Proxy servers can be useful, but few know what using them actually entails. In this article, we’ll break down what a proxy server is, why people use them, and how to avoid the risks involved. You’ll also learn how they differ from VPNs (Virtual Private Networks) and why they both have their place in cybersecurity.
Table of contents
What is a proxy server?
A proxy server acts as a middleman between you and a website. When you establish a connection via a proxy server, it forwards your request to the target website and relays the response back to you.
Doing so, it replaces your IP (Internet Protocol) address with its own. This is important from a privacy standpoint since an unprotected IP can be tracked, making it possible to discover your approximate location, build a profile of your browsing habits, or control your browsing access.
How does a proxy server work?
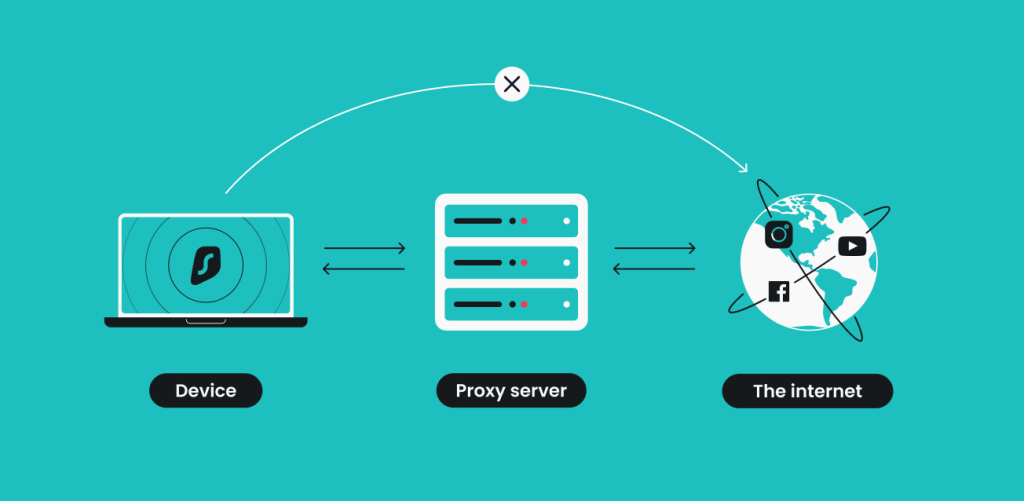
A proxy server intercepts the information you send from your device before passing it on to the requested web server. Once the website responds, the process is reversed. Think of it as a fancier version of a mail-forwarding service.
The full cycle looks like this:
- You enter a website’s address into your browser;
- The proxy server receives your request;
- The proxy server forwards the request to the web server you’re trying to reach;
- The web server sends a response (website data) back to the proxy server;
- The proxy server forwards the response to you.
This process offers several benefits, mostly centered around location changes. However, proxy servers do get more sophisticated, adding encryption methods that increase the security of your requests.
Why use a proxy server?
Proxy servers have several applications. They can be helpful if you want to browse the web without leaving a clear digital footprint, but they’re also useful for network management in businesses or schools:
IP address masking | Proxies hide your real IP address by routing traffic through the proxy server, providing some level of anonymity when accessing websites. |
|---|---|
Bypassing geo-restrictions | Proxies can help you access content that is unavailable to your regular IP. |
Improving performance through caching | Caching proxies store copies of frequently accessed web content, speeding up load times and reducing bandwidth usage for commonly requested resources. |
Content filtering | Proxies can set rules for acceptable internet usage, blocking certain websites or types of content, which is useful in controlled environments like schools or workplaces. |
Bandwidth savings | By caching frequently visited sites and compressing data, proxies can help reduce overall bandwidth consumption. |
Web scraping | Proxies are widely used for web scraping, allowing users to scrape data from websites without revealing their IP addresses or getting blocked. |
Anonymity in simple tasks | Proxies provide basic anonymity when you only need to hide your IP address for low-security tasks like bypassing geo-blocks or accessing certain websites. |
Faster local network access | Companies may use internal proxies to speed up access to internal resources by reducing external internet usage. |
What are the different types of proxy servers?
There are several types of proxy servers, each designed to perform a specific function. Let’s break them down one by one:
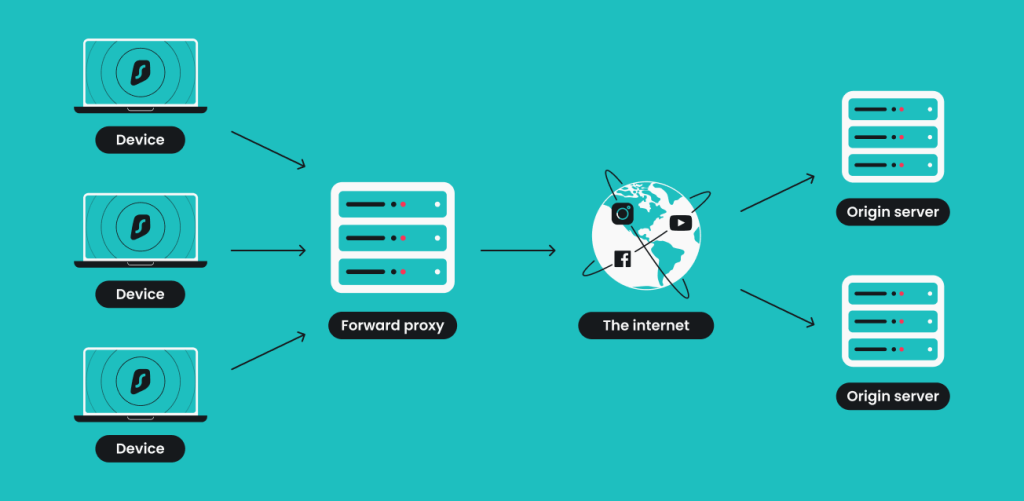
Forward proxy
The most common type of proxy forwards requests from clients to a server and returns the response. Forward proxies are typically used by individuals or organizations to hide their IP addresses, access blocked content, or control internet usage. Besides web traffic, forward proxies can also handle FTP and email requests.
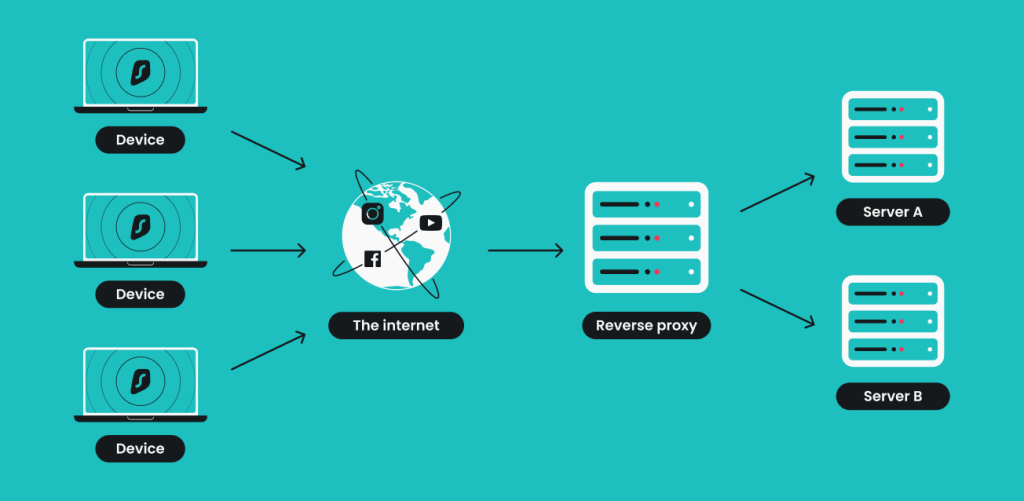
Reverse proxy
A reverse proxy handles clients’ requests on behalf of the server to ensure a smooth user experience and lessen the strain on their service. Besides balancing server load, reverse proxies enhance security by hiding the server’s actual location and improve speed by caching frequently requested content.
Web proxy server
A web proxy is essentially a subset of forward proxies focused solely on browsing and web-related activities. Web proxies can act as load balancers, spreading incoming requests over several servers to keep the service up and make sure a big influx of requests doesn’t crash the server.
Anonymous proxy
An anonymous proxy, sometimes referred to as an anonymizer or a distorting proxy, hides your original IP address and gives you a new one but doesn’t hide the fact that a proxy is in use. While it gives some level of anonymity, your browsing can still be tracked in certain situations, such as by your ISP (Internet Service Provider) or other entities.
High anonymity proxy
Also known as an elite proxy, a high anonymity proxy provides the highest level of privacy by both hiding your IP address entirely and not identifying itself as a proxy. It makes your web traffic appear as though it’s coming from a regular user rather than through a proxy server.
Transparent proxy
A transparent proxy is invisible to users and websites. It doesn’t hide your IP address and is often used for content filtering or caching by schools, businesses, or ISPs. Since it doesn’t mask your identity, it’s not useful for privacy or bypassing restrictions.
CGI proxy
CGI (Common Gateway Interface) proxy technology adds an additional step to the equation by connecting to a proxy via a website. Because a CGI proxy allows access to web pages through a web form, it’s a quick method for hiding your IP address. However, performance can be slow, and the proxy is visible to the website you’re visiting.
Suffix proxy
Suffix proxy adds its own suffix to the website’s address to overcome firewall filters. It’s a simple tool but limited in use and easy to detect and block. Also, it doesn’t provide any privacy or security features.
DNS proxy
Computers use DNS (Domain Name System) servers to translate web addresses into numbers — from surfshark.com to 104.18.120.34, for example. A DNS proxy forwards DNS requests, enabling users to reroute their traffic without changing the entire connection settings. It can be useful for optimizing speed, as it allows for connecting to a DNS server closer to the user.
Datacenter proxy
Datacenter proxies originate from a corporate-owned data center. They offer fast speeds but are easy for websites to detect and block since they don’t come from residential IPs. They’re mainly used for high-volume activities like web scraping or automated tasks.
Residential proxy
A residential proxy uses IP addresses assigned to actual devices, making your traffic appear as though it’s coming from a real user in a specific location. These proxies are harder to detect and block, making them ideal for more stealthy browsing or bypassing geo-blocks.
Rotating proxy
A rotating proxy assigns you a new IP address for each connection request or after a certain amount of time. This provides high anonymity and is especially useful for web scraping, avoiding detection, or accessing content across multiple regions.
SSL proxy
SSL proxies provide extra protection by encrypting traffic. They are common where sensitive information, like financial data or personal details, is involved, ensuring it remains secure while in transit between the client and server.
What protocols do proxy servers use?
Proxy servers rely on specific protocols to manage traffic between clients and servers. These protocols dictate how requests are sent, processed, and forwarded. Let’s break down the most common ones:
- HTTP (HyperText Transfer Protocol): the standard protocol used by most web proxies. HTTP proxies handle traffic for websites and web-based applications. However, this also means they are limited to standard, unencrypted web browsing and won’t protect your data if you’re using HTTPS (the secure version of HTTP);
- HTTPS (HyperText Transfer Protocol Secure): it encrypts data sent between the client and the server, making it safer to browse sensitive websites like banking platforms or online stores. HTTPS proxies are ideal for users concerned about data privacy and security;
- SOCKS (Socket Secure): these proxies operate at a lower level than HTTP/HTTPS proxies. They can handle more types of traffic, including email, FTP, and torrent connections. This makes SOCKS proxies more versatile, but they typically don’t provide encryption, which can leave your data vulnerable;
- FTP (File Transfer Protocol): used specifically for managing file transfers over the internet. They help with accessing FTP servers to upload, download, or share files while managing bandwidth and network resources more efficiently;
- WebSocket: used for real-time communication between a client and server. Proxies supporting WebSocket allow continuous communication channels, which are commonly used in web applications like chat services or online gaming.
Each of these protocols serves different purposes depending on the type of traffic, security requirements, and performance needs.
What are the risks of using a proxy server?
While proxy servers offer several benefits, they’re not without their drawbacks — especially if you’re using an unsecured or poorly configured one. Here’s what you need to know:
- Lack of encryption: most proxies, especially free ones, don’t offer encryption. This means your data is still vulnerable to interception, particularly on public networks. Without encryption, sensitive information like passwords, financial details, or personal messages could be exposed to hackers.
- Data logging: some proxy providers may log your activity. If you’re using a free proxy service, there’s a good chance it tracks and stores your browsing data (just like a free VPN would). This information could be sold to third parties, used for targeted ads, or worse — fall into the hands of cybercriminals.
- Unreliable performance: free proxies, in particular, tend to have poor reliability. They often offer slow speeds, frequent downtime, and limited bandwidth. This can not only be frustrating when you’re trying to stream or download files, but it also opens you up to additional security risks if your connection suddenly drops.
- Malware injections: proxy servers can be used as a vector for malware. Malicious proxies may inject harmful code into the websites you visit, infecting your device without your knowledge. This risk is higher when using unsecured or untrustworthy proxies.
- No privacy guarantee: although a proxy hides your IP address, it doesn’t provide full privacy. Your ISP can still see what you’re doing, and if the proxy itself is compromised or not properly secured, your activity could be exposed.
- Legal concerns: depending on where you are and what you’re using the proxy for, you could run into legal issues. Some governments monitor the use of proxies and have restrictions in place for bypassing content blocks or accessing certain information.
Using a proxy without understanding these risks can lead to serious privacy and security vulnerabilities. It’s essential to weigh these concerns carefully, especially when dealing with sensitive data or relying on a free service.
What are the main differences between a VPN and a proxy?
While both VPNs and proxy servers help protect your privacy and provide ways to bypass restrictions, they differ significantly in how they work and what they offer. Here’s a breakdown of the VPN vs. proxy debate:
Proxy | VPN | |
|---|---|---|
Encryption | Proxies provide little to no encryption, with only HTTPS proxies offering limited encryption for web browsing. Most proxy types (such as HTTP and SOCKS proxies) do not encrypt your traffic, leaving your data vulnerable. | VPNs offer comprehensive encryption for all your internet traffic and use robust protocols (such as AES-256) to ensure your data is secure and protected from all third parties. |
Coverage | Proxies offer limited coverage because they usually only protect traffic from specific applications (like web browsers) or devices. They do not encrypt traffic, meaning they provide limited security coverage. If you want to protect multiple devices or ensure all types of traffic are covered, a proxy is not sufficient. | Provide system-wide coverage, protecting all applications (not just your web browser), and can be used across multiple platforms. VPNs also offer global server networks, advanced security features, and multi-device support, making them a much better option for privacy and security coverage. |
Protection | Offer basic protection when browsing the web by IP masking but minimal against cyberthreats like man-in-the-middle attacks, data interception, or DNS hijacking. Free or public proxies may even inject ads or malware into your connection, and they typically log your data. | Provide far superior protection through comprehensive encryption of all internet traffic, no-logs policies, and extra security features like kill switches and DNS leak protection. VPNs offer system-wide protection across all applications and are much better at maintaining privacy and defending against cyberthreats. |
Anonymity | Provide basic anonymity by hiding your IP address for web browsers, but do not encrypt your data, making them less secure and less anonymous than VPNs. | VPNs offer much greater anonymity because they encrypt all your internet traffic, prevent data leaks, and ensure system-wide protection, not just for individual apps. |
Speed | Usually faster because they don’t encrypt your data, but this only applies to web-related traffic (such as HTTP/HTTPS requests). Free or overloaded proxies can slow your connection significantly. | Can impact your connection speed due to encryption overhead, but most reliable ones use refined protocols like WireGuard, which makes the difference negligible. |
Cost | Might be a cost-effective option if you only need to mask your IP address for basic tasks like accessing websites. If you require full privacy and smart encryption of all internet traffic (not just web browsing), a proxy won’t offer the same value as a VPN. | Typically more expensive but offer better performance and system-wide protection, making them the more practical choice. Also tend to have no-logs policies and better privacy protections. |
Another alternative is to use Remote Desktop Protocol (RDP) to browse from a completely different computer; however, RDP differs from a VPN in much the same way a proxy does — it provides little to no encryption.
Bottom line: proxies have their place but are limited
Proxies are a quick way to bypass geo-restrictions, hide your IP, or access blocked websites. They’re simple, often free, and provide basic anonymity that can get the job done in limited scenarios.
But when it comes to security and privacy, proxies fall short. Most don’t encrypt your traffic, leaving your data vulnerable to eavesdropping or logging. The lack of comprehensive coverage means you’re only protecting certain apps and not your entire internet activity.
If you need something more robust — something that encrypts your data, secures all your online traffic, and provides a high level of anonymity — a VPN is the better option. VPNs offer an all-in-one solution that combines privacy, security, and speed without sacrificing convenience.
FAQ
What do proxy servers do?
Proxy servers act as intermediaries between your device and the internet, routing your web traffic through an external server. They help hide your IP address, provide some anonymity, and can also manage or filter your internet traffic.
What is a proxy server for Wi-Fi?
A proxy server for Wi-Fi reroutes your internet traffic through an intermediary server when connected to a wireless network. This can provide extra privacy, control, or faster access to cached content, depending on the proxy configuration.
Is it OK to use a free proxy server?
Using a free proxy server can be risky since many don’t offer encryption and may log your data, putting your privacy at risk. For better security and privacy, it’s safer to opt for a paid proxy server or trusted service.
Should I keep my proxy server on or off?
You should keep a proxy server on if you want to hide your IP address, increase privacy, or manage web access. If you don’t need these features, it can be turned off to avoid potential slowdowns or connection issues.
How do proxies hide IP addresses?
Proxies hide your IP address by replacing it with their own. Websites see the proxy server’s IP instead of your device’s, making it harder to trace your online activity back to you.
Are proxy servers legal?
Yes, proxy servers are legal in most places, but how you use them matters. Accessing restricted content via proxy can violate terms of service.
Do I have a proxy server?
You can check if you’re using a proxy by looking at your device’s network settings. If a proxy server is configured, the details will appear under your network or browser settings.
What is the difference between a firewall and a proxy server?
A firewall protects your network by blocking unauthorized traffic and filtering data. A proxy server, on the other hand, routes your traffic through an intermediary, providing privacy by hiding your IP address and sometimes filtering content.
What is an open proxy?
An open proxy is a publicly available proxy server that acts as an intermediary between you (your device) and the internet (websites). Open proxy routes your internet traffic through its server, masking your IP and anonymizing your connection to the website you’re visiting. However, open proxies come with significant security risks, so consider using a trustworthy VPN instead.