RFID-blocking products claim to prevent wireless pickpocketing. Whether it’s a wallet, bag, or phone case, they all serve the same purpose: to stop thieves from skimming your data when they get close to your RFID-enabled items.
It all sounds promising, but how much protection do they really offer, and are they truly necessary? Figuring all that out helps you understand how RFID works, what these blockers are meant to do, and whether there are better ways to protect your data. Let’s break it down.
What is RFID and why is it used?
RFID (Radio Frequency Identification) is a wireless technology that uses radio waves to identify and track tags attached to objects. Don’t be put off by the fancy name — it’s actually pretty straightforward. Stripped down, it’s just communication between two main components: a reader (also called an interrogator) and a tag (also known as a transponder).
A tag is a small chip or label attached to your item. Inside, there’s a microchip that stores data (such as unique ID or product details), an antenna for sending and receiving signals, and sometimes a built-in power source.
A reader, on the other hand, is a device that sends and picks up radio signals from tags in its range. It activates nearby tags, gathers their data, and typically passes it on to a connected system or database. You’ll find readers built into things like payment terminals, security gates, or even handheld scanners.
Here’s what happens in a typical RFID exchange:
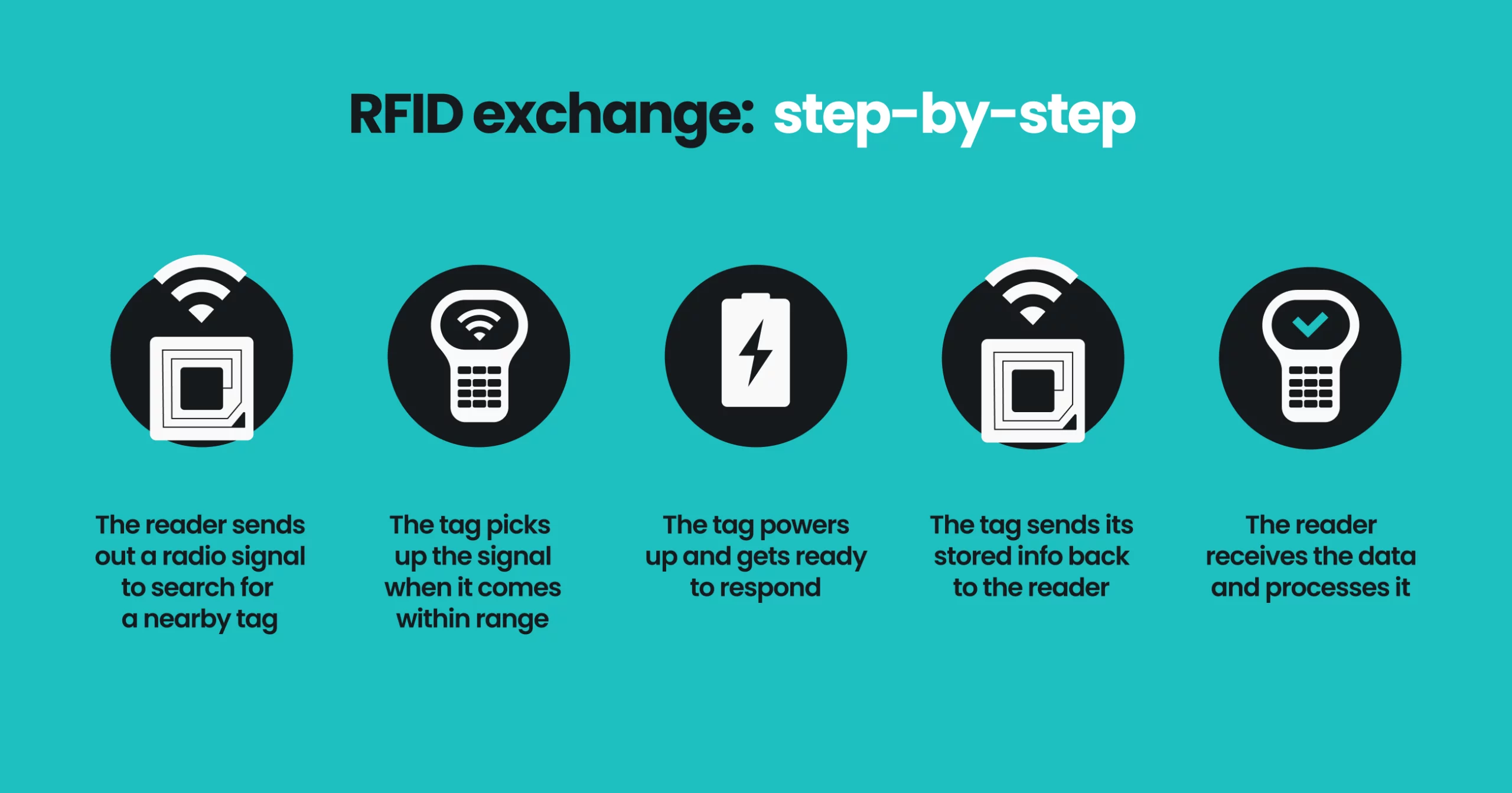
Unlike barcodes, RFID doesn’t need a direct line of sight to work. You can still detect tags even if they’re embedded in objects, buried inside packaging, tucked in wallets, or hidden behind surfaces.
That’s why RFID is used in everything from preventing shoplifting and monitoring medication to keeping tabs on pallets and collecting tolls. Those large-scale uses aside, RFID is also in the everyday items you carry, such as:
- Credit and debit cards that let you tap to pay;
- Access cards and key fobs that unlock doors or gated areas;
- Passports that carry your personal and biometric data;
- Transit cards that keep track of your rides and fares;
- Driver’s licenses and ID cards that allow quick identification.
Handy as it is, RFID makes things quicker and easier. But the price of that convenience is that the tech can be misused. RFID skimming is one example.
How does RFID skimming work?
RFID skimming is a type of digital theft where someone secretly uses a scanner to wirelessly steal data from your RFID-enabled items. It’s also called digital pickpocketing since the thief doesn’t need to lay a hand on you or physically take anything. They just need to get close enough to pick up the signal and grab the data.

While any RFID-based item can be skimmed, the ones people worry about most are tied to identity, access, or money — things like your contactless credit or debit card, office pass, or passport. Depending on what you’re carrying, here’s what a skimmer could grab:
|
Contactless payment card
Card number, expiry date, and sometimes the cardholder’s name. PIN and CVV aren’t exposed. |
E-passport
Basic personal info stored on the chip — like name, date of birth, and passport number — if security measures are bypassed. |
Access card/office badge
Unique ID or code that unlocks doors or grants access to restricted areas. |
|
Transit pass
Card number, balance, and possibly ride history, depending on the system. |
Hotel room key card
Temporary access codes for room and possibly shared facilities like the gym. |
Toll tag
Vehicle or account ID linked to toll billing. |
It might sound a little alarming when you lay it out like that, but just because RFID data can be skimmed doesn’t mean it actually happens often.
Yes, RFID skimming is technically possible. Readers are also cheap, portable, and easy to get. But, in reality, it’s far less common than you might assume. Confirmed cases are so rare that there’s barely any data to go on. It’s also not as simple as just strolling past someone and collecting their data. Here’s why:
|
Short range
|
Most RFID-enabled items only work when a reader is within a few centimeters. A thief would have to get uncomfortably close, enough to raise suspicion or risk being caught on camera.
|
|
Built-in security
|
Plenty of RFID-enabled items come with out-of-the-box protections. For instance, payment cards rely on one-time codes. Meanwhile, e-passports use encryption, BAC (Basic Access Control), and physical shielding.
|
|
Signal interference
|
Stacked, bundled, or moving items — like those in a bag while walking — are much harder to scan. All that movement and overlapping signals tend to throw off the scanner.
|
|
Short activation windows
|
Some RFID chips only stay active for a short time or when deliberately triggered. They don’t constantly broadcast your info. That small window makes drive-by skimming much tougher.
|
|
Incomplete data
|
Even if someone manages to skim something, it’s usually just partial info. Typically, it’s missing critical pieces like PINs, CVVs, passwords, or verification codes, making it hard to exploit.
|
|
Easier methods available
|
Do you really need RFID blocking?
Given how unlikely RFID skimming actually is, it’s fair to wonder if RFID blocking is even worth your time. Well, that depends. It all comes down to what RFID-enabled items you carry, where you use them, and how cautious you like to be.
Before you decide, let’s take a look at the pros and cons of RFID blocking:
|
Pros
|
Cons
|
|
Always-on protection
No setup or maintenance needed. It works quietly in the background. |
Very low real-world risk
If no one’s actively trying to skim your card, there’s really nothing to block. |
|
Minimal effort
Once it’s in place, there’s nothing else you need to manage. |
May be redundant
Many RFID items already have built-in protection like encryption or time-limited access. |
|
Reduces accidental scans
Helps you control what gets scanned and when. This can prevent unintended taps or mix-ups when you’re carrying more than one RFID-enabled item. |
Can create false confidence
Some people might assume it provides blanket protection for all sorts of digital threats, when it actually only blocks a niche type of risk. |
|
Extra layer of privacy
Blocks passive or unauthorized scans that could happen without your knowledge, even if the actual risk is small. |
Can interfere with convenience
It could get in the way of tap-to-pay, entry badges, or transit passes you actually want to use quickly. |
You’re more likely to get the most out of RFID blocking if:
- You’re a frequent traveler with an RFID-enabled e-passport, and want to play it safe at airports or border crossings;
- You’ve experienced — or are concerned about — cloning, unauthorized access, or identity-related issues, and want an extra safeguard;
- You’re already in the market for a new wallet;
- You juggle multiple contactless cards daily;
- You spend a lot of time in crowded public areas, like packed transit or co-working spaces, where close contact is common.
For the average person, though, RFID blocking is probably not a top priority. It just might feel like one sometimes because of confusion or misinformation. So, let’s clear up some of the most common myths and misconceptions.
Claim 1: Someone can drain your bank account just by walking past with a scanner
False. Skimming might capture your card number, but it can’t grab your PIN or CVV — both of which are usually needed to complete a transaction.
Claim 2: RFID skimming is a common threat
False. It’s actually very rare, with limited confirmed cases. Most criminals prefer easier and more profitable methods like phishing, malware, or data breaches.
Claim 3: Every card is RFID-enabled
False. Only cards with contactless features (indicated by the tap-to-pay symbol) use RFID. Many cards, especially older ones, don’t transmit anything at all.
Claim 4: RFID-blocking gear protects you from all digital threats
False. They help reduce the risk of passive scans, but they won’t protect you from phishing, carding, data breaches, or other digital threats.
Claim 5: RFID skimming is how most identity theft happens
False. Identity theft is usually the result of a phishing or smishing attack, a leaked password, a spoofed website, or a compromised database — not from someone sneakily scanning your items in passing. And if skimming is involved, it’s typically from a tampered ATM or payment terminal, not a wireless scan.
RFID blocking wallets vs. RFID blocking cards
If RFID blocking is still on your mind, it’s worth knowing what kinds of tools are out there, how they work, and how they stack up. Two popular options are RFID-blocking wallets and cards. Both are designed to protect your contactless cards, but they suit different needs and preferences.
Here’s how they compare:
|
Feature
|
RFID-blocking wallets
|
RFID-blocking cards
|
|
How it works
|
Lined with shielding materials that block RFID signals. For example, aluminum or nickel.
|
A card that blocks nearby scanners by absorbing or emitting jamming RFID signals.
|
|
Ease of use
|
Just place your cards inside.
|
May need to be positioned close to the cards you want to protect.
|
|
Scope
|
Covers everything stored inside the wallet.
|
Depends on placement. Typically it only protects cards near it.
|
|
Setup
|
Use it like a regular wallet.
|
Slip it into a wallet alongside other cards.
|
|
Durability
|
Depending on materials, some wear down fast.
|
Usually longer-lasting and less prone to physical wear.
|
|
Convenience
|
Ideal if you’re already replacing your wallet.
|
Easy to use with any existing wallet.
|
|
Cost
|
Usually more expensive than a regular wallet.
|
Generally cheaper, but top models can cost more than basic wallets.
|
|
Best for
|
Everyday use, frequent travelers, heavy card users, or anyone buying a new wallet.
|
Minimalists, budget-conscious users, or anyone who wants to keep their current wallet.
|
|
Drawbacks
|
Can be bulky, with limited style choices and fixed carrying capacity. Effectiveness depends on the materials used.
|
Can be easy to forget or misplace, less effective if not positioned correctly, and may need more than one for larger or multi-compartment wallets.
|
RFID blocking while traveling: is it worth it?
You might not think twice about RFID blocking at home. But when you’re traveling — especially internationally — RFID skimming could start to feel like a real concern.
Busy airports, shoulder-to-shoulder tourist hotspots, and unfamiliar systems in foreign countries can make anyone feel vulnerable. Chances are, you’re also carrying your passport and contactless cards — using them to hop on trains, check in at hotels, or pay for food. With so much close contact, it’s easy to feel exposed. That’s when the risk starts to feel a lot more real.
But just like at home, the actual risk remains incredibly low. Most RFID-enabled items already come with built-in protections. Take your passport, for example — it’s encrypted and uses BAC, which means it has to be physically opened and scanned before any data can be read.
Skimming also requires close, steady contact. This is hard to pull off without drawing attention, especially in a fast-moving, crowded space. Plus, when your items are stacked or shifting around in a bag, it’s even harder to scan.
That said, if you’re still feeling uneasy, an RFID-blocking wallet or card can act as a safety net. Just remember not to let it lull you into a false sense of security.
Pro tip: RFID-blocking gear might help with your peace of mind, but it’s not your strongest defense against common travel risks. Use a travel-friendly VPN (Virtual Private Network) to protect your data on public Wi-Fi in places like airports or hotels. Stay sharp around ATMs, card terminals, and self-checkout kiosks. Keep valuables zipped up or tucked into an inner pocket.
Beyond RFID: how to truly protect your identity
For all the worry around RFID skimming, the real threats to your identity usually come from far more common sources. Here are some of the more pressing ones you should watch out for:
- Data breaches: hackers may launch large-scale attacks on companies, services, or apps you use, stealing your personal data to sell on the dark web or commit fraud;
- Phishing scams: scammers often send fake emails or texts, or create websites that look legitimate to trick you into clicking malicious links or giving up sensitive info like login credentials or credit card numbers;
- Identity theft: criminals may use leaked data — such as your name, address, and more — to open bank accounts, take out loans, or hijack your existing services;
- Public Wi-Fi snooping: attackers can intercept the data you send over unsecured networks — including passwords, messages, or payment details;
- Social engineering: malicious actors might impersonate someone you trust — like tech support, a customer service rep, or even a friend — to get you to share personal or financial info;
- Malware and spyware: cybercriminals might hide malicious code in fake apps, email attachments, or sketchy downloads that can steal your keystrokes, passwords, or other sensitive data.
Clearly, the threats go beyond what RFID blocking can protect against. Staying safe means layering smart security habits with powerful tools. So, let’s look at how you can cover your bases.
Follow security best practices
One of the best ways to protect your identity is to start with the basics. Here are a few small steps that can make a difference:
- Use strong, unique passwords with a mix of upper and lowercase letters, numbers, and special characters;
- Turn on 2FA (Two-Factor Authentication) to add an extra layer of protection to your logins;
- Avoid links, attachments, and messages in unsolicited or unexpected emails.
Get a VPN
A reliable VPN like Surfshark is one of your best defenses for protecting your identity and data. It encrypts your internet traffic so others can’t snoop on your sensitive information — whether that’s passwords, credit card details, or private messages. Plus, it hides your browsing activity to limit what advertisers, trackers, and malicious sites can collect about you.
At the same time, Surfshark also masks your real IP (Internet Protocol) address and location. This makes it much harder for bad actors to launch targeted phishing attempts, serve location-based fake virus alerts, or track your online behavior to carry out identity theft, carding, and other personalized scams.
Review account activity
Regularly check your banking, email, and social media accounts for anything unusual. This includes unknown logins, unauthorized charges, or new devices. If something doesn’t look right, act fast to shut things down. Log out of all sessions, change your password, and enable 2FA.
Keep your identity under wraps
Avoid giving out your real details online unless absolutely necessary. Instead, opt for a tool like Surfshark’s Alternative ID, which lets you generate a full online persona — with customizable details such as name, address, and email — to mask your real identity and personal info. You can then use this persona to surf, sign up for services, and receive updates while keeping your data private.
Update your software regularly
Install the latest updates for your device, OS (Operating System), browser, apps, antivirus, and other software. If possible, enable auto-updates so you don’t have to think about them or risk missing one. These updates often fix bugs, patch security flaws hackers could exploit, and improve overall protection.
Monitor data breaches
Consider using tools like Surfshark Alert to keep an eye on your personal info on the web. You can enter details like your email, credit card, and ID info, and Alert will notify you if any of them pop up in a breach, so you can act quickly to minimize the damage. Early detection means you can change compromised passwords, freeze accounts, and notify your service providers — helping you stay a step ahead of identity theft.
RFID blocking is just the tip of it
RFID skimming can happen, but it’s uncommon. Most modern RFID items already have some built-in protection. Plus, criminals usually go for easier wins like phishing scams or big data breaches. Still, an RFID blocker can act as a safety net — especially if you travel often or spend time in crowds. Just remember: it’s one layer of protection, not your entire defense.
Instead, combine RFID blocking with other practical security practices. Use strong, unique passwords and enable 2FA. Stay skeptical and cautious when you’re online. Make the most of tools that help you stay safe. For all-in-one cybersecurity protection that includes a VPN, Alternative ID, and more, check out the Surfshark One bundle.
FAQ
What is RFID blocking material made of?
RFID blocking material is typically made from a combination of metals like aluminum, copper, or nickel, which can absorb or interfere with radio frequency signals. These metals are often woven into fabric or layered between other materials. Sometimes, manufacturers also throw in synthetic fibers like polyester to improve strength, flexibility, and durability.
Is RFID blocking necessary for passports?
RFID blocking is generally not necessary for passports. Modern e-passports already have built-in protections: the chip is encrypted to prevent tampering, digital signatures verify authenticity, and BAC ensures the passport has to be physically opened and scanned before any data can be read.
Can tinfoil really block RFID?
Technically yes, tinfoil can block RFID signals. Aluminum foil can disrupt radio waves, so it might stop a scanner from reading an RFID chip. That said, it’s a flimsy, inconvenient, and unreliable solution. Plus, it’s usually not even necessary. Most modern RFID cards and passports already have built-in security, and actual cases of RFID skimming are extremely rare.
How do RFID-blocking cards work?
RFID-blocking cards work by creating interference that jams or confuses scanners, preventing them from reading nearby cards. Unlike sleeves or wallets that need to cover each card individually, these RFID-blocking cards just need to be placed near your credit, debit, or access cards.
How do I know if my wallet is RFID-blocking?
The easiest way to know if your wallet blocks RFID is to check the label — it’ll usually be clearly marked as “RFID protected” or “RFID blocking” if it offers that feature. You can also try slipping an RFID-enabled card inside and using it at a payment terminal. If it doesn’t work, chances are your wallet’s blocking the signal. For more accurate results, use a dedicated RFID tester.
How common is RFID theft?
RFID theft isn’t very common at all. While the technology exists, actual cases are incredibly hard to find and even harder to prove. Instead, you’re better off focusing on risks like phishing attempts, identity theft, and data breaches.
Does my credit card have RFID?
To check if your credit card has RFID, look for the icon on the front or back of your card. It usually looks like a stack of curved lines, arranged from small to large. If you see this symbol, your card has an RFID chip.



