The largest ransomware attacks have shut down hospitals, triggered fuel shortages, cost businesses billions, and forced governments into declaring national emergencies.
Below, we’ll examine 15 major ransomware incidents. We’ll focus on their short- and long-term impact, the lessons we can learn from them, and the measures we can take to strengthen our defenses as individuals.
What is a ransomware attack (and how does it spread)?
Ransomware is a type of malicious software that locks users out of their files or systems. Attackers then demand payment — usually cryptocurrency — in exchange for restoring access.
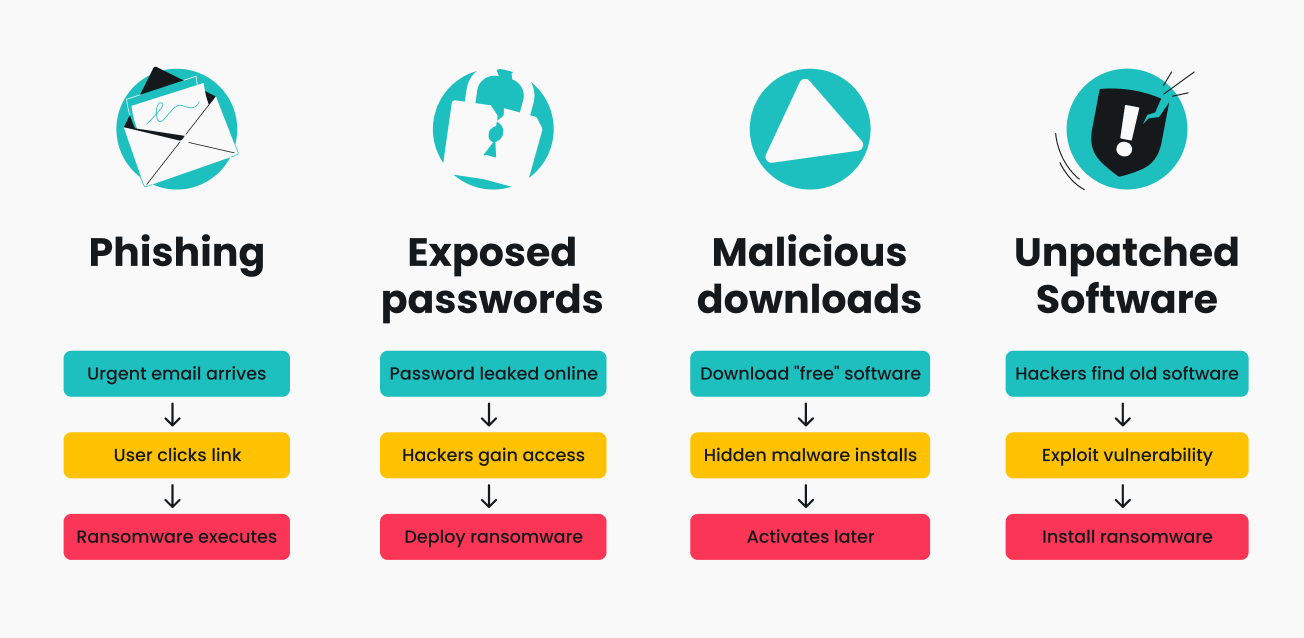
How do attackers get in? Typically through one of these:
- Phishing emails: fake urgent emails with malicious links or attachments;
- Exposed passwords: credentials leaked to the dark web;
- Malicious downloads: fake apps, cracked software, or infected links;
- Unpatched software vulnerabilities: outdated programs hackers exploit.
And ransomware isn’t standing still. In 2025, attackers use AI tools to write convincing phishing messages and tweak attack code on the fly.¹ That means staying careful online has never been more important.
If you’d like a deeper dive, Surfshark’s ransomware research breaks down how these attacks tend to spread.
15 of the biggest ransomware attacks in history
Some ransomware incidents stand out because of the disruption they caused, the number of people they affected, or the lessons they forced us to learn.
Below are the 15 biggest ransomware attacks that shaped today’s digital security landscape.
1. CryptoLocker outbreak (2013-2014): the first major ransomware wave
- Demanded amount: around $300-$600 in bitcoin per victim
CryptoLocker was one of the first ransomware outbreaks to hit the headlines. It spread mainly through malicious email attachments, infecting hundreds of thousands of computers across the globe. Attackers encrypted the files and demanded payment in bitcoin — a relatively new concept at the time.
CryptoLocker pioneered ransomware’s business model: encrypt files, demand crypto, and set deadlines. Security experts eventually managed to neutralize the malware, but by then, it had already collected millions from ransomware victims and inspired countless copycats.
2. NotPetya operation (2017): a cyberwarfare trial run
- Demanded amount: about $300 in bitcoin per computer
NotPetya first looked like typical ransomware, but it turned out to be especially destructive. It spread rapidly through a software update in Ukraine, crippling banks, airports, shipping companies, and government agencies. Unlike most ransomware, NotPetya didn’t even have a functioning payment system — suggesting it was built more to destroy than to earn money.
The global damage was estimated at over $10 billion, making it one of the worst ransomware attacks ever. It also showed the world how ransomware could be used as a weapon of cyberwarfare, instead of just a way to make quick money.
3. WannaCry attacks (2017): a worldwide ransomware outbreak
- Demanded amount: about $300–$600 in bitcoin per device
WannaCry became a household name overnight. In May 2017, this ransomware spread like wildfire by exploiting a Windows vulnerability called EternalBlue. Within days, more than 200,000 computers across 150 countries were locked, making it one of the biggest malware attacks in history.
Hospitals in the UK had to cancel appointments, factories shut down, and organizations from FedEx to Telefónica were disrupted. The speed and scale of WannaCry showed just how quickly ransomware could paralyze critical services.
At the time of the attack, Microsoft had already released a patch for the vulnerability — but many systems hadn’t been updated, proving that skipping security updates can come with a very real cost.
4. Ryuk campaign (2018-2020): targeting big organizations
- Demanded amount: from $100,000 to over $1 million per organization
Ryuk marked a shift in ransomware strategy. Instead of casting wide nets, attackers using Ryuk targeted large organizations — especially hospitals, newspapers, and local governments — where downtime could be devastating. By targeting big fish, they could demand massive ransoms — and often got paid.
Ryuk also introduced the now-common double extortion tactic: not only encrypting files, but also stealing data and threatening to leak it unless payment was made. This approach raised the stakes for the ransomware victims, forcing many to pay up just to keep sensitive data from getting exposed.
During its peak years, Ryuk caused hundreds of millions of dollars in losses and paved the way for today’s professional ransomware gangs.
5. GandCrab outbreak (2018-2019): popularizing RaaS
- Demanded amount: between $600 and $700,000, depending on the victim
GandCrab quickly became one of the most widespread ransomware strains of its time. Instead of being run by a single group, it was offered as RaaS (Ransomware-as-a-Service) — meaning anyone could rent the malware and launch an attack, with developers taking a cut of the profits.
This model attracted thousands of cybercriminals and led to an explosion of ransomware incidents worldwide. Estimates suggest GandCrab earned its operators over $2 billion before they announced their retirement in 2019.
Even though GandCrab was shut down, its business model lived on. Many modern ransomware groups, like REvil and LockBit, still use the same playbook today.
6. Travelex (2019): crippling financial services
- Demanded amount: about $6 million in bitcoin
In late 2019, foreign exchange company Travelex was hit by a ransomware group called REvil. The attack took down Travelex’s websites, mobile apps, and even its ability to process currency transactions at airports around the world. That meant that customers couldn’t buy or sell currency for weeks.
REvil (also known as Sodinokibi) was one of the most notorious ransomware gangs, and the attack on Travelex showed just how disruptive targeting a single global service provider could be. Travelex was forced into weeks of downtime and ended up entering administration (a UK form of bankruptcy protection), showing how ransomware incidents can push even major companies to the brink.
The Travelex case exposed the vulnerability of modern financial services and cemented REvil’s reputation in the underworld.
7. Kaseya (2021): supply chain ransomware at scale
- Demanded amount: up to $70 million in bitcoin for a universal decryption key
In July 2021, the REvil group struck again — this time through Kaseya, an IT management software provider. By exploiting a software vulnerability, the attackers pushed ransomware to hundreds of MSPs (Managed Service Providers), which in turn infected thousands of small and medium-sized businesses worldwide.
Its place among the largest ransomware attacks is well deserved: the consequences were staggering. Grocery store chains in Sweden had to shut down, dental clinics in the US were locked out of patient files, and countless small businesses were left scrambling.
The Kaseya incident showed how powerful supply chain attacks can be: compromising one provider is enough to spread ransomware to hundreds of victims at once. It remains one of the largest ransom demands ever made.
8. Colonial Pipeline (2021): hitting critical infrastructure
- Demanded amount: about $4.4 million in bitcoin (most of which was later recovered by US authorities)
In May 2021, Colonial Pipeline — the company supplying nearly half of the US East Coast’s fuel — was forced to shut down operations after a ransomware attack by the DarkSide group. The shutdown triggered panic buying and fuel shortages across several states, with gas stations running dry in some areas.
The company quickly paid the ransom to restore operations, but the attack exposed critical infrastructure vulnerabilities. It also caught the attention of the US government, which treated the event as a national security issue and later recovered a significant portion of the ransom.
Colonial Pipeline was among the most high-profile ransomware attacks to date, and a wake-up call for governments worldwide.
9. JBS Foods (2021): disrupting the food supply chain
- Demanded amount: about $11 million in bitcoin
Just weeks after the Colonial Pipeline attack, REvil targeted the world’s largest meat supplier, JBS Foods. The ransomware campaign forced the company to shut down meat processing plants in the US, Canada, and Australia, disrupting global food supply chains.
To quickly restore operations and prevent further disruption, JBS decided to pay the ransom — one of the largest publicly known ransom payments at the time. The incident underscored how ransomware can directly affect something as basic and essential as food supply.
Together with Colonial Pipeline, this attack proved that ransomware wasn’t just an IT problem — it was a real-world issue with immediate consequences for millions of people.
10. Kronos (2021): freezing payroll systems
- Demanded amount: not publicly disclosed
In December 2021, the workforce management company Ultimate Kronos Group was hit by a ransomware attack that disrupted its Kronos Private Cloud services. This platform was used by thousands of businesses to manage payroll, scheduling, and HR tasks.
The impact rippled across industries — from hospitals to retailers — leaving many employees unable to access timesheets or receive paychecks on time. Some companies had to switch back to manual recordkeeping for weeks.
The Kronos incident was a clear reminder that corporate ransomware attacks can directly affect the livelihood of everyday workers.
11. Costa Rican government (2022): forcing a national emergency
- Demanded amount: about $20 million
In April 2022, the Conti ransomware group launched a massive attack on Costa Rica’s government systems. The Ministry of Finance was hit hardest, disrupting tax collection and customs processing. Soon after, other government agencies — including those handling social security and health — were also affected.
The attack was so severe that the Costa Rican president declared a state of emergency, a first in the country’s history for a cyber incident. For weeks, imports and exports slowed to a crawl, businesses struggled with paperwork, and government services were paralyzed.
This event showed how the worst ransomware attacks could destabilize not just companies, but entire national economies — especially when critical government functions are involved.
12. MOVEit (2023): mass data theft
- Demanded amount: varied by victim; some reports suggest millions per organization
In mid-2023, the Clop ransomware group exploited a vulnerability in MOVEit Transfer, a popular file-sharing software. This high-profile ransomware attack had a massive global reach — MOVEit was used by hundreds of corporations, universities, and government agencies to transfer sensitive data.
Instead of encrypting files, Clop stole data and used a data leak extortion method: threatening to publish stolen information unless victims paid up. Organizations hit included US federal agencies, the BBC, Shell, and British Airways.
The MOVEit incident demonstrated how a single software flaw in a widely used product could lead to a cascade of global breaches. It also highlighted a growing ransomware trend — attackers don’t always need to lock files; stealing and leaking data can be just as damaging.
13. Caesars and MGM Resorts (2023): ransomware on the Vegas Strip
- Demanded amount: Caesars reportedly paid about $15 million; MGM refused and lost tens of millions in revenue
In September 2023, two of Las Vegas’s biggest names — Caesars Entertainment and MGM Resorts — were hit by corporate ransomware attacks orchestrated by groups linked to ALPHV/BlackCat.
Attackers reportedly gained access through a simple social engineering trick: calling the IT help desk and impersonating an employee. Once inside, they disrupted hotel check-in systems, slot machines, and digital room keys. MGM’s operations across the Strip were thrown into chaos, with guests locked out of rooms and long lines forming in lobbies.
Caesars quietly negotiated and paid part of the ransom, while MGM chose not to — resulting in weeks of disruption and estimated losses of over $100 million.
14. CDK Global (2023–2024): stalling car dealerships
- Demanded amount: reports suggest tens of millions, though exact figures weren’t disclosed
In June 2024, CDK Global, a major software provider for car dealerships across North America, was crippled by a ransomware attack. CDK’s platform manages everything from sales to financing to service scheduling, so when its systems went offline, thousands of dealerships were forced back to pen and paper.
The outage lasted for weeks, leaving dealers unable to process transactions, track inventory, or access customer records. Some dealerships reported losses of hundreds of thousands of dollars per day, and customers faced delays in buying or repairing vehicles.
The CDK incident is now considered one of the biggest ransomware attacks in history, showing how targeting a single service provider can disrupt entire industries.
15. Change Healthcare (2024): shutting down healthcare payments
- Demanded amount: about $22 million in bitcoin, which was reportedly paid
In early 2024, Change Healthcare, a subsidiary of UnitedHealth Group, was hit by a ransomware attack that shook the US healthcare system. The attack, carried out by the ALPHV/BlackCat group, crippled payment and claims processing for hospitals, pharmacies, and clinics nationwide.
For weeks, healthcare providers couldn’t get reimbursed, prescriptions were delayed, and patients faced difficulties accessing care. UnitedHealth later admitted to paying a ransom of roughly $22 million, though recovery was slow and costly.
This incident highlighted the extreme risks corporate ransomware attacks pose to critical services, where downtime doesn’t just cost money — it can directly impact people’s wellbeing.
What these ransomware attacks taught us
Looking back at these cases, a few patterns emerge, showing how cyberattacks evolved and what organizations and individuals can learn to stay safer.
- Supply chain attacks magnify impact: Kaseya and CDK Global prove that targeting one software provider cascades to thousands of businesses downstream. Everyone connected faces risk, not just direct targets.
- Critical infrastructure remains vulnerable: pipelines, hospitals, food supply chains — ransomware directly affects lives through fuel shortages and delayed medical care.
- Paying doesn’t guarantee safety: even after paying, victims aren’t secure. Research shows 73% of victims have been hit more than once.²
- The tide is turning: only 17% of UK enterprises paid ransoms in 2025 (down from previous years)³, and global payments dropped 35% to $813 million in 2024⁴ — thanks to stronger backups, better response plans, and government pressure.
- AI changes the game: generative AI makes phishing emails more convincing and helps attackers tweak malware in real time⁵ — scams are harder to spot, defenses must keep up.
- Old vulnerabilities still work: despite new tools, attackers exploit basics like unpatched software. WannaCry spread through missing updates, and even in 2024, groups like Akira exploited older VPN vulnerabilities.⁶
How to protect yourself from ransomware attacks
While the ransomware victims discussed in the cases above are corporations, ransomware doesn’t discriminate — personal computers are vulnerable too. Most ransomware incidents exploit basic mistakes like weak passwords or outdated software, whether you’re protecting family photos or company data.
Essential cybersecurity tips for everyone
- Keep your software up to date: many outbreaks spread through old vulnerabilities. Enable automatic updates everywhere.
- Use strong, unique passwords: reusing passwords makes you an easy target. A password manager helps manage them.
- Add MFA (Multi-factor Authentication): text codes or authenticator apps add barriers, even if passwords leak.
- Back up your data regularly: store backups offline or in secure cloud services. Test restoration periodically.
- Be cautious with emails and links: don’t click suspicious attachments, even from known contacts.
- Use antivirus software and a VPN: Surfshark’s Antivirus features block malware; a VPN (Virtual Private Network) increases your security on unprotected networks.
Workplace considerations
- Report suspicious emails immediately: IT teams can warn others and investigate.
- Never bypass security policies: those restrictions exist for good reasons.
- Keep work and personal accounts separate: a personal breach shouldn’t compromise company data.
- Know your company’s backup system: understand what’s protected and what isn’t.
- Use the corporate VPN: if your company uses one, make sure you connect when working remotely or on public networks.
Remember: Colonial Pipeline’s shutdown started with one compromised password. MGM’s chaos began with one phone call to IT. Most malware attacks on companies begin with a single person — meaning your personal actions matter more than you might think.
Conclusion: Ransomware is evolving, but smart habits still work
Ransomware has evolved from small-time scams into global disruptions halting pipelines, hospitals, and governments. The attacks we’ve examined reshaped how the world thinks about cybersecurity — and while threats grow more sophisticated, basic digital hygiene still makes a difference.
Stay cautious, keep your software up to date, and remember: prevention is always cheaper than recovery.
FAQ
What is the 3-2-1 rule of ransomware defense?
The 3-2-1 rule means keeping three data copies on two different media types with one copy stored off-site. This ensures you can recover files even if ransomware locks your main system and local backups.
What is the greatest cyberattack in history?
That depends on how you measure greatest — whether by scale, damage, or political impact. Many experts point to Stuxnet (which physically damaged Iran’s nuclear centrifuges) as a landmark because it blurred physical-cyber boundaries.
What was the largest ransomware attack in 2025?
As of mid-2025, there isn’t a single undisputed largest ransom demand, but multiple attacks are making headlines for their size and damage. Some reports suggest ransom demands reached tens of millions of dollars in several cases.
What is a Medusa ransomware email?
Medusa ransomware emails are phishing messages that trick victims into opening malicious links or attachments, giving attackers access to install ransomware. Medusa is a RaaS variant that steals data and threatens leaks if ransoms aren’t paid.
What companies have been hacked by ransomware?
Hundreds — from small businesses to global corporations. Well-known victims include Colonial Pipeline, JBS Foods, MGM Resorts, Caesars Entertainment, Change Healthcare (UnitedHealth), and service providers like Kaseya and CDK Global.
Sources used
https://www.sattrix.com/blog/biggest-ransomware-attacks-in-us/
https://www.digitalguardian.com/blog/50-examples-ransomware-attacks-and-their-impacts
https://cybermagazine.com/articles/top-10-ransomware-attacks
¹ https://www.forbes.com/sites/zakdoffman/2024/12/21/fbi-warns-gmail-outlook-apple-mail-users-check-3-things-now/
² http://semperis.com/wp-content/uploads/resources-pdfs/reports/resources-semperis-ransomware-risk-report.pdf
³ http://itpro.com/business/business-strategy/ransomware-victims-are-refusing-to-play-ball-with-hackers-just-17-percent-of-enterprises-have-paid-up-so-far-in-2025-marking-an-all-time-low
⁴ https://www.bleepingcomputer.com/news/security/ransomware-payments-fell-by-35-percent-in-2024-totalling-813-550-000/
⁵ http://mitsloan.mit.edu/ideas-made-to-matter/80-ransomware-attacks-now-use-artificial-intelligence
⁶ https://thehackernews.com/2025/09/sonicwall-ssl-vpn-flaw-and.html

