Secure your personal data and stay private online with Surfshark’s industry-leading VPN encryption.
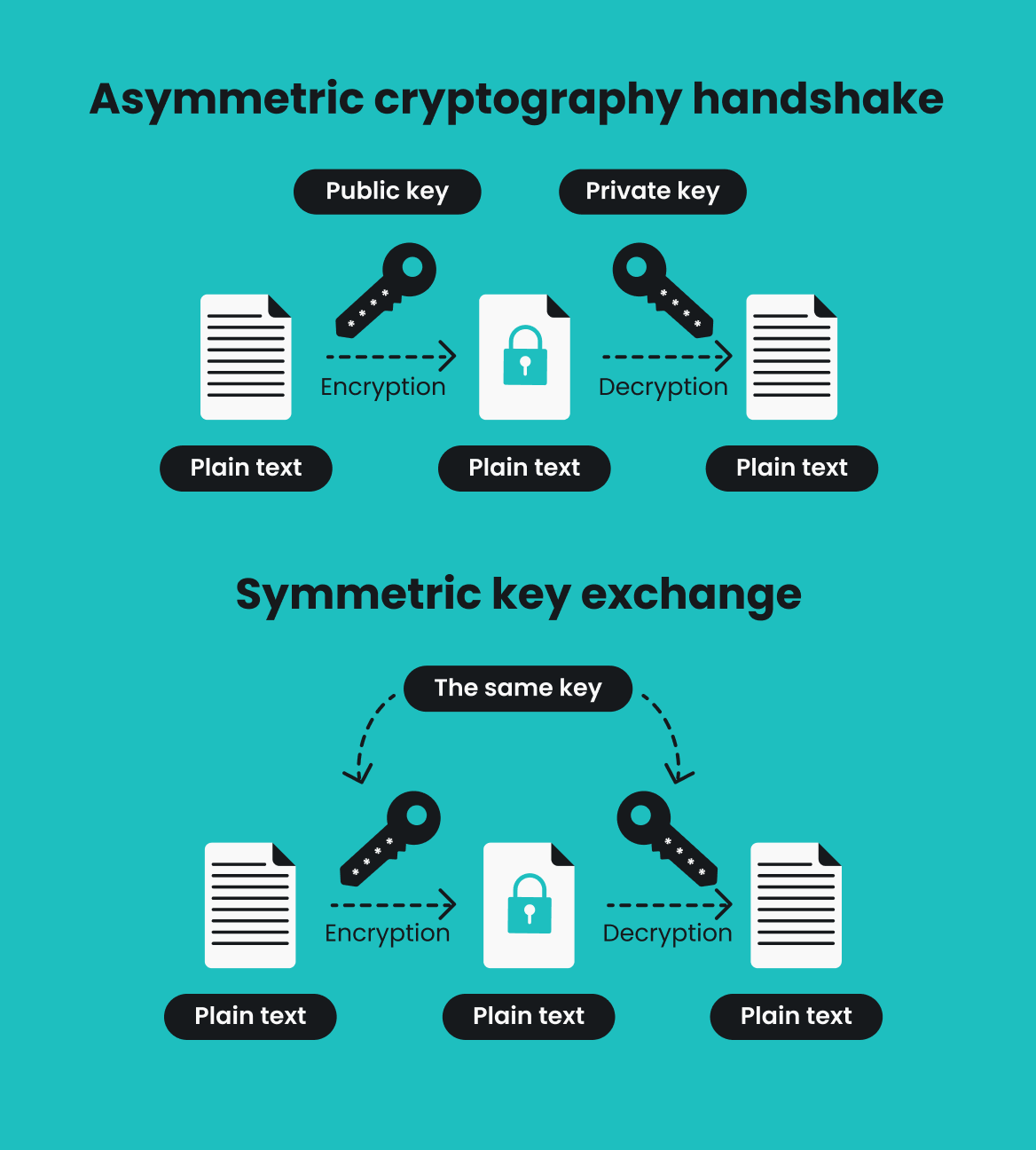
What is VPN encryption?
VPN (Virtual Private Network) encryption is a process that enciphers data transmitted between your device and a VPN server to secure it.
When you connect to a VPN, an encryption key is generated, which is used to encode and decode the data. No one besides you has that key, so even if a third party tried to intercept your connection, your encrypted data would look like useless nonsense to them.
Strong encryption is crucial to any VPN. That’s why trustworthy VPN service providers, including Surfshark, use AES-256 encryption — one of the most effective encryption algorithms to date. Along with AES-256 encryption for OpenVPN and IKEv2 protocols, Surfshark uses equally effective ChaCha20 encryption for the WireGuard protocol.