
Phishing attacks like the classic Nigerian prince scam are still alive and kicking, so it’s vital to understand these online menaces and how to best protect yourself against them.
Table of content
What is phishing, and why is it dangerous?
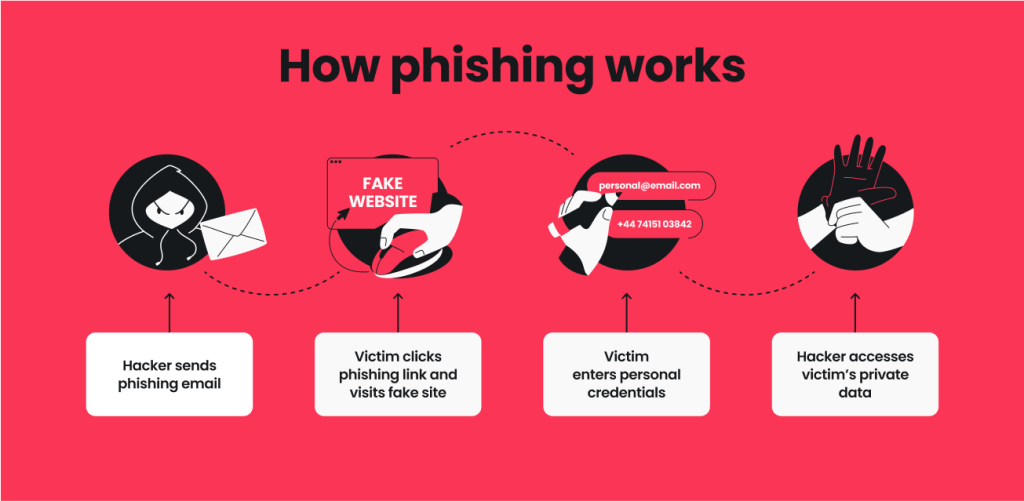
Phishing is a type of attack where cybercriminals trick people into sharing sensitive information like usernames, passwords, or credit card details by posing as a reliable source.
They accomplish this by sending fraudulent emails or text messages or by creating fake websites to lure victims in.
Why is phishing dangerous?
Phishing attempts can lead to financial loss, identity theft, and unauthorized access to your most important accounts. Attackers can even install malware onto your device, meaning unsuspecting users might face system damage and performance issues.
What are the most common indicators of a phishing attempt?
Phishing is meant to be sneaky and misleading, but that doesn’t mean it’s impossible to spot. Let’s examine the tell-tale signs of a phishing email so you know what to look out for. Since phishing can be particularly harmful for companies — with the average data breach cost hitting $4.45 million — here’s a suspicious work email as an example.
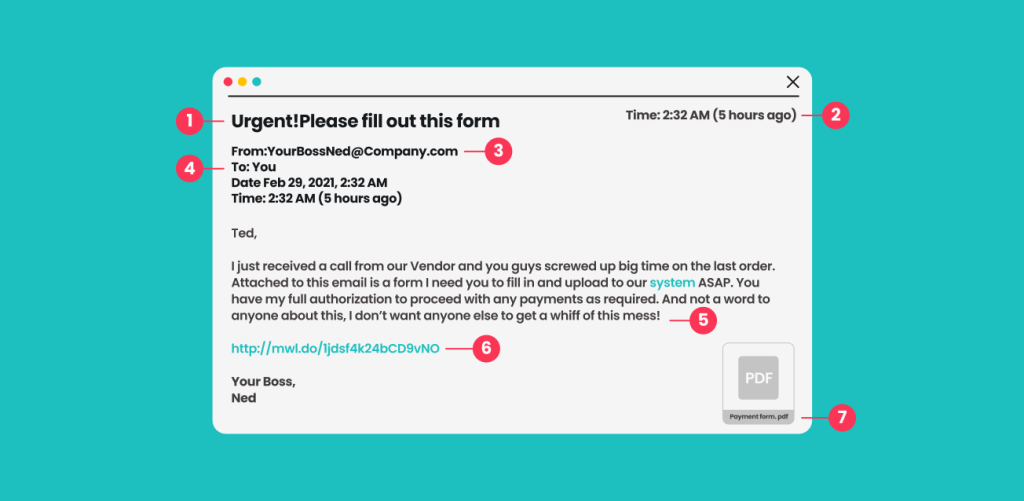
-
Subject line
- Sense of urgency: phishing emails frequently make victims think that time is running out, forcing them to act impulsively and irrationally;
- Mismatch between subject and body: cybercriminals aren’t Shakespeare. Phishing messages are usually poorly written and have disjointed elements hastily thrown together.
-
Date and time
- Unusual time: attackers are active around the clock, so many messages come in at night or outside standard working hours;
- Inappropriate day: governments, financial institutions, and most legitimate companies don’t send important notifications on holidays or over the weekend.
-
Sender
- Unknown sender: phishing emails often appear to come from strangers. If they claim to be someone you know, they might be writing in an inconsistent tone or style;
- Suspicious domain: are you familiar with the sender’s email domain, or does it look slightly off? Typos or domains you’ve never seen before are a major red flag.
-
Recipient
- Random CC chain: did anyone else receive this email? A list of other random addresses next to yours is a good indicator of a phishing scam;
- Generic greeting: check how the email starts. Be wary if all you see is a vague Hi without your name or anything to identify you specifically.
-
Body
- Typos and mistakes: phishing scams are notorious for poor grammar, spelling, you name it. Steer clear of any messages that are riddled with errors;
- Financial promises: has anyone you know ever won anything over email? If it sounds too good to be true, it most likely is;
- Threats: phishing emails commonly prey on your emotions. Don’t buy into any attempts to scare or intimidate you.
-
Hyperlinks
- Unfamiliar hyperlinks: hover your mouse over a link to see if it takes you to a credible website or is just a random string of letters and numbers;
- Incorrect hyperlinks: if a link includes a name you’re familiar with, double-check the domain and suffix. There’s a world of difference between nyke.co and nike.com.
-
Attachment
- Uncommon file type: attachments that are .exe files can be used to trick people into downloading malware;
- Strange file name: is the attachment named something generic like Document.pdf? Or does it have a double extension like Invoice.doc.exe? Stay away from these at all costs.
The most common phishing examples
Phishing attacks come in all shapes and sizes. Here are the different types you’re most likely to encounter:
Email phishing
Phishing emails involve attackers sending fraudulent emails that appear to come from credible, authoritative sources. Also known as spam phishing, these messages trick users into clicking malicious links, scanning phony QR codes, or sharing sensitive data like passwords or bank account numbers.
Spear phishing
Spear phishing is a form of phishing in which hackers send personalized messages to a specific person or organization. These are often more difficult to detect and more effective at convincing targeted users to divulge personal information.
Whaling
Whaling is a type of spear phishing aimed at high-profile targets, like company executives or senior officials. Attackers trick these prominent figures into sharing confidential financial information that can be exploited for extortion or monetary gain.
Smishing (SMS phishing)
Smishing attacks are phishing campaigns executed through SMS or text messages to your cell phone. Scammers frequently pose as mobile carriers or other legitimate sources and send messages containing harmful links or requests for sensitive data.
Vishing (Voice phishing)
Vishing involves attackers calling you to extract personal or financial information over the phone. On top of pretending to be from some authoritative body, scammers commonly claim to be friends or family members needing assistance.
Clone phishing
In clone phishing, attackers create a copy of a genuine email the victim has already received and alter links or attachments to redirect them to malicious content. These can be especially difficult to detect since they look like they’re from a person or company you’re regularly in touch with.
Pharming
Pharming is a phishing technique that redirects users from a legitimate website to a fake one, tricking them into entering personally identifiable information. Rather than clicking a malicious link, pharming has a user download malware without their knowledge.
Search engine phishing
Search engine phishing occurs when hackers create bogus websites that come up in search engine results. By making their malicious website or product the top hit for popular search terms, attackers lure victims to pages where they’ll enter personal details or credit card data.
Social media phishing
Social media phishing takes place when scammers create fake profiles on Facebook, Instagram, etc., and send deceptive messages that prompt victims to reveal sensitive data. Angler phishing is a specific attack that involves cybercriminals creating fake customer service accounts and responding to user complaints or inquiries over social media.
What to do in case of a phishing attack
If you’ve clicked on a phishing link or downloaded a suspicious attachment, don’t panic just yet. Here are some simple steps you can take to combat phishing and minimize its harmful effects moving forward:
- Change your passwords: passwords may be compromised during phishing attempts or data leaks. If you think you’re vulnerable, change all your passwords routinely (every three months is a good rule of thumb);
- Scan your devices for malware: run a thorough scan of your devices using anti-malware or antivirus software (like Surfshark Antivirus) to detect and remove any malicious programs;
- Monitor your financial accounts: check your bank accounts for suspicious activity or unauthorized transactions, which could indicate a carding scam. If anything catches your eye, promptly report it to mitigate any monetary loss.
- Back up your data: create copies of important files and move sensitive data to a secure location. That way, you’ll have a backup of all your essentials in case an attack targets you.
- Be vigilant on messaging apps: report any suspicious messages or users if you suspect phishing, as it’s one of the most common scams on Telegram and other similar apps.
How to prevent phishing attacks
You can effectively avoid a phishing attack with these common-sense measures:
- Use a VPN (Virtual Private Network): a VPN like Surfshark encrypts your internet traffic, making it harder for attackers to read or intercept your data, including personal and financial information you may enter online;
- Enable MFA (Multi-factor Authentication): MFA adds a security layer to your password. Even if your login credentials get stolen, scammers will have a tougher time accessing your accounts;
- Stay alert: don’t take unnecessary risks online. Never click on suspicious email links or give another person full access to your accounts. Better yet, take advantage of tools like Surfshark’s email scam checker to scan messages in your Gmail inbox for possible phishing attacks;
- Educate yourself: Phishing techniques are constantly evolving. Read up on these cybercrimes to boost your phishing awareness and learn about new anti-phishing strategies.
Give yourself advanced phishing protection
Phishing is ultimately based on human error, so staying safe is all about being cautious and up-to-date on the latest scams.
Thankfully, you can level up your online security with tools like a VPN that blocks access to many phishing sites. Better still, solutions like Surfshark come with Alternative ID, software that helps you avoid spam and data leaks by generating a new email address and online identity.
While no service is 100% effective against phishing, a VPN like Surfshark is the key to browsing with more confidence.
Phishing FAQs
What is phishing in simple terms?
Phishing is an online scam in which attackers send deceptive messages, usually via email, to trick people into sharing personal information or giving away money.
How can you prevent phishing attacks in an organization?
Follow these steps to prevent phishing in an organization or company:
- Use anti-phishing software: equip your team with tools like a VPN and antivirus;
- Educate employees: conduct regular training on what phishing looks like;
- Establish clear policies: create guidelines team members can follow when handling suspicious emails.
How can you recognize phishing emails?
Use these techniques to recognize phishing emails effectively:
- Check the sender: note unfamiliar addresses, strange domains, and unusual sending times;
- Look for errors: phishing messages tend to have spelling and grammar mistakes;
- Watch out for urgency: pay attention to urgent requests, intimidation, and threats;
- Verify links: hover over links to check where they’ll take you, and don’t click on anything unless you’re sure.
What is the most common phishing attempt?
The most common phishing attempt is an email posing as a trusted source — such as a bank, online service, or even a government agency — designed to trick you into revealing personal or financial information. One of the most well-known examples is the Nigerian prince scam, where the sender promises a large reward in exchange for your help and banking details.




