
Spear phishing is a form of phishing that uses personalized emails, calls, or SMS texts to approach specific individuals and organizations with malicious intent. Spear phishing is an especially devastating cyberattack because it uses personal information to spin believable stories and exploit people emotionally.
Table of contents
What is spear phishing vs. phishing?
Phishing is a general term for a hacker trying to trick someone into sharing their credentials, credit card information, or other work and personal data they can use for monetary gain. It is usually carried out via fake emails, texts (smishing), or phone call.
Spear phishing is essentially the same thing, except that attackers use their victims’ personal information to make their cyberattacks seem more genuine, trustworthy, and persuasive.
In short, if phishing was apples, then spear phishing would be Granny Smith, URL phishing – Golden Delicious, Smishing – Pink Lady, and so on.
What does a spear phishing attack look like?
Let’s take a look at a hypothetical example of a spear-phishing attempt.
Scenario: A college student loves to listen to music on Spotify. One day he decides to post a screenshot of his favorite song on Twitter captioned, “I can’t stop listening to this, lol.” A cybercriminal scrolling his feed comes across this post. He then goes on Facebook to see if he can find the student’s profile.
Unsurprisingly, he does. Here, our attacker learns his soon-to-be victim’s email address, that he is a student at a local college, got his first car on his 18th birthday, and has been on a family trip to Bali before.
Spear phishing: Having everything he needs, the cybercriminal puts together the following email using a spoofed domain:
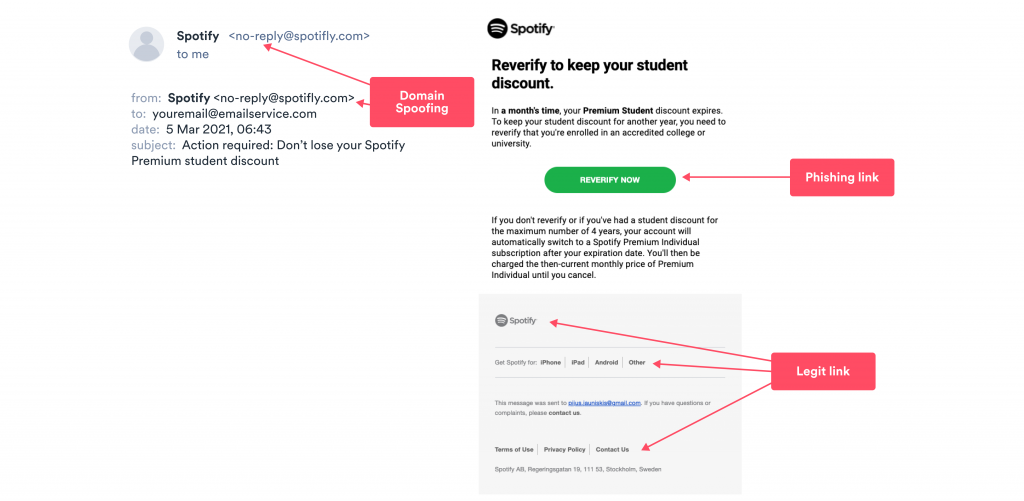
The email was replicated after a legit Spotify notification. The only differences are that the attacker sent the message from a spoofed domain <no-reply@spotifly.com> and changed the link to a phishing one on the green “Reverify Now” button. Instead of leading to Spotify’s web page, the link will redirect anyone who clicks it to a clone site that the attacker built to gather people’s info.
Payout: The student does not want to lose his discount and clicks the button after receiving the email. On the cloned site, he is asked to re-enter his credit card information and choose his college as proof that he’s a student.
Through a successful spear phishing attempt, the attacker now has the student’s name, address, credit card information, and a possible security question (first car). The hacker can sell this data on the dark web or use it to create duplicates of the card and make purchases using fake ones.
What makes spear phishing attacks so dangerous?
That was a single example of one person becoming victim to a targeted cyberattack. However, individuals are not the only ones in danger of spear phishing. Quite the opposite, in fact.
According to Symantec’s 2019 report, 65% of all known cybercriminal groups use spear phishing for gathering intelligence. This is also one of the main reasons why 95% of attacks on business networks result from spear phishing.
What’s the catch? Simple, spear phishing attacks are so effective because they:
- Appear authentic, just like any other work-related email you’d get.
- Fit in the context. A work-related spear phishing email may be sent during work hours and have appropriate subjects. This is also known as a Business Email Compromise (BEC) – a form of spear phishing when an attacker poses as someone working in the company.
- Reach the target personally. Spear phishing attacks don’t come in email chains or appear spam-sent to many different people.
- Are covered with legitimate links, which allows them to bypass workplace and personal email security systems.
What helps protect from spear phishing?
Preventing spear phishing is extremely difficult due to its slippery nature. However, there are a few things you can do to minimize the chances of it happening in the first place:
For individuals:
- Educate yourself to recognize phishing threats.
- Understand that spear phishing plays into emotions and susceptibility to authority.
- Stop leaving your fingerprints and personal information all over the web and social media.
- Don’t share sensitive information via emails.
For workplaces:
- Do not openly list employees’ email addresses.
- Train and educate everyone in the organization to spot phishing.
- Make sure you perform routine scans on the web for leaked emails or credentials.
- And again, don’t share sensitive information via emails.
Tip: Since most phishing occurs via email, using an alias may lower the risk of being spear-phished.
Using Surfshark’s Alternative ID, you can generate a complete online persona with identity credentials and an alternative email address. You can then use this information for sign-ups and registrations on websites and services you don’t fully trust. Your regular identity stays private, cutting off the personal information spear phishers need to craft convincing attacks.
What is whaling, and how is it different from spear phishing?
Whaling is a form of spear phishing that targets CEOs, CMOs, COOs, or other top-level executives.
The goal is usually to get hold of credentials that would provide the attacker with full system access to the company’s resources. The more defenses you can bypass, the more money you can steal or extort later.
In short, if phishing was apples and spearing phishing Granny Smiths, then whaling would be a gourmet apple pie topped with whipped crème de la crème.
Only you can prevent phishing
The formula to avoid phishing is actually quite simple – no click, no problem.
In the case of social engineering – ignorance is far from bliss. Knowledge here is your best friend and defense, so you know what to look for and avoid in emails, messages, or phone calls. Educate yourself and increase your phishing awareness (don’t worry, we’ll guide you through it)!

