
Each of us carries a device that can record video, sound, and location. There are cameras everywhere. Every other intimate detail of our lives is scattered all about social media platforms.
Every time you remember that, there’s a whisper in the back of your mind. What are the odds the big suits above are not using that? Is the government watching me?
If that’s what you want to know, the simple answer is: yes, the government is watching you. The real question is, “to what degree?”
Real cases of government surveillance
For a long time, government surveillance was a ghost story for conspiracy theorists and hot-take specialists. But with the exposure of authorities around the world, it became a disturbing fact.
The 2013 NSA file leak
What happened? In 2013, people around the world were introduced to the US National Security Agency and what it does. Edward Snowden leaked NSA files that exposed the massive scope of the agency’s surveillance.
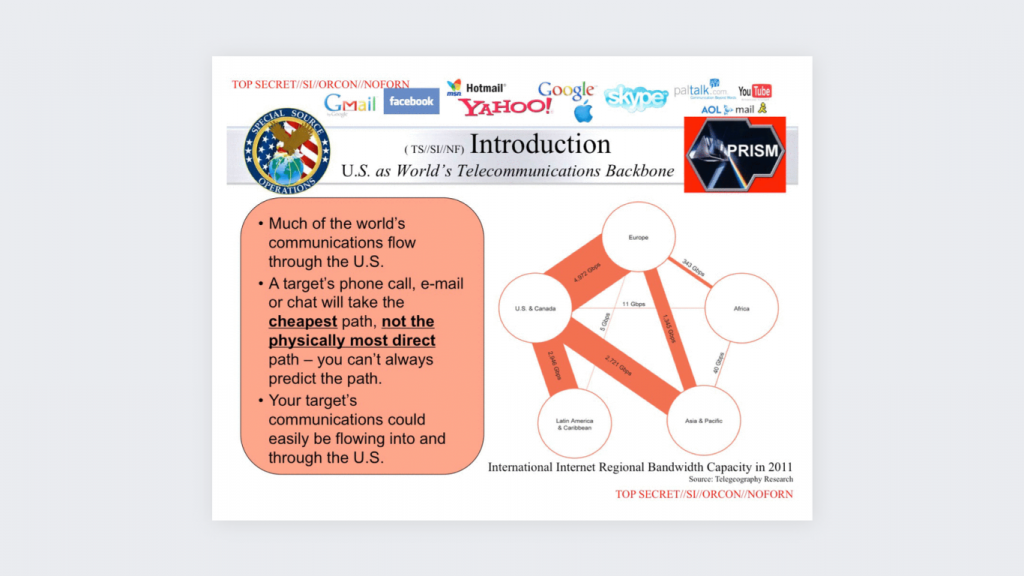
What does the NSA collect? Metadata about emails, time, location, and duration of phone calls, unique IDs; internet traffic data that travels in the US through fiber-optic cables (including other countries); metadata from Google, Apple, Facebook, Yahoo, and other internet giants.
What does this mean? It means that the US government is collecting metadata from its citizens and people in other countries. The NSA was said to collect 20 Terabytes of data every minute, equivalent to around 10 million photos taken on an iPhone 12 camera.

The NSA leak exposed the UK government too
The NSA files leaked by Snowden revealed the UK’s involvement in the same data-tracking network as the US government.
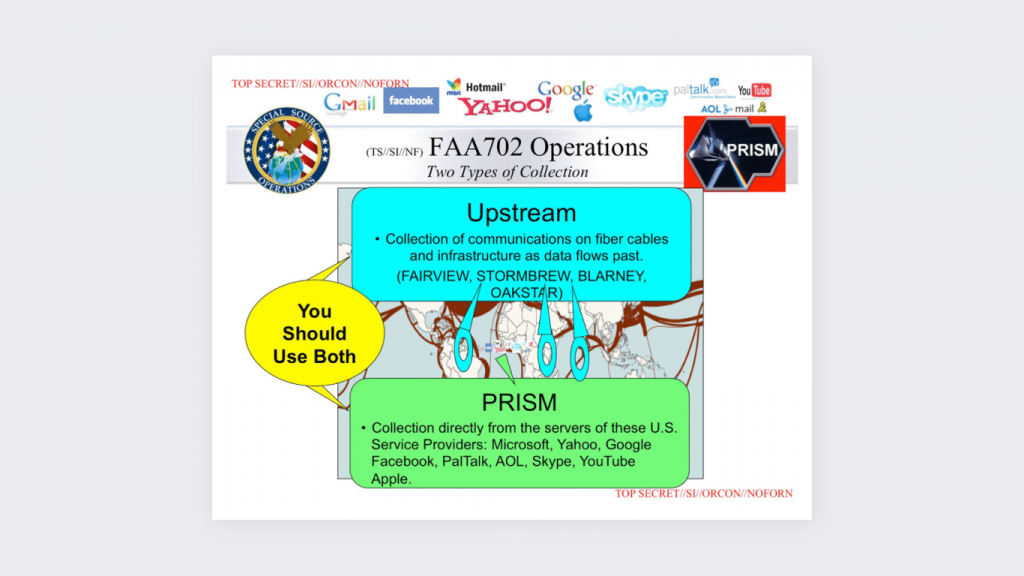
What happened? The UK Government Communications Headquarters (GCHQ) was running a mass surveillance system, Tempora, together with the US. Tempora is a program that intercepts and examines all data running through fiber-optic communication cables in the UK.
What does the GCHQ collect? Email messages, public and private social media posts, phone calls and IDs, browsing histories.
What does this mean? All data traveling through the fiber-optic cables in the UK and the US is being inspected by their governments.
Document Date: 2012-05-21
Description: This page from GCHQ's internal GCWiki, last edited in May 2012, provides background information on the agency's "internet buffer business capability": see the Der Spiegel article The NSA in Germany: Snowden's Documents Available for Download, 18 June 2014.
Document: [edit] News
BREAKING NEWS (May 2012) - The second tranche of 'deep dive' processing capability at RPC has gone live. In addition 2 extra IOG's are being processed at OPC. This brings the current deep dive' capability to:
- CPC with 16x10g,
- OPC with 7 x 1 0g
- RPC1 with 23 x l0g.
The MTI programme would like to say a big thanks to everyone who has made this possible (Which includes TCA. TEA. SSMG, SSOS, GTE, ACD. OPP-LEG, IT Services, R1 at E NSA. AHS and ) - a true collaborative effort!
The GCHQ called the Tempora program “Mastering the internet.” Sounds shady? All this information collection and processing is deemed legal by the countries because it is metadata.
This data was said to be processed by over 300 GCHQ and 250 NSA analysts. They examined keywords, emails, and web addresses and noted down what they needed.
It is important to note that metadata is data about data. It does not include the contents of emails, phone calls, or data packets. It includes their IDs, IP addresses, time, location, and other identifiers.
It’s the same information that many ad brokers and marketers use when trying to make you purchase something. However, it is still an invaluable resource for the government, especially for intelligence.
What can the government do with metadata?

Small amounts of metadata about you are not that scary. But when taken in bulk and over a long period of time, it can reveal:
- Places you frequent. Visiting the building two blocks away every Tuesday and Thursday – why? Oh, yoga class? Ok.
- Your hobbies and interests. Picking up fishing, I see. Awfully strange for someone who never learned how to swim.
- People close to you. I see you’re very close with X. Did you know they have a criminal record? Doesn’t bother you? Interesting.
- Whom and how often you call. We see you’ve called your psychiatrist three times last week and once after midnight. Where were you on July 15th?
- Your method of communication. You always use WhatsApp but send a couple of messages a month through Signal. Care to explain yourself? No? Smart.
The list can stretch as far as your imagination. The thing is, bulks of metadata accumulate and reveal patterns in our actions. In turn, these patterns can be used to make allegations, something we’ve already seen happen recently with AI (artificial intelligence) technology.
How government surveillance looks in action
Aside from mass surveillance of data influx, there are different ways the government collects metadata. Most of these were made possible by recent technologies like AI, machine learning, and social media. Others rely on using the law to their advantage.

The government uses AI to track social media profiles
The governments don’t just intercept data that travels through their countries. Recent cases show that they scrape people’s social media profiles for information. This data is aggregated, organized, and analyzed by artificial intelligence (AI) for mass surveillance.
What does this mean? Well, using just your social media profiles, this AI can:
- Map your relationships.
- Assign the meaning and attitude to your social media posts.
- Infer your past, present, and future locations.
- Inform facial recognition technology.
- Gather information about your political views, religious beliefs, and sexual orientation.
The last point is particularly dangerous because there are still places in the world where that information can be used to harm someone.
Luckily, the technology is not at that stage yet. But at the same time, we’re starting to see different applications of AI in government surveillance.
Government social media tracking turns to facial recognition

The AI can collect and analyze millions of pictures and turn this information into facial recognition. It’s a technology that allows an AI program to recognize people’s faces. Several authorities around the world are already using it:
- The Department of Homeland Security (DHS) extended its surveillance area 100 miles outside of the US border. It now monitors an additional 200 million people that are not its citizens.
- Customs and Border Protection (CBP) has purchased the technology to bypass certain encryption and passwords in people’s phones and computers to extract data. Around 300 police departments use similar tools in California alone.
How was facial recognition used in a social context? In 2021 the US police used facial recognition to “support criminal investigations related to civil unrest, riots, or protests.” However, the technology proved to be very ineffective at separating people of different races.
Recently, Australia’s said to start using the same technology to enforce the COVID-19 pandemic rules. However, the EU is not as enthusiastic about it as other countries. The EU parliament recently backed a ban against police using facial recognition.
Tech giants vs. the government
We worry about tech giants like Facebook and Google watching us. But we also tend to forget that they’re companies based inside countries and have to abide by the local law.
If you ever thought your Facebook data was limited to the platform, I’m sorry to disappoint you. We already know that the government collects metadata. But companies like Google, Facebook, Apple, and Microsoft also share a lot of information with the government (read our User Data Surveillance Report).
From 2013 to 2019, data requests made by the government from big tech companies have grown by 213%. This increase might be due to the changes that happened after the NSA file leak in 2013.
Whatever the case may be, government surveillance is on the rise. The good news is that the companies don’t always comply with these requests. However, the requests they comply with range from 55% to 76% (lowest being Apple, highest – Facebook).
However, such requests are for specific cases. It’s usually about what metadata cannot show about a person (I.e., actual conversations within emails or texts).
The government is watching you, but it might not be like you think
But wait, if the government records and processes so much data, why would they need help from big tech companies?
Well, the government is not all-powerful. The NSA, GCHQ, and other authorities have limited resources. They simply can’t collect all the information about every person. And that’s why they process metadata to inform themselves first before investigating deeper.
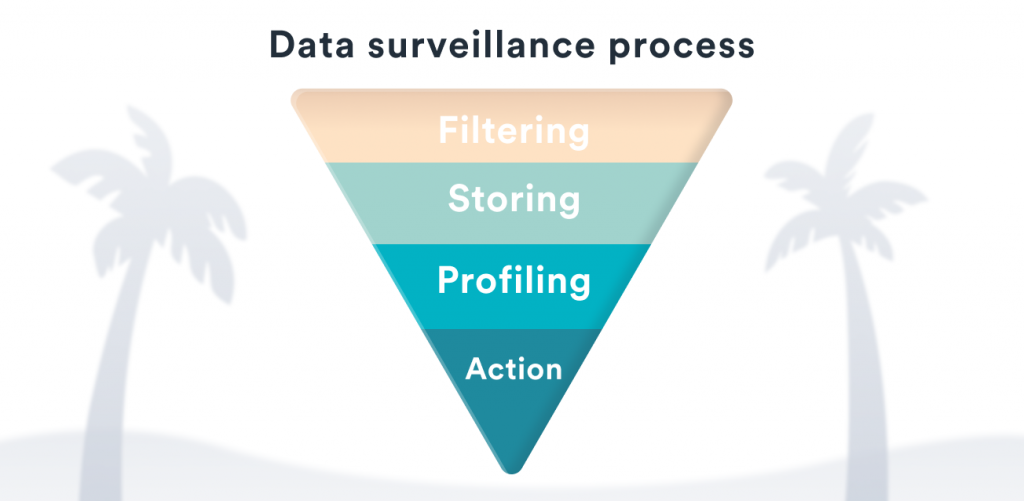
To give it a rough outline, here’s how the data surveillance would look like:
- The government filters large amounts of metadata. The data goes through their filters that look for specific keywords, email addresses, names, tags, numbers, etc.
- Relevant data is automatically picked out and stored in profiles.
- Government agents sieve through this information. They examine and evaluate the potential threat of information.
- They narrow down their targets. If potential threat levels are high, they will inform other authorities.
As you can see, it’s really all about threat detection and prevention (however you want to define the word ‘threat’ here). It’s important to remember that no government, company, or organization has infinite resources to watch everyone closely.
That might change with AI soon, but to what degree – we do not know. What we do know right now is that the technology is still in its infancy.
Tips to avoid the government watching you

If you don’t fancy the government watching you, here are some tips to protect your privacy:
- Be careful what you post on social media. The AI scraping and processing large amounts of social media profiles would be impossible if people didn’t post. Facebook alone has nearly 3 billion monthly active users, meaning the government has access to information about nearly half of the world’s population. So, if you don’t want to be a part of that experiment, don’t post sensitive information about yourself!
- Use a VPN. A VPN will hide your internet traffic, so the government won’t be able to tell what data is yours. But bear in mind that a VPN won’t help if you’re using an email or credit card with your name or otherwise personally identifiable information.
- Don’t transmit data online that might harm you. If you’re a whistleblower or live in a country with strict censorship, be careful what information you share online. If the data can be tied to your name, you might get in trouble!
- Get a password manager. This tip is good for general digital hygiene as well as protecting yourself from any prying eyes. Technology allows authorities to crack weak passwords with ease (CBP example above). So, invest in a password manager!
- Avoid free and shady apps. Installing an app can give someone remote access to your phone. Be wary of what software you use!
Can the government watching you prove useful?
Credit is given where credit is due – not all surveillance is pure evil. We need to maintain a level of tracking to keep people accountable (like cameras at malls, for example).
The question is, does mass metadata collection justify itself? According to the NSA, this information has helped them to:
- Prevent terror (and other) threats before they happen.
- Track and prevent COVID-19 from spreading.
The reasons sound legit and serious. But both the morality and effectiveness of mass surveillance have been questioned multiple times.
Knowledge informs action. It’s up to us to ensure we take the correct steps to handle our data with care. And many people claim that such mass surveillance, as showcased by the NSA and GCHQ, has crossed the line.
Whatever the case may be, it’s everyone’s individual choice and responsibility for how they handle their data. Use the tips above to protect your privacy because the government won’t do that for you.
And if you’re looking for a VPN, consider giving Surfshark a go. We don’t monitor your connection or keep any logs. What you do on the internet is your business and yours alone.
