your VPN and use a free online tool (like Surfshark’s IP address checker) to note your IP address.
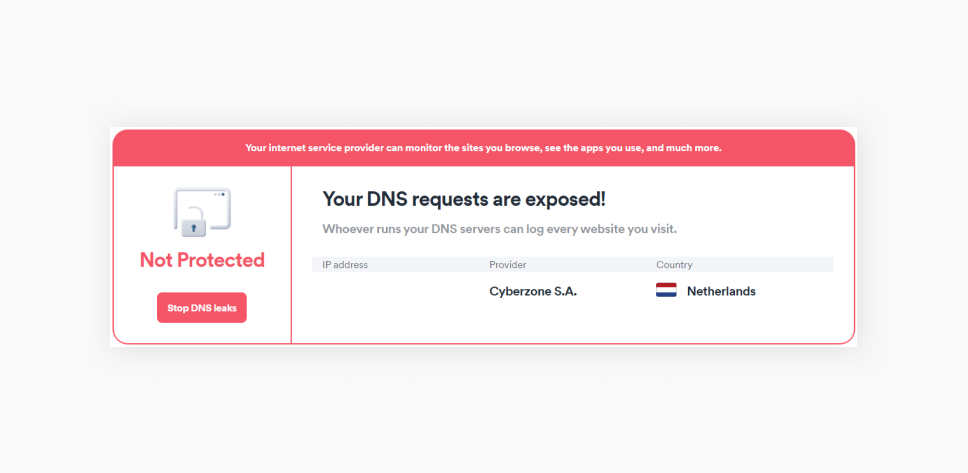
Then, activate your VPN and refresh the webpage. If your IP address, ISP, and location have changed, your private pathway to the internet is secure.
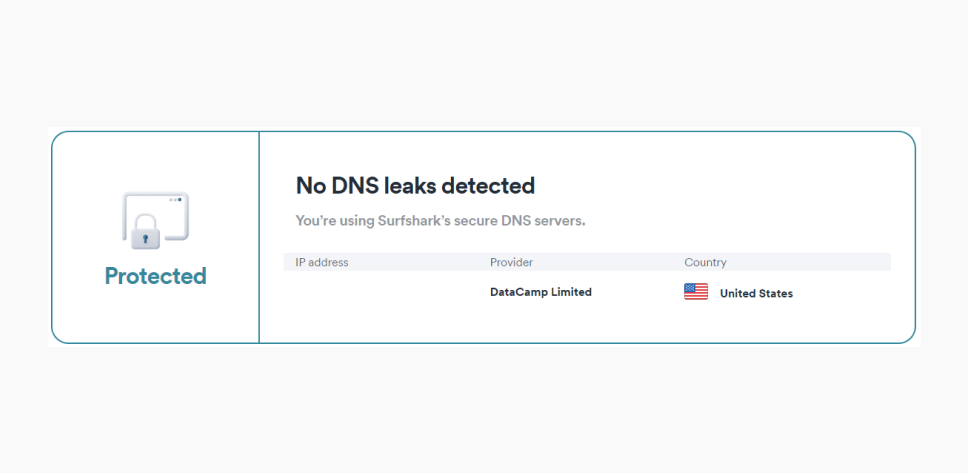
-
Ping the remote network
Those who are more tech-savvy can test their VPN via pinging. First, disconnect your VPN and open either Command Prompt if you’re using Windows or Terminal if you’re on macOS/Linux.
Type in “ping google.com” or use another reliable website and hit Enter/Return to check your connection’s latency. Focus on the time measurements on the right.
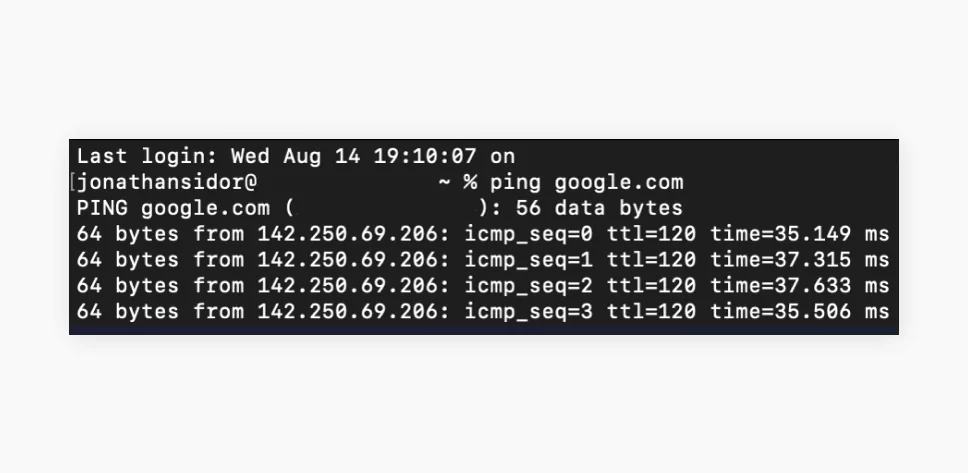
Now, repeat the process with your VPN turned on. If the ping is higher, you likely have a strong VPN tunnel providing a secure and encrypted connection.
What is VPN split tunneling?
VPN split tunneling (called Bypasser in Surfshark) is a feature that allows you to choose what data packets go through a VPN tunnel and which remain unprotected. This is useful if you want your VPN provider to protect a single app or keep some websites away from an encrypted connection.
For example, users often can’t gain access to banking apps with certain types of VPNs. You can set up your VPN service to encrypt all your internet data except your bank’s app, allowing you to handle your finances directly while protecting the rest of your traffic.
Split tunneling is particularly helpful when using services that require your actual IP address, accessing wireless devices on your home network, and excluding data-heavy apps that can slow your internet connection.
Enjoy multiple protocols in one tool
There isn’t one protocol that objectively offers the best VPN tunnels. While most users won’t instantly notice any differences between them, it’s still good to have a solution that offers multiple protocols, just in case.
A solution like Surfshark VPN.
Surfshark puts three tunneling protocols — OpenVPN, IKEv2, and WireGuard — at your fingertips. The best part? You don’t have to choose manually — Surfshark is pre-configured to use the most optimal one every time.
Disclaimer: Surfshark doesn’t support IKEv2 on Windows.
FAQ
What does a VPN tunnel do?
A VPN tunnel encrypts your internet traffic, creating a secure connection between your device and a remote server. This protects your data from hackers, masks your IP address, and allows you to browse the web privately.
Are VPN tunnels legal?
Yes, VPN tunnels are legal in most countries. However, using a VPN for illegal activities or in countries where VPNs are restricted could lead to legal issues. Always check local laws before using a VPN.
Can I use a VPN tunnel for free?
You can set up a VPN tunnel for free, but this isn’t recommended. Many free VPN providers offer outdated tunnel protocols and limited features that expose you to threats.
What is the best VPN tunnel?
The best VPN tunnel protocols are OpenVPN, IKEv2, and WireGuard, as they give enhanced online protection with minimal impact on network performance.
Which VPN protocols are supported by Surfshark?
Surfshark supports three VPN protocols: OpenVPN, IKEv2, and WireGuard. These protocols are among the safest and allow for optimal VPN performance.



