VPN(仮想プライベートネットワーク)は、ユーザーのインターネットトラフィックを暗号化し、IP (インターネットプロトコル)アドレスを秘匿するツールです。安全なネット接続を実現し、ユーザーのプライバシーを守ることができます。オンラインアクティビティを隠すことで、第三者に詮索されてデータを収集されないようにします。
VPN は、オンラインアクティビティのプライバシー保護、広告のブロック、トラッカーとマルウェアからの保護、同時にすべてのデバイスの保護が可能です。
VPN(仮想プライベートネットワーク)は、ユーザーのインターネットトラフィックを暗号化し、IP (インターネットプロトコル)アドレスを秘匿するツールです。安全なネット接続を実現し、ユーザーのプライバシーを守ることができます。オンラインアクティビティを隠すことで、第三者に詮索されてデータを収集されないようにします。
VPN は、オンラインアクティビティのプライバシー保護、広告のブロック、トラッカーとマルウェアからの保護、同時にすべてのデバイスの保護が可能です。
VPN は、ユーザーのトラフィックを暗号化することにより、さまざまなサイバー攻撃からユーザーを守ります。Wi-Fi スポットを利用する際は、ホームネットワークよりも脅威に晒されるリスクが高いため、特に役立ちます。
抑圧的な政府の中には、ネット利用を厳しく検閲しているところがあります。VPN を使用することで、こうした制約を乗り越え、世界に広がるインターネットの真髄にアクセスすることができます。
Surfshark は、安全な暗号化技術と厳格なノーログポリシーの組み合わせにより、広告主、インターネットサービスプロバイダー、ユーザーデータから利益を得ようとするその他の第三者から、ユーザーを守ります。
オンラインゲームでは、ネットサーフィンと同じくらい貴重なデータが大量に流出するおそれがあるため、VPN を使用して対策しましょう。ゲーム中も、データ流出、DDoS 攻撃、インターネットサービスプロバイダーによるスロットリングから、自分の身を守りましょう。
Webサイトは、ユーザーの位置情報やクッキーを使用して、商品やサービスの価格を調整しています。VPN を使用すれば、このようなマーケティング手法を回避し、オンラインショッピングの時に費用を節約することができます。
VPN は、お気に入りの番組をオンラインで視聴する際にプライバシーを守ってくれるだけでなく、インターネットサービスプロバイダーによるスロットリングを回避するのにも役立ちます。その結果、安全でバッファのない快適な視聴が可能になります。
もっと詳しく知りたいですか?VPN の利点に関する記事をお読みください!
VPN は、インターネットに到達する手前で VPN サーバー経由でトラフィックを送信することにより、データを暗号化し、IP アドレスを秘匿します。暗号化により、覗き見を試みる者や侵入を試みる第三者からユーザーデータを守ります。IP を変更することで、ユーザーは、自宅からではなく VPN サーバーの設置されている地域からアクセスしているように見えます。
VPN 経由でインターネットに接続すると、VPN サーバーにより、お手元のデバイスとインターネットの間に、安全な仮想トンネルが作られます。このトンネルを使用して、すべてのインターネットトラフィックが送信されます。
インターネットトラフィックが VPN トンネルを一度介すると、IPアドレスが変更されます。ユーザーがアクセスした Web サイトの側には、ユーザーの IP アドレスではなく VPN サーバーの IP アドレスが表示されます。
VPN はユーザーのあらゆるトラフィックを暗号化し、トンネリングの安全性を確保します。暗号化すると、ユーザーのデータはコードにより秘匿されるため、第三者はユーザーの機密情報にアクセスできなくなります。
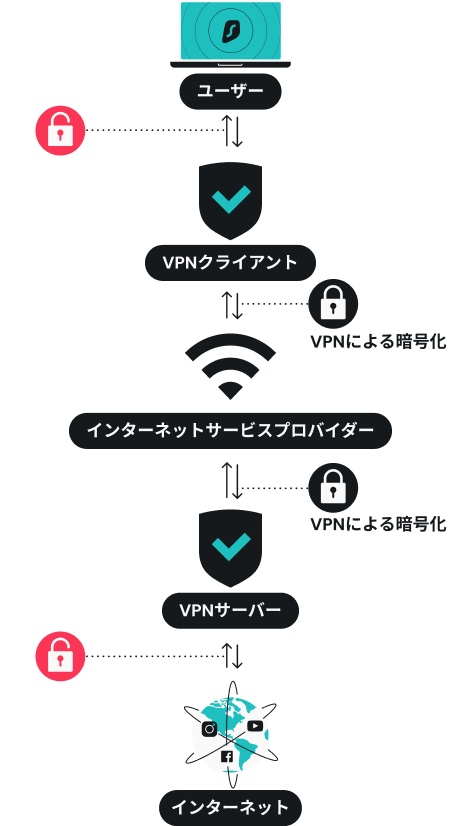
VPN トンネルは、安全な接続であり、お手元のデバイスとインターネットを繋ぎます。トンネリングはカプセル化 という技術を使用し、公衆インターネット上の VPN 通信を隠します。 このため、何者かがユーザーのネット接続を調べても、ユーザーが VPN を使用していることは分かるものの、ユーザーが何をしているかは分かりません。
ネット上のアクティビティを隠すだけでなく、VPN を使用していることも隠したくはありませんか?プライバシーのレベルをもう一段高めたいなら、難読化されたサーバーを使用できます。

VPN サーバーは、VPN ソフトウェアで構成された標準的なサーバーです。ユーザーのトラフィックは、インターネットに到達する手前で、まずサーバー経由でルーティングされます。これにより VPN は実際の IP アドレスを秘匿し、ユーザーデータを覗き見から守ることができます。

IP アドレスとは、ネットワーク間の通信を実現するためのデジタルラベルです。これは、ネットワーク内において、ユーザーとユーザーの居場所を識別するために用いられます。VPN は、ユーザーの IP アドレスを秘匿することで、Web サイトがユーザーに関する情報を収集することを防ぎます。

VPN は暗号化により、ユーザーのデータをエンコードし守ります。VPN クライアントとサーバーは、ユーザーが VPN に接続した際に、暗号キーを生成します。このキーは、データが暗号化されたトンネルを通過するたびに、データの暗号化と復号化に用いられます。キーを持っていない第三者にとっては、接続を試みても、暗号化されたデータは読み取り不能なままです。
暗号化のセキュリティは、使用される暗号で異なります。AES 256bit暗号は、最高の暗号化アルゴリズムと言われており、 米国政府やNSAをはじめとする信頼性の高いVPNサービスプロバイダが採用しており、Surfshark もこの暗号を採用しています。
ユーザーのIP アドレス、位置情報、訪れる Web サイトとそこで行うことなど、VPN はあらゆるインターネットトラフィックを隠して暗号化します。とはいえ VPN も、ソーシャルメディアへの投稿や Web サイトに登録する際にユーザーが自分から入力した情報など、開示することを選んだ情報まで隠すことはできません。
| これは隠せますか? | VPN の使用あり | VPN の使用なし |
| IP アドレス | 非公開 | 公開 |
| ロケーション | 非公開 | 公開 |
| 閲覧の習慣 | 非公開 | 公開 |
| インターネットトラフィック | 暗号化 | 公開 |
| 登録時に使用したEメール | 公開 | 公開 |
| 購入時に使用したクレジットカード情報 | 公開 | 公開 |
| Google アカウントにログインした状態でのグーグル検索 | 公開 | 公開 |
| ソーシャルメディアに掲載する情報 | 公開 | 公開 |
| ターゲット広告 | 最小限 | 非常に頻繁 |
いいえ、VPN では完全に匿名になりません。実際問題として、Web 上で完全に匿名になる方法はありません。しかし、VPN を使用すれば、オンラインでのプライバシー保護を大幅に強化できます。ネット利用の痕跡を完全に消し去ることはできないにしても、データを暗号化し IP を秘匿することで、追跡の魔の手からユーザーを守ります。
Surfshark のように最高水準の暗号と接続プロトコルを採用している VPN は極めて安全です。
ほぼすべてのセキュリティ対策が、突破されないよう、複雑な作りになっています。使用されているコンピュータで異なりますが、暗号化されたセッションの復号には、数百万年かかる場合があります。言うまでもなく、これはどの VPN セッションよりもはるかに長いです。
また仮に何者かが解読に成功したとしても、Surfshark のような多くの VPN プロバイダーは、PFS(Perfect Forward Secrecy)と呼ばれるものを実装しています。これは、約7分おきに VPN クライアントが新しいキーを生成し、ユーザーのプライベートなデータを悪意のある者から守ります。
VPN の種類には、ISO 認証の厳格な分類などはありませんが、現在、広く受け容れられている分類として以下のものがあります。
リモートアクセス VPN を使用すると、ユーザーは離れたネットワークに安全に接続できます。これにより、ユーザーは離れた場所からプライベートネットワークに安全にアクセスできます。在宅勤務が一般的になって以来、このタイプの VPN の人気が非常に高まっています。これは、リモートワークの従業員がネットワークに接続するにあたり、安全を確保できるためです。
サイト間 VPN は、イントラネットをネットワークに接続します。世界中にオフィスを構える大企業に役立ちます。オフィスのイントラネットが複数か所にまたがっている場合も、サイト間 VPN は、それらを単一のシームレスなネットワークに接続します。従業員は、設定したり、他のネットワークに接続したりすることなく、利用することができます。
パーソナル VPN は、個人ユーザー向けです。ユーザーを異なるネットワークに接続するのではなく、VPN サーバーに接続します。ユーザーがパーソナル VPN を経由して Web サイトやサービスにアクセスすると、トラフィックは、ホームネットワークではなく、VPN サーバーから来ているように見えます。Surfshark やその他の人気のある VPN のほとんどは、パーソナル VPN です。
VPN プロトコルは、ユーザーの VPN 接続が最初から最後までどのように機能するか決定するものです。また、VPN 接続の通信速度やセキュリティに影響を与えることがあります。相当数の VPN プロトコルが存在しますが、分かりやすいように、現時点で使用に適したものに限って、いくつかご紹介します。
OpenVPN は、高速安全で、様々なルーターに対応したオープンソースの VPN プロトコルです。オープン方式のため、世界中のサイバーセキュリティの専門家によりそのコードは徹底的に調査されています。信頼できる優れものですが、IKEV2 や WireGuard よりもパフォーマンスが劣る傾向があります。
対応している OS:Windows、macOS、Android、iOS、Linux、BSD。
Surfshark 対応:〇
Wireguard®は、わずか4,000行のコードでOpenVPN や IPSec を上回る電力使用量とパフォーマンスを実現するために作成され、比較的新しいプロトコルです。現状では、今日使用できる VPN プロトコルのなかで WireGuard が最速です。
対応している OS:Windows、macOS、Android、iOS、FreeBSD、NetBSD、OpenBSDなど。
Surfshark 対応:〇
Internet Key Exchange version 2(IKEv2)は、WireGuard と同等の品質です。ネットワーク切り替え時や短距離接続時に他のプロトコルを上回る速度を提供しているため、モバイルユーザーに人気があります。
対応している OS::macOS、Android、iOS、Linux、Blackberry、Unix など。
Surfshark 対応:〇
どちらもかなり旧式のトンネリングプロトコルで、避けるのが無難です。高速ではありますが、OpenVPN、IKEv2、WireGuard に匹敵するほどのセキュリティや信頼性はありません。
対応している OS:Windows、macOS、Android、iOS。
Surfshark 対応:×
SSTP は、VPN プロトコルではなくトンネリングプロトコルです。このため、OpenVPN、IKEv2、WireGuard のような機能はありません。比較的安全で使いやすいと考えられていますが、そのコードは一度も監査されたことがなく、Mac OS など他の OS での動作に問題があります。
対応している OS:Windows、Linux、BSD。
Surfshark 対応:×
Shadowsocksは、VPN プロトコルではなく、トンネリングプロキシです。しかし、VPN クライアント上のプロトコルとして実行することができます。中国のグレートファイアウォールを迂回することだけを目的に作成されました。速度が速くて検出されづらく、政府の検閲を回避する目的で使用できます。
対応している OS:Windows、macOS、Android、iOS、Linux。
Surfshark 対応:×
VPN が必要だと分かれば、次は、プロバイダーを選択する際に何に注意すればよいか、理解する必要があります。注意すべき重要なポイントは次のとおりです。
強力なVPNプロバイダーは、世界中の VPN サーバーをカバーしているべきです。これにより、より多くの場所から選択することができ、サーバーの負荷を軽減することができます。
安全なVPNの暗号化アルゴリズムは必須です。現在の業界標準である AES-256暗号を採用していることをご確認ください。
ユーザーの負荷を分散するために十分な数のサーバーがない場合、接続速度が低下して遅くなってしまいます。
プロトコルは、VPN のセキュリティに欠かせないもので、好みによってプロトコルを使い分けることができます。OpenVPN、IKEv2、WireGuard は今のところ VPN ゲームにとって最良の選択肢のひとつであるため、これらを運用しているサービスをお選びください。
マルチホップとは、複数のサーバーを同時に経由してトラフィックを誘導する VPN 機能のことです。これにより、保護機能はますます強化されますが、通信速度は遅くなります。これを使用することは必須ではないものの、オンラインセキュリティをさらに強化することができます。
難読化されたサーバー に接続すると、ユーザーのトラフィックは、通常のインターネットトラフィックのように見えます。これにより VPN ブロッカーを回避することができ、政府の抑圧的な検閲からユーザーを守ることができます。
VPN を購入する前に、セキュリティを確保したいデバイスに対応しているかどうかを確認してください。Surfshark は、iOS、macOS、Android、Windows、Linux など、主要なプラットフォームのすべてに対応しています。
RAM 専用サーバーは、あらゆる良質な VPN サービスの定番になりつつあります。RAM で動作している場合、サーバーの電源を切ると自動的にデータが消去されます。
厳格なプライバシーポリシーは、あらゆる VPN サービスの最重要要素のひとつです。VPN プロバイダーがプライバシーポリシーを持っていなかったり、明確な理由なく機密情報を記録していたりする場合は、直ちに危険信号です。
自分のニーズに合うVPN サブスクリプションのプランを選択し、アカウントを作成します。
お手元のデバイスにVPN アプリをインストールします。
アプリ上または手動で VPN に接続します。
設定中にサポートが必要な場合は、Surfshark ご利用開始に関するガイドをご覧ください。あらゆるプラットフォームで設定する詳細なガイドと、その他のお役立ち情報をご覧いただけます。
ホームネットワーク全体を保護したいですか?それならルーターに VPN を設定しましょう!ルーター1台を接続するだけで、VPN アプリをインストールしていないデバイスを含め、すべてのデバイスを保護でき、家族全員を守ることができます。