
Scammers never sleep, not as far as you should be concerned. According to the 2021 report on the State of Phishing & Online Fraud, internet fraud activities rose 185% from 2019 to 2020, and it hasn’t stopped since. In fact, we have a new collection of types to look out for in 2024. So let’s talk about what online scams are and how to avoid them.
Table of contents
Spoofing
Spoofing refers to someone disguising an email address, a phone number, the name of the sender, or a website URL by changing one letter, symbol, or number to a similar looking one.
Spoofing as an online scam technique stands next to phishing because both are often used in conjunction.
The goal is to make you misread the changed credential and make you believe you’re interacting with a figure you trust. You might receive a message or an email that looks like it’s from someone you know — your boss, a family member, or a doctor.
How to protect yourself from getting spoofed:
- Check every symbol. Always check the credentials letter by letter and number by number. It’s a tedious process, and you will want to skip this step, but that’s exactly what the scammers hope to achieve;
- Check online if the credentials match. If you’re not sure about the link or the phone number, don’t click it and don’t answer. It’s better to be safe by running the address or the number online.
Phishing

Phishing — pretending to be a legitimate business or person to trick you into giving away money or sensitive information — continues to dominate the online scams chart. For instance, it’s one of the most popular scams on Telegram.
How does phishing happen:
- Deceitful communication: scammers will use any form to get to you — email, text messages, social media, or even phone calls. They impersonate legitimate entities and create a sense of urgency, curiosity, or fear to prompt the victim to respond;
- False pretenses: phishers craft messages, imitating an entity you might trust — the branding, logos, and design of legitimate organizations to deceive recipients. They may claim a problem with the victim’s account, a security breach, or a need for immediate action to entice the victim into taking action without thinking critically;
- Request for sensitive information: the message requests the victim to provide login credentials, credit card numbers, social security numbers, etc. The message may direct the victim to click on a link leading to a fake website designed to collect the information;
- Redirecting to fake websites: phishers often include links in their messages that redirect recipients to fraudulent websites. These websites resemble the legitimate sites they imitate, tricking users into entering their information. The fake sites may have similar (spoofed) URLs with slight variations or misspellings;
- Information exploitation: once the phishers obtain the sensitive information, they can use it for various malicious purposes, such as identity theft, unauthorized financial transactions, or unauthorized access to accounts. They may also sell the information on the black market or use it for further targeted attacks.
Online job scams
This internet scam is considered a form of phishing — scammers pose as employers or recruitment agencies, targeting individuals seeking employment.
Scammers know many people would prefer earning money working from home. So they place online ads, offering jobs where you can earn thousands of dollars in no time and with little effort while working from home.
These scams aim to deceive job seekers into giving away personal information, paying upfront fees, or performing illegitimate tasks under the false pretense of landing a job.
Tech support scams
Technical support scams lean heavily on phishing tactics — scammers posing as technical support representatives from reputable companies and coercing you out of your money. Usually, it’s the unholy child of a phishing attack and a gift card scam (more on the latter later).
Imagine you unknowingly clicked on a malicious link, and a pop-up window opened saying you’ve got a virus on your computer. The window looks legitimate and tells you to call tech support to fix the issue.
The scammers then contact victims via phone calls or pop-up messages, a typical scenario seen in the well-known Geek Squad scam. They then offer assistance for a fee and may attempt to gain remote access to the victim’s computer to steal personal information.
Payments are usually asked to be made via gift cards or mobile services like Cash App.
How to protect yourself against phishing:
- Be cautious of unsolicited messages, especially those requesting sensitive information or immediate action;
- Verify the legitimacy of any communication by independently contacting the organization through official channels;
- Pay attention to the website URLs and look for signs of secure connections (e.g., “https” and a padlock symbol) when providing sensitive information online.
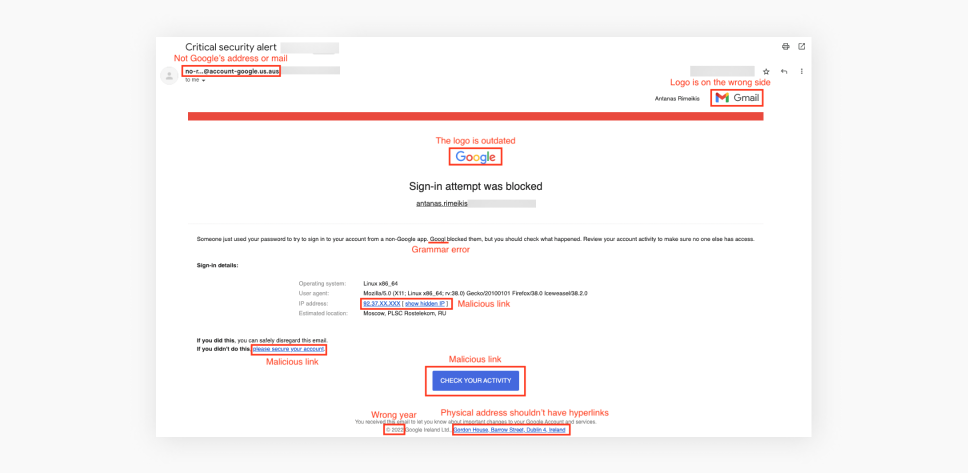
According to IBM’s report, around 20% of data breaches that companies experience come from compromised credentials, which are more often than not gathered via phishing scams. And they take the longest to identify (250 days on average vs. 212 for other methods). Plus, considering that 44% of breaches expose personal data such as names, emails, and passwords, this can lead to even more breaches.
But to avoid becoming the first link in the breach chain, you have to be conscious of the risks posed by such nefarious activity. That’s one of the reasons why Surfshark has compiled everything you need to know about phishing and prepared guides on how to recognize and avoid it.
Gift card scams

Speaking of online scams, a gift card scam is a type of fraud where scammers trick individuals into purchasing gift cards and providing the card information or codes, allowing the scammers to steal the funds loaded onto the cards.
How does a gift card scam happen:
- Scammers contact victims posing as representatives from legitimate organizations;
- They deceive victims with false stories and create urgency;
- They ask victims to buy specific gift cards and share the card information;
- Scammers then steal the funds from the cards, making them hard to trace.
How to protect from gift card scams:
- Be cautious of unsolicited requests for payment through gift cards;
- Verify the request’s legitimacy by independently contacting the organization or individual supposedly involved;
- Be skeptical of any request that demands payment exclusively through gift cards;
- Keep your gift card information confidential.
These days there’s a growing trend of using gift cards, and the FTC reports that online scams using gift cards as payment have been on the uptick, with $148 million being stolen that way in the first nine months of 2021.
What does this mean to you? Well, if anyone asks you to pay in gift cards, you are most likely getting scammed, so beware!

Ransomware

Ransomware is a type of malicious software that locks up your device — or an entire system — to hold it for ransom.
How does ransomware happen:
- Delivery: the goal is to trick the victim into downloading the ransomware onto their device. A victim of ransomware may click on a link in a phishing email, visit a compromised website, or download a malicious attachment;
- Encryption: now that the victim downloaded the “trojan horse” and the online scammer has a way into the system, they will find important personal information and encrypt it, OR they will lock parts of your device, rendering it unusable;
- Ransom demand: the online scammer will contact the victim to trade the “unlock” or the decryption key for a large amount of money. We, normal human beings, call that extortion.
Spyware
Spyware is a sneaky program that secretly watches what you do on your computer or device without you knowing. Spyware is downloaded the same way ransomware is — by clicking a malicious link. It usually lies dormant without the victim noticing.
It monitors your activity and gathers information that can later be sold. It often is used to blackmail people out of their money. In principle, it works similarly to malware — it holds your info ransom for money. Some might call that extortion.
Dead giveaways of spyware:
- Your device battery runs dry faster;
- Less RAM is available;
- Unknown apps are running in the background;
- Unknown apps open and close on their own.
How to protect against ransomware:
- Regularly back up important files and store them offline in a separate and secure location;
- Use anti-malware software and update it;
- Don’t open phishy email attachments or click on suspicious links;
- Keep your operating system and software applications updated with the latest security patches;
- Enable automatic updates for your software and use a firewall to protect your network;
- Educate yourself about phishing emails, suspicious websites, and safe online practices.
2021 was a big year for ransomware: from CD Projekt Red in February to Panasonic in November, loads of large companies felt the sting. What’s more, even oil pipelines and farming industries aren’t immune to it.
Overall, US statistics show that the first half of 2021 saw a 61% increase in ransomware attacks over the same period in 2020. Even the US Department of Justice issued bounties in the tens of millions for information on ransomware groups such as DarkSide.
The sum itself should be an indicator of how serious the threat — and how lucrative a field — ransomware is. So be sure to learn to recognize a phishing email since it’s still one of the easiest ways for this malware to spread.
Sextortion or online blackmail scams
Sextortion is an online scam where scammers coerce people into sending their explicit images and then ask for money in order not to share those images online. Do you remember Black Mirror’s episode called “Shut Up & Dance” (S3E3)? This online scam is exactly that.
How do sextortion and blackmailing scams happen:
- Contact: a scammer will take a different identity and act it out. Then they’ll try to look for potential victims in chat rooms, social media platforms, or dating platforms;
- Building trust: once a victim is found, they’ll try to establish an intimate virtual relationship. The goal is to promise and say whatever the victim might want to hear to lure out explicit material;
- Threats: once the scammer gets ahold of such content, they’ll lose the act and threaten the victim with showing the explicit material to the victim’s close social circles — family, school, work, etc.;
- Extortion: the scammer will ask for a payment, which is requested through untraceable methods like cryptocurrency. Sadly, even if the victim complies, there is no guarantee that the scammer will stop or keep their end of the bargain.
How to protect yourself against sextortion and blackmailing scams:
- Be cautious when sharing personal information or intimate content online, especially with individuals you don’t know and haven’t met in person;
- Use strong passwords for your online accounts and enable two-factor authentication whenever possible.
- Be wary of suspicious or unsolicited contact, particularly if someone pressures you into sharing explicit material;
- Do not engage with the scammer if you receive extortion threats. Report the incident to the local authorities and the platform where the communication occurred. YOU DO NOT NEGOTIATE WITH TERRORISTS;
- You’re not alone; remember that. If you have a trusted friend or a family member — ask for their help, or seek professional support and guidance. There’s no shame in that.
The ugly truth is that these abominations prey on the weak — teens and minors. This problem is so prevalent in the US that the FBI issued a national public safety alert on financial sextortion schemes.
Romance fraud

This type of online scam happens when fraudsters create fake personas and establish romantic relationships with their victims to emotionally manipulate them for financial gain.
Their objective is to make a person fall in love with a fake person and start asking to wire them money. It often starts small, but the reasoning for the transfer starts to ramp up and gets more extreme, leading to asking for bigger sums.
How does a romance scam happen:
- Scammers go to dating sites and create fake online profiles to look for victims;
- Once a victim is found, they start building trust and grooming the victim;
- They begin asking for money under different pretexts, like medical emergencies and travel expenses, often leaving the victim emotionally and financially devastated.
Dead giveaways of romance scams:
- Their profile is suited to match your needs perfectly;
- They’re quick to confess their love for you;
- You find yourself you’d do anything to keep them happy;
- Their behavior is dodgy and evasive (e.g., make up excuses not to meet up).
How to avoid a romance scam:
- Protect your privacy by being skeptical of overly flattering or extravagant claims early in a relationship;
- Avoid sharing personal or financial information with someone you’ve just met online;
- Research and verify the identity of individuals you meet online using available resources;
- Be wary of requests for money or financial assistance, especially if they are accompanied by elaborate stories or urgent circumstances.
We’re not talking about someone claiming to be famous on Tinder or using a Photoshopped photo. Regarding internet fraud of the romantic variety, FTC reports that romance scams cost $304 million in damages in 2020, a 50% increase over 2019. We all tend to get lonely and isolated, and scammers know that.
The likely victims can be young and old, and sometimes it can be bad enough that the victim becomes an accessory to a crime. So any talk about gift cards or bitcoin should be a warning sign, a red flag big enough to blot out the sun: this is a romance scam.
Has something similar happened to you, and you’re unsure whether it was plain confidence or a romance scam? Surfshark has researched enough to help you differentiate between the two.
Online investment fraud

Online investment fraud is a scam designed to get money out of you with the promise of huge returns — and it’s had a devastating impact on Americans.
According to the FBI, cybercriminals have stolen more than $5.9B in investment scams over the past decade.
Making its way online from the physical world, investment fraud comes in many forms: emails, ads, malicious sites promoting fake deals, and opportunities that are too good to be true.
Once the bait is swallowed, the online scammer will ask the victim to wire them money directly and as fast as possible. They promise to pay in the future but never will. The aim is to say whatever it takes to lure you into emptying your pockets.
The most common dead giveaways of investment scams are:
- A false sense of urgency (limited time offer, pay now, etc.);
- A too-good-to-be-true offer;
- Low- or no-risk investment opportunities with significant and usually immediate returns.
Crypto scams
The most notable crypto scam is called fake Initial Coin Offerings (ICOs). It’s a type of online scam where scammers create fake ICOs to raise funds for non-existent or fraudulent projects.
They entice investors by promising high returns or exclusive benefits, but once the funds are collected, the scammers disappear without delivering on their promises.
2021 was the year when crypto internet fraud flourished. From an unauthorized Squid Game token making off with the money to a sham initial coin offering to Elon Musk impersonators tricking fans into forking over $2 million (to be fair, targeting Musk fans is a tried and true method dating back to 2018), things were wild all over the spectrum.
Advance-fee fraud — the Nigerian letter scam
Example: pay a small fee to receive your promised “pot of gold.” This scam typically means getting an email or message from someone pretending to be a wealthy individual, royal family member, or government official. The most famous example of such a technique is the Nigerian prince scam.
Scammers promise a large sum in exchange for a small fee or personal information, but it’s a ploy to extract money from the victim.
How to avoid online investment fraud:
- Research and verify the investment opportunity or platform before committing your funds. Verify the company’s legitimacy, check if they are registered with relevant financial authorities, and look for reviews or complaints from other investors;
- Don’t be pressured into making quick investment decisions — scammers create a sense of urgency, so take your time to evaluate investment opportunities and never feel rushed into making a decision;
- Only use secure and reputable investment platforms or brokerage firms with a strong reputation. Make sure they have proper security measures, such as encryption and two-factor authentication;
- Stay informed and educate yourself about different investment types, strategies, and common investment scams. Knowledge is a powerful tool to identify potential fraud and make informed investment decisions;
- Seek professional advice if you’re unsure about an investment opportunity. Consult with a qualified financial advisor or professional who can provide guidance and help you make informed decisions based on your financial goals and risk tolerance;
- Trust your instincts — there’s a high chance of a scam if something doesn’t feel right or seems too good to be true. Don’t let greed or pressure cloud your judgment.
How to avoid online scams in general
There’s an infinite variety of scams in the world. Here’s how you might spot the common types:
- Always reread everything: when it comes to emails and internet services, scammers leave typos and punctuation mistakes. Some of it is to weed out scam-aware people early on. The rest might be due to carelessness.
- Check those website addresses: unless the hackers have hacked an official website, they can’t have the same website address as the real one. Always check the URL for minor deviations from the official title. In emails, you can hover your cursor over buttons and hyperlinks to see the address in the lower left corner.
- Don’t trust random warnings: you should already have an antivirus app installed. If it isn’t freaking out, you shouldn’t be either. If you don’t have an antivirus installed, any warning you see online might be pushing fake antivirus software (or a VPN scam). Instead, get one from an official supplier or a trusted website like CNET or Softpedia.
- Beware of good deals: if a deal seems too good to be true when shopping online, then it probably is. If that isn’t enough for you, search the site’s name to learn more about it, and check reviews on websites like Trustpilot.
- Never give away your sensitive information: as the old saying goes, “We will never ask for your password.” No bank, store, or website will ever need to know your login credentials as they can already do any necessary activities via their service’s backend.
- Remember that big companies won’t call you: nobody is calling you to tell you that your computer has a virus, certainly not Google, Amazon, or Apple. At best, you’d get an email about a security breach.
- Stay frosty with close and personal: confidence frauds rely on shock value and your empathy. We’re not saying not to be empathetic, but be careful, especially when large sums of money are involved.
- Consider CleanWeb: CleanWeb is a free extra feature of Surfshark VPN. When active, it works in the background to shield you from malware. When it comes to everyday use, CleanWeb blocks ads and known malware from downloading.
- Use Alternative ID: Surfshark’s Alternative ID lets you create multiple online personas, complete with names, birthdates, addresses, and emails. Use them instead of your actual personal data to minimize the risk of being targeted for online scams.
And while we’re on the topic, did you know that VPNs can improve passive protection against many types of online scams?
Final thoughts — keep your protections up
Internet scams are an art constantly reinventing itself — remixing the old hits and using different techniques in conjunction. Having read the article, you’re halfway to mounting an effective defense. So why not get Surfshark VPN? It comes with CleanWeb — a feature that helps block malicious ads!
FAQ
Who gets scammed the most?
Basically, everyone gets targeted by scams at least a couple of times a month. All age demographics are experiencing scams similarly, but some age groups get targeted by specific scams:
- Young adults get scammed the most by online shopping scams via social media and fake shopping websites;
- The people in the middle get scammed by business imposters the most;
- The older demographic tends to get scammed the most by tech support scams.
Do banks refund scammed money?
Most banks should refund you if someone scammed you out of your funds, but be sure to read your bank’s policy.
Don’t wait and call your bank as soon as possible to let them know what’s happened and ask them to stop the transfer if there’s still time. If not, try asking for a refund or freeze the bank account.
Before letting the money go through, most banks usually contact you if you transfer money to a shady account. Therefore, you shouldn’t deal with untraceable payments.
Can you track a scammer?
Some scammers reuse their fake credentials, so a person can track a scammer by searching for identifying factors — any used credentials, like email address, phone number, and business name. One can also try to track the scammer by using IP tracking or hiring a private investigator. But we highly advise you to report such things to your local authorities instead of going after them yourself.


