Online security became paramount thanks to Covid-19 putting both our work and parties at home. People turned to VPN en masse. Many businesses started looking for VPN alternatives (Virtual Private Network) for their remote access needs, so the past years gave birth to various options to defend yourself on the web.
Whether you’re looking for different ways to protect your privacy or increase network security at your business, this article is just for you.
Table of contents
What can I use instead of a VPN?
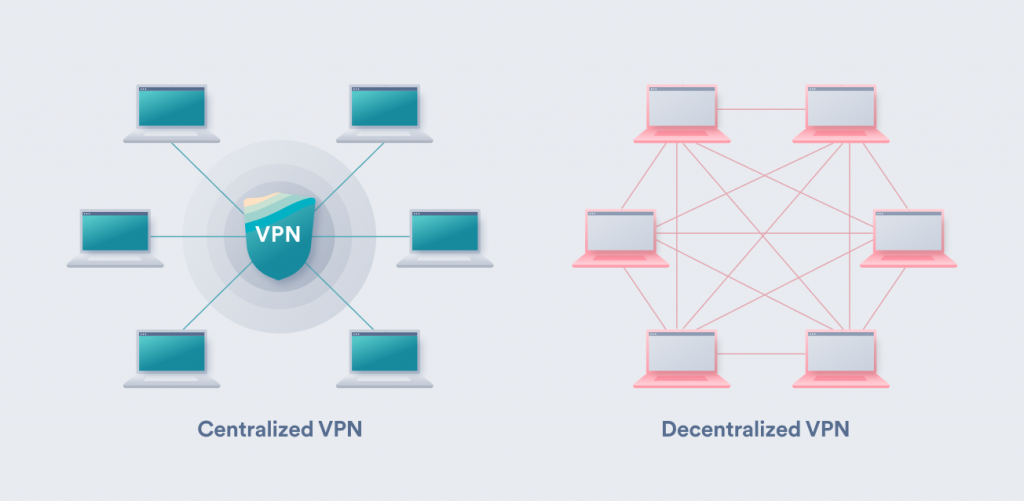
A VPN establishes an encrypted communication tunnel to the internet by rerouting your data traffic through its servers. All you need to do to achieve network-wide security is to log in to your client and run the app.
But even the best personal VPN might not be the right choice for a company. That’s why you should look into these bad boys if you want to protect your business.
-
Zero trust network access (ZTNA)
Zero trust means even you can’t be trusted. It’s a security measure mainly advertised for and used by companies. It’s a paranoid VPN alternative that:
- Blocks all traffic by default;
- Gives access to specific applications;
- Uses multi-factor authentication (MFA);
- Monitors all activity on the network;
- Requires all network users to be continuously validated for security configuration;
- Operates on the principle of least privilege — doesn’t give privileged access management to anyone in the network by default.
In layperson’s terms, to access the private networks further, you must revalidate yourself on almost every other step. You’re a threat from the program’s perspective, and your device is already a security liability — ergo, the constant re-authorization and “zero-trust” bit.
When this measure protects the network, the administrator authenticates remote users and monitors devices for security risks on and off the network. Another neat upside is that the net user can’t show their IP address outside the network’s perimeter (even when on the internet).
Verdict: ZTNA’s a safe security option keeping your company assets close to your chest (even if paranoically so). It’s a step up from hardware VPNs. But ZTNA isn’t adapted yet for easy home use and isn’t as convenient as VPN apps.
-
Secure access service edge (SASE)
A couple of security solutions wearing a SASE (read: sassy) trenchcoat. The idea is to combine many services into a single, cloud-based security service.
SDN + SWG + CASB + FWaaS + ZTNA = SASE
Let’s go over each program hiding under the sassy coat to understand what SASE does.
Software-defined networking (SDN) — a network that’s managed via software.
Security web gateway (SWG) — prevents unsecured (possibly malicious) data traffic from entering a network.
Cloud access security brokers (CASBs) are “sensitive” points between the service provider and user that trigger different security policies once cloud-based resources are accessed.
The policies are: user authentication, authorization, single sign-on, credential mapping, device profiling, encryption, tokenization, logging, alerting, and malware detection/prevention.
Firewall as a service (FWaaS) — a firewall on your computer inspects and filters your data traffic. And FWaaS is the same concept but adapted to the cloud to make cloud computing more secure.
Zero trust network access (ZTNA) — as explained above, it’s a strict security option that prevents users from seeing anything they don’t have permission to access.
Verdict: Like a VPC (Virtual Private Cloud) and other cloud-based technologies, SASE is a relatively new security option. It’s designed to be an approachable, all-in-one solution for large companies.
However, due to it being fresh, troubleshooting may be harder, and managing the internal network can be a hassle. SASE might overlap with other security measures (like recently implemented SD-WAN) and cause performance issues.
To learn more, read our SASE vs. VPN comparison.
-
Proxy servers
When comparing a VPN vs. a proxy, both are similar in one regard — they reroute your data and change your IP address (Internet Protocol). But let’s talk proxy. This service means that another server on the web represents your device by proxy (pun intended).
Your internet service provider (ISP) gives you a distinct IP depending on your location. Your browser uses your IP to send requests to every server it contacts on the web.
When you use a proxy, your data traffic travels through their servers and gets a new IP. This is a good way to circumvent geoblocking and escape IP tracking (and all that comes with it).
There’s an ample number of proxies used for different purposes with different protocols, but I’ll only mention the topical ones further along in this article. For our purposes, it’s enough to know that SOCKS5 is a commonly accepted proxy standard these days.
Verdict: using a proxy server will give you a new IP, which is an excellent way to find markets with lower prices and find a way around geographical restrictions on the web.
HOWEVER, aside from IP change, a proxy doesn’t provide any security on the web or your network.
-
Smart domain name system (DNS)
Smart DNS has some similarities to a VPN — it’s a service that uses both DNS servers and proxy ones to change your DNS address. Some refer to it as a DNS proxy.
DNS is the phone book of the internet. It translates the website’s address (e.g., www.surfshark.com) that you can remember into an IP address computers and other devices can use.
A smart DNS service is programmed to know which websites and services to route via proxy server. It also forces the websites you visit to look at your new-found DNS address first, which is usually enough to circumvent ISP-issued geo-blocks.
However, security-wise, it offers nothing. Your IP is still the same and can be seen by more tenacious service providers.
Verdict: smart DNS is an excellent option to get over a geo-restriction when your device doesn’t support a VPN. However, it offers no protection.
-
Shadowsocks
It’s a semi-proxy service whose main purpose is to dig under some restrictions and censorship (hint: it has something to do with Asian walls). Founded by a Chinese programmer, this service has an exciting founding history.
Shadowsocks is not entirely a proxy but an app that connects to a SOCKS5 proxy server. But the proxy itself differs from others by offering a combo of three authentication methods:
- Null authentication — no authentication is necessary when connecting to a proxy. Your password’s accepted without checking;
- Username/password authentication — the password is accepted as long as it corresponds with the username you gave;
- GSS-API authentication — it’s a process where two or more computers (your device and the server you’re trying to reach) use the same authentication methods to verify your identity.
Shadowsocks, paired with SOCKS5, funnels your traffic through a remote server and changes your IP address before your data reaches the services you want to get to.
Verdict: Shadowsocks changes your IP and helps you hide your location, but it won’t secure your traffic. Its thin veil of security easily crumbles under deep packet inspection (DPI) tools (if somebody were to use them).
Might be great for individual use to overcome web restrictions, but Shadowsocks isn’t a good security option when managing your business network.
-
SSH Tunnel
SSH tunneling, or SSH port forwarding, means transferring any data (referred to as arbitrary data) over an encrypted SSH channel.
What is SSH?
Secure shell protocol that uses cryptography. A shell is a program where the commands are issued via text rather than a mouse, keyboard, or touchscreen. You can log in to your shell from a device that’s not yours — and that’s the basis for secure remote work with SSH.
Note: SSH connects you to a specific device. SSH sounds similar to a VPN, but SSH connects to a particular device, whereas a VPN connects to a network.
What is port forwarding?
Port forwarding lets servers from the internet access devices on a private network. Once data from the internet reaches a device, port forwarding redirects it through a specific entry place on the device — a port.
What is SSH port forwarding / SSH tunneling?
This lets you forward data via an encrypted tunnel from another client application running on the same computer as a secure shell client. Thanks to its cryptography and ability to connect directly, this security protocol can also be used to go over firewalls.
Verdict: SSH tunneling is a great security measure when looking at software VPN alternatives for a business. It encrypts your data passing through the SSH channels. Also, individual use of SSH tunneling is possible, but it requires knowledge.
There aren’t many drawbacks — SSH tunneling secures only the part of the data that goes through its client, and server-wide implementation requires experienced personnel.
-
Tor
The Onion Router (Tor) is a good solution for individual users. In function, it’s close to a VPN, but one that chooses more privacy instead of usability or speed.
What is Tor, in short, please?
Tor works via the Tor Browser (a customized version of Firefox) that allows the user to connect to the volunteer-run network of Tor servers. These two components are used to make your connections to the wider internet a lot more private; plus, it lets you access websites hosted on the Tor network and inaccessible via the regular World Wide Web.
How Tor works
Tor uses a group of layered private servers (volunteers offering their computers) to route and encrypt your internet traffic through the internet:
- It connects with a list of available nodes in the network spanning across the world;
- The data is funneled through a series of three random TOR nodes. Each of these is different from one another and has a unique encryption key:
- The entry node knows the user and the relay node;
- The relay node knows the entry and exit nodes;
- The exit node knows the relay node and the destination.
Because of the network’s architecture, no single computer knows where the data flow origin and final destination points are — your identity and IP are safe.
However, Tor has some downsides:
- It is slow: VPNs slow down your connection a bit because they route your data via an additional server. Tor routes via three servers, all of which can be very far from each other. This can mean serious drops in connection speeds;
- You can’t choose the server: the node choice is usually randomized, so you can’t really choose the exit server, meaning you can’t obtain the IP on the country you want;
- No obfuscation: even if your internet service provider can’t see what you’re browsing, they can still see you using Tor, which is illegal in some countries.
Verdict: Thanks to its unique infrastructure, ToR is a fantastic privacy tool for individual use. But its greatest asset is its bottleneck. While we agree with the internet being free and accessible for anyone, we also think there’s a simpler and faster way to secure your online presence, especially if you’re running an enterprise.
Why would you use a VPN alternative?
The reasons to seek VPN alternatives depend on whether you’re an individual consumer or a business.
Consumers want VPN alternatives for two main reasons: money and system compatibility. Good VPNs are premium, which means more than $40 a year for the privilege. Meanwhile, not every device can support a VPN — consoles famously don’t.
Businesses may want VPN alternatives for security and scaling issues. A VPN on an employee’s laptop is also a security threat, either as something that can be stolen or because an employee may download a virus that would then spread over the VPN. Another reason may be speed: if you run a big office and your employees work remotely with the VPN on, you may experience some loss in speed.
In conclusion: using the right privacy tool
For a regular consumer, a VPN is all you need. But if you want to scale your business and keep it safe, hardware VPNs are an exponentially growing hassle. A SASE service is a great replacement for it. If your network is already secure and only needs a touch-up — try out ZTNA.
It all depends on your security administrator’s taste — do they like the flavor of detailed network management? Maybe their palette is not as refined yet, and you’re looking for a more straightforward solution.
Also, remember that many hardware VPN issues have been resolved by their successor — the software VPN. A VPN connection is a great option for both home AND business use. Easy to scale, simply implemented, and secured through the use of RAM-based servers, encryption, and obfuscation.
FAQ
What is safer than a VPN?
Tor is said to offer more privacy for individual use thanks to its service infrastructure. It helps you access the dark web and is often used for secure communication. Nonetheless, the service is sometimes disruptive and doesn’t use obfuscation — it doesn’t hide the fact that you’re using Tor.
For business owners — it’s not recommended to shift from VPNs to ToR simply because of unreliable service speeds and lack of network management.
Is Tor better than a VPN?
It depends on who is using it and why they need it. A brief Tor vs. VPN overview for you: Tor is great when you’re not concerned about speed and you need to relay something sensitive; a VPN is reliable when you need privacy on mundane internet browsing — it balances speed and convenience.
Is VPN safer than proxy?
Yes, because a VPN not only gives you a new IP but also encrypts and obfuscates your data traffic. A proxy will only reroute your traffic and change your IP, which makes it great for jumping over geo-blocks.
Does zero trust replace VPN?
As a security approach, zero trust can replace VPNs for company networks. However, it’s hard to implement and expensive for individual users.
What is the difference between a VPN and a zero-trust network?
Zero trust network assumes that all incoming connections are hostile and need to be verified before continuing. Meanwhile, a VPN assumes that a connection with the right credentials is friendly and lets it through.
Are VPN alternatives suitable for all types of businesses?
It depends on the alternative in question and the type of business. Small businesses can do well with VPNs. Large businesses are better off moving towards ZTNA or SASE approaches.