Post-quantum encryption is a new kind of encryption designed to resist attacks from quantum computers — future machines that could crack today’s security systems much faster than any regular computer ever could.
If that sounds a little overwhelming, don’t worry — you’re not alone. In this article, we’ll walk you through what post-quantum encryption is, why it matters for your online privacy, and how you can use it to stay protected. Let’s dive in!
What is post-quantum encryption?
Imagine if the super-powerful computers of the future could easily crack the security tools we rely on today. That’s the problem post-quantum encryption (PQE) is designed to solve.
Post-quantum encryption is a type of encryption that’s built to protect your data against attacks from quantum computers. Right now, traditional encryption protects most of what we do online, from shopping and chatting to logging into our bank accounts. But quantum computers could one day become strong enough to break those defenses in minutes, putting today’s sensitive data at risk. In fact, some attackers are already engaging in Harvest Now, Decrypt Later (HNDL) tactics — collecting encrypted data in hopes of cracking it once quantum technology matures. That’s why it’s important to adopt post-quantum encryption now.
The current situation is far from perfect. A recent analysis by Surfshark examined 12 popular messaging apps to assess their preparedness for the quantum era, focusing specifically on end-to-end encryption. The results were eye-opening: only two apps — Signal and iMessage — have already introduced post-quantum cryptographic protections. While this analysis targeted E2EE, it’s important to remember that quantum computing poses a threat to all widely used cryptographic systems — not just messaging security. Most apps, even those that promote strong encryption today, remain vulnerable to future quantum decryption methods.
How post-quantum encryption works
Because traditional encryption relies on traditional math problems, such as factoring large numbers or solving discrete logarithms, quantum computers could crack it quickly. Post-quantum encryption, however, is built around entirely different kinds of problems that are much trickier for quantum computers to figure out.
For example, many post-quantum methods use lattice-based cryptography, where breaking the encryption would require solving extremely complex geometric puzzles in high-dimensional spaces. Others use multivariate polynomial equations, hash-based cryptography, or code-based cryptography, all of which remain resistant to known quantum attacks.
Since quantum computers excel at some types of math but tend to struggle with others, these new techniques make it incredibly difficult — even impractical — for a quantum computer to break the encryption.
Post-quantum encryption vs. post-quantum cryptography
You’ll often see the terms post-quantum encryption and post-quantum cryptography used together, but they aren’t exactly the same thing.
Post-quantum encryption is specifically about protecting sensitive data, like secure messages and encrypted emails or online activity, against future quantum attacks.
Post-quantum cryptography, on the other hand, is the bigger picture. It covers everything related to building security tools that can survive the power of quantum computers, including encryption, digital signatures, and secure communication systems.
In simple terms:
- Post-quantum encryption = protecting what you send and receive;
- Post-quantum cryptography = building all the tools needed for a safer future internet.
(Not to be confused with “quantum cryptography,” which refers to theoretical systems that would run on quantum computers themselves — something that still lies in the future.)
How to protect yourself from future quantum threats
You don’t need to wait for quantum computers to go mainstream to start protecting your data. One of the smartest things you can do today is to use services that already have post-quantum encryption built in.
At Surfshark, we’ve integrated post-quantum protection into our app by upgrading how it handles the WireGuard protocol. That means when you connect using the WireGuard protocol, your online activity gets an extra layer of future-proof security without you having to do anything extra.
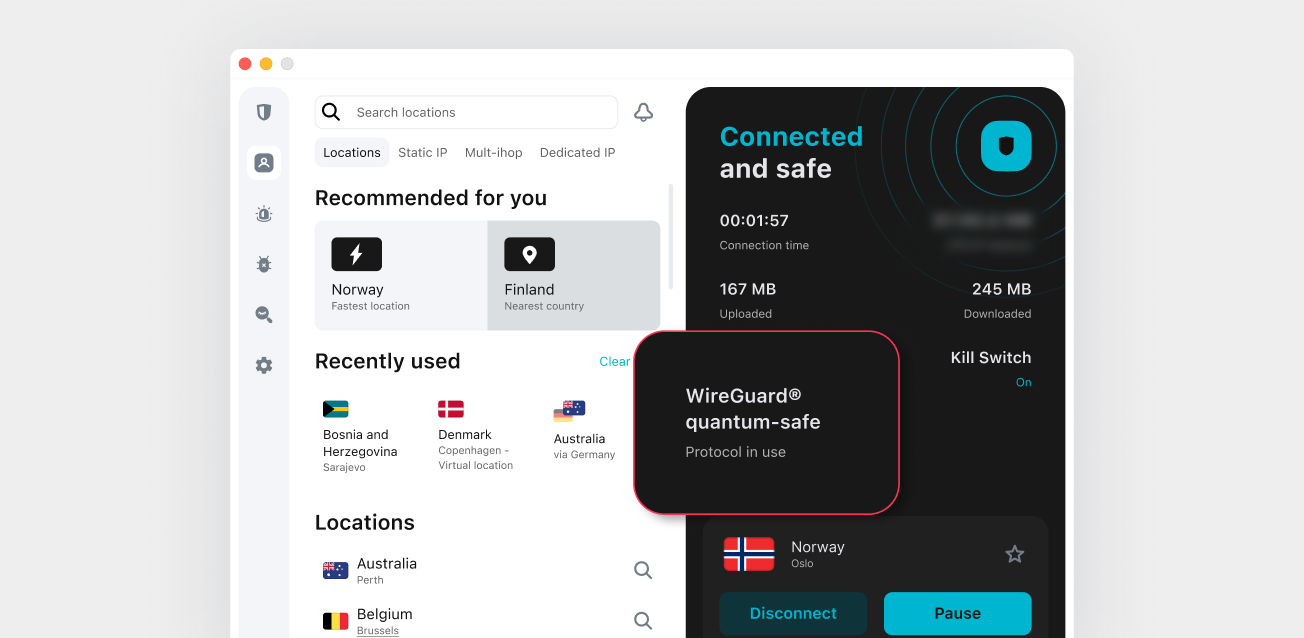
Here’s how to make sure you’re covered:
- Open the Surfshark app on your device;
- Go to VPN Settings, choose Protocols, and select WireGuard as your VPN protocol of choice;
- For extra peace of mind, disable Auto-connect, as it could switch you to a different protocol when reconnecting.
With these settings in place, you can browse, stream, and enjoy your privacy — now and in the quantum future.
Conclusion — an ounce of prevention is worth a pound of cure
Quantum computers might sound like science fiction now, but the risks they bring to online privacy are very real — and getting closer every day.
The good news? You don’t have to wait for the future to prepare. With Surfshark’s WireGuard protocol offering post-quantum encryption in-app, you’re already one step ahead. Protecting your personal information now means you’ll be ready for whatever comes next.
FAQ
Why do quantum computers threaten today’s encryption?
Quantum computers process information in a completely different way, allowing them to break current encryption methods much faster than traditional computers. Because some organizations may be saving encrypted data now to crack it later, Surfshark is adopting post-quantum encryption early.
Why isn’t post-quantum encryption more widely adopted?
While quantum computers are theoretically capable of breaking widely used encryption methods, machines powerful enough to do that don’t exist yet — at least not in a publicly known, scalable form. But because the threat is still emerging, Surfshark adopts post-quantum encryption early, with the goal of helping future-proof user security.
How long until quantum computers break encryption?
It’s hard to estimate the exact timeline, as it constantly shifts as progress accelerates. The real concern isn’t just when quantum computers will be powerful enough but who will have access to them first. Sensitive data encrypted today could be harvested and stored for decryption once those capabilities arrive. That’s why starting the transition to quantum-safe solutions now is more important than ever.
Does Google use quantum computing?
Google is actively researching quantum computing and achieved a milestone called quantum supremacy in 2019.
What are NIST’s post-quantum cryptographic standards?
NIST (National Institute of Standards and Technology) is leading the development of official standards for post-quantum cryptography — algorithms designed to resist attacks from quantum computers. In August 2024, NIST finalized the first three of these standards, marking a major milestone in helping organizations begin transitioning to quantum-resistant encryption.

