The Tor (The Onion Router) Browser is an internet browser part of the Tor Project. It sends your traffic through a volunteer-based network to provide privacy and anonymity online. However, there are some things you should know about before blindly trusting Tor with your privacy. Keep on reading to learn how the Tor Browser works.
Table of contents
Is the Tor Browser safe?
The Tor Browser offers a solid boost to your online privacy by hiding your IP (Internet Protocol) address and making it more difficult to trace your online activity back to you. Therefore, it is safer than a regular browser, but it does have known vulnerabilities. So, if you browse onion websites or want to be a whistle-blower online, you might want to secure yourself by running Onion over VPN.
Benefits | Issues |
|---|---|
Three layers of encryption | Entry node sees your IP, exit node sees your data |
Connects via three random nodes | Nodes are run by volunteers and could be compromised |
Nodes are changed every five minutes | Only browser traffic is encrypted, while all other traffic remains unaffected |
Verdict
The Tor Browser is safe, but it’s not bulletproof. Your IP address is vulnerable at the entry node, and your data is vulnerable at the exit node. Cracking both nodes and matching your IP to your data might be rare, but it’s not impossible. If privacy is your main concern, you should use a reputable VPN together with Tor at all times.
How Tor works
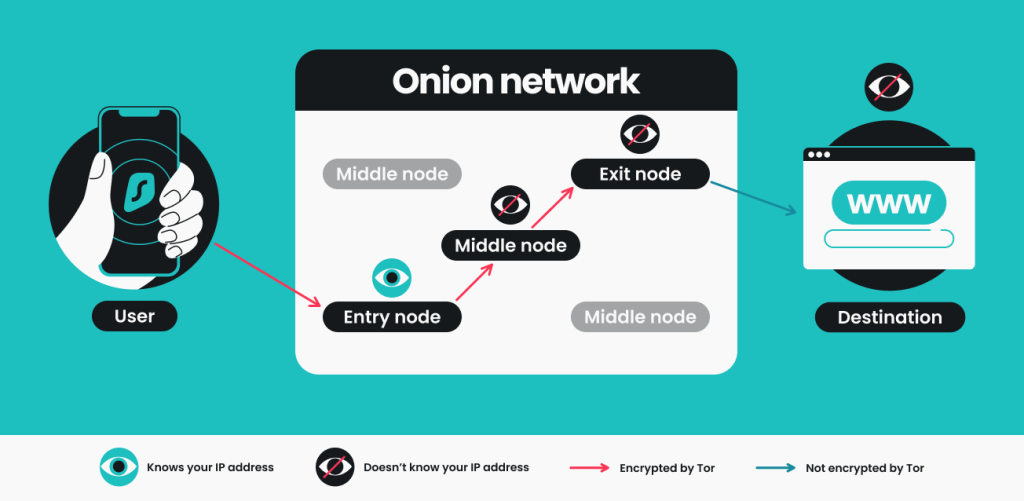
The Tor Browser relies on a network of volunteers to encrypt your traffic and send it through three different servers, also known as nodes or relays. This process hides your IP address and protects your activity data from snoopers and any other intrusive third parties.
When you access Tor, the entry relay can see your IP but not the data you send. The middle relay can see your data but not your IP. The same applies to the exit relay, which sends your data to the internet but doesn’t know where it’s coming from. These relays are changed every 5 minutes as a preventative measure against compromised nodes.
In theory, such a connection could be considered secure since no single relay has access to both your IP and data. However, the security issues linked with Tor prove that the system isn’t flawless.
What are the benefits of using Tor?
Using the Tor Browser comes with a few risks, but there are still plenty of good reasons to give it a go and bulk up your online security:
It improves privacy
Tor is specifically designed to improve your online privacy and anonymity. It encrypts your data, hides your traffic from third parties, and keeps your IP address secret, making it difficult for anyone to trace your online behavior back to you.
But if privacy is your main concern, consider using Tor together with a VPN. A VPN hides your real IP from the owner of the entry relay and eliminates the flaws in Tor’s encryption.
It’s harder to compromise
Tor’s network routes your internet traffic through multiple volunteer-operated servers and creates several layers of encryption. In theory, this system is harder to compromise.
In practice, volunteer networks can be infiltrated by bad actors. So Tor might be safer than a free VPN, but using a reputable paid VPN like Surfshark is even more secure.
It’s easy to use
Over the years, Tor has become increasingly user-friendly. It’s easy to use, and Tor users don’t need to be tech-savvy to browse the internet privately. Simply download the browser, launch it, and start browsing. It will automatically connect you through a secure node and, in most cases, allow you to connect to the Tor network without further configuration.
It’s free
Tor is a free and open-source software run by a community of volunteers worldwide. While they do accept donations, you don’t have to pay for a premium version or subscription. However, we all know the saying, “If you’re not paying for the product, you are the product,” so it begs the question — is Tor really safe?
The security vulnerabilities and risks of the Tor Browser
Most security issues linked to Tor are caused by the fact that its network is run by volunteers. This means that nearly anyone can set up a server and become a part of the network. As a result, your traffic may run through relays owned by malicious actors or even government agencies, such as the CIA.
Volunteer-run networks can be easily compromised
With enough nodes, you can intercept the data going through the entry and exit nodes of the same circuit. This means that a person or group of people could hold both the entry and the exit relay of your connection at the same time. The more relays someone owns, the more likely it is to happen.
Sure, the servers are changed every few minutes, but even a few seconds could be costly if you’re dealing with sensitive information online.
Malicious parties may collect data
When a hacker-owned server acts as an entry node, hackers can record your IP and find out who you are. When a hacker-owned server acts as an exit node, hackers know what websites and services you accessed via that node.
If they manage to collect enough data, malicious actors can piece together what you were doing online at one point or another.
Malicious parties can monitor data at the exit node
Exit node eavesdropping refers to hosting nodes intending to harvest data as it becomes deciphered by the exit node. This may have been the case in 2021 when an unknown entity had compromised 900 Tor network nodes.
Suppose your traffic isn’t encrypted by TLS (Transport Layer Security) or a VPN (Virtual Private Network). In that case, the person monitoring the exit node can capture sensitive data such as combinations of account names and passwords.
Tor exit nodes may be blocked
Some websites and services block Tor IP addresses from accessing their content. This may happen if a Tor user breaks a service agreement, Terms of Use, or other company rules. In addition, some websites may block Tor IPs if they notice an abundance of malicious activity coming from such addresses.
In addition, using Tor may be illegal in some countries due to dark web connections or because it provides online privacy, which some authoritarian governments don’t like. Since your internet service provider can tell you’re using Tor, this can expose you to the authorities.
So, if someone knows that you’re using Tor, it’s possible they can track you while you’re using it.
Online tracking is possible on the Tor network
It is technically possible to track you on Tor. As discussed earlier, Tor’s connection-routing nodes have vulnerabilities. Here are two of the most common ways for third parties to track you on Tor:
- Triangulation: it is possible by matching data from entry and exit nodes. To do so, a hacker needs to have access to both nodes. This would allow them to assume that traffic sent at a certain point in time is related to a post or comment that appears at the exit node one or two seconds later.
For example, a connection made at 9:51:15 a.m. may be linked to a post made at 9:51:16 a.m. - Eavesdropping: at the exit node, eavesdropping may allow bad actors to steal user data. Tor traffic isn’t encrypted when it leaves the exit node. If someone manages to intercept the connection before it reaches the internet, they may be able to access sensitive data that can be linked to you.
Malware infections can target your devices
While Tor helps with your online privacy and anonymity, it doesn’t make you immune from malicious websites. The dark web, in particular, is full of malware. Make sure to use a reliable antivirus to protect yourself from such threats — or get a Surfshark One subscription, which combines Antivirus with VPN protection.
Security levels vary on different devices
Due to platform constraints, the Tor Browser has different levels of security. It’s officially accessible on Android, Windows, Linux, and macOS. However, it is unavailable for iOS devices because Apple requires that either the UIWebView or WKWebView rendering engine be used to create any iOS browser.
This requirement prevents Apple from developing a dedicated Tor Browser for Apple users. The closest alternative for iOS users is Onion Browser. This browser was developed by Mike Tigas, one of the volunteer core contributors at Tor.
The Onion Browser doesn’t offer the same level of security as the official Tor Browser. So, if you need to use Tor to protect your privacy and anonymity, do so on a computer or an Android device.
Is the Tor Browser legal?
Tor is legal in most countries worldwide. However, countries like Belarus, Turkey, Russia, Iran, and Saudi Arabia have specific regulations for Tor, while China blocks all Tor traffic. If you live in any of these countries, we advise you to research your legislation before using the browser.
Using Tor can become dangerous in countries where it’s illegal. Your ISP (Internet Service Provider) doesn’t see what you do on Tor, but it can detect your internet traffic going through the Tor network. This means they can track when you use the browser and report Tor usage to the authorities.
It is important to note that engaging in illegal activities while using Tor is against the law in all countries.
How to use the Tor Browser safely
We have written a dedicated article on how to use Tor safely, but here’s a shorter version for you:
- Set the Tor Browser security settings: go to Settings > Privacy & Security > Choose between three levels of security available to you: Standard, Safer, and Safest. Safer settings limit access to some features and may slow down the already slow Tor connection even more;
- Disable JavaScript: JavaScript may collect Personally Identifiable Information (PII) and has been prone to vulnerabilities in the past. Avoid such risks by simply disabling JavaScript altogether;
- Don’t use personal accounts: don’t provide personal email addresses or other information on Tor, especially on .onion sites. Use burner accounts or Surfshark’s Alternative ID feature to generate an alternative identity for Tor use;
- Use New Identity: New Identity is a Tor Browser feature that clears your cookies and cache, closes all windows, and starts a brand new connection with new relays. Use it periodically to delete traces of your previous activity on the browser;
- Update your apps: updates often fix certain security issues or tackle zero-day vulnerabilities. To ensure optimal security, always keep your Tor Browser, VPN, and antivirus apps updated.
- Use Tor over a VPN — a VPN encrypts your traffic before it reaches Tor, which protects you from Tor’s vulnerabilities at the entry and exit nodes. Overall, Tor over a VPN provides the safest possible Tor experience, but it may slow down your connection significantly.

What is the difference between Tor, VPN, and Proxy?
Tor: a network that bounces your internet traffic through multiple volunteer-operated servers. It is typically used to access .onion websites or improve privacy when browsing anywhere else.
VPN: a virtual private network. It creates a secure, encrypted tunnel between your device and a remote server while hiding your IP address.
Proxy: a server that acts as an intermediary between your device and the internet, forwarding your web requests. It can change your IP but doesn’t encrypt data on its own.
Here’s an analogy: think of your online journey as a package you’re sending through the mail.
- Tor is like sending a package through a series of secret tunnels and mazes. It hides your package in a sealed box, concealing it from everyone;
- A VPN is like sealing your package in a locked container and then sending it through a private courier service. The courier company knows where it’s going, but no one can peek inside the box;
- A proxy is like asking a friend to deliver your package for you. Your friend will certainly drop it off, but anyone watching can still see the package. You are just using them as a middleman to handle your mail.
What should I use?
Here’s a specific use case for Tor, a VPN, and a proxy.
Tor:
You want to access .onion websites while also protecting your online privacy on other websites.
Why Tor? .onion websites can only be accessed via the Tor browser. So, if you visit such websites frequently, you can use Tor as your default browser. It will allow you to access what you need and protect your privacy on any website you visit.
VPN:
You want privacy and security for all internet traffic, including browsers and apps.
Why a VPN? A VPN encrypts all traffic coming from your device; its protection is not limited to a specific browser or app. So, when using a VPN, you can rest assured that your online privacy is protected no matter what you do.
Tor over a VPN:
You want to ensure the best privacy protection for .onion websites.
Why Tor over a VPN? The dark web doesn’t exactly have a reputation as an online haven. If you want to use Tor for whistleblowing purposes or other sensitive activities on .onion websites, you need to use Tor over a VPN. It might slow down your connection significantly, but it’s the safest option available.
Proxy:
You want to change your IP but don’t need encryption to protect your privacy.
Why proxy? A proxy routes your traffic through a specific server and changes your IP. But it doesn’t encrypt your traffic, making proxy the least safe out of these options. Having a proxy server in your home country can be a great tool for accessing content and websites in your home country when traveling abroad.
You should assess your needs when deciding between Tor vs. a VPN, Tor over a VPN, or a proxy. Keep in mind that there’s a trade-off between safety and speed. The more you prioritize privacy, the slower your internet connection might become.
Alternative browsers to Tor
If you are concerned about your privacy but don’t want to use Tor because of its slow speeds or connections to the dark web, there are other privacy-focused, faster, and less controversial web browsers.
The Brave browser, for example, has probably the most default settings for privacy and security and offers optional onion routing. DuckDuckGo’s search engine and web browser are well known for their private search and the option to instantly close all tabs and delete browsing history. Epic Privacy Browser blocks ads, trackers, and fingerprinting and hides your IP.
These are just a few alternatives to the Tor browser. If you’d like to learn more, read our comprehensive guide on the best browsers for privacy.
Is Tor safe, or should I look for a different browser?
Using Tor is definitely safer than other mainstream browsers. But it’s far from a flawless solution for online privacy. In fact, just using a paid VPN usually provides better protection than Tor. If you really want to use Tor safely, you should do so by using Tor over a VPN instead of just running the browser on its own.
FAQ
Does Tor hide your IP?
Tor hides your IP from the website or service you want to access — whenever you request or send data on the internet, Tor encrypts it. However, the Tor entry node still sees your real IP (unless you use a VPN).
Is Tor anonymous?
The Tor browser is not 100% anonymous — it does hide your location and browsing activity, but the entry node knows your IP, and the exit node can see the data you’re sending. It doesn’t pose a risk unless the same entity owns both nodes.
Is the Tor Browser safe without a VPN?
Using Tor without a VPN isn’t always safe. Tor’s connections have some vulnerabilities at the entry and exit relays. If you use a VPN with Tor, these vulnerabilities are eliminated by the VPN’s encryption.
Is Tor illegal in the US?
Using the Tor browser is legal in the US, as well as Europe, and most other countries in the world. Its use is only illegal or restricted in Russia, China, Belarus, Iran, Saudi Arabia, and Turkey.